Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 771:
A security analyst recently implemented a new vulnerability scanning platform. The initial scan of 438 hosts found the following vulnerabilities:
210 critical 1,854 high 1,786 medium 48 low
The analyst is unsure how to handle such a large-scale remediation effort. Which of the following would be the next logical step?
A. Identify the assets with a high value and remediate all vulnerabilities on those hosts.
B. Perform remediation activities for all critical and high vulnerabilities first.
C. Perform a risk calculation to determine the probability and magnitude of exposure.
D. Identify the vulnerabilities that affect the most systems and remediate them first.
-
Question 772:
An analyst received an alert regarding an application spawning a suspicious command shell process. Upon further investigation, the analyst observes the following registry change occurring immediately after the suspicious event:
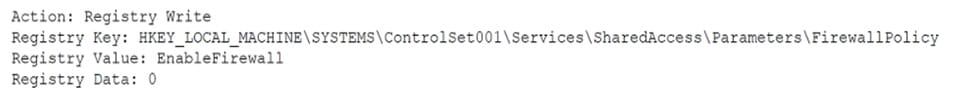
Which of the following was the suspicious event able to accomplish?
A. Impair defenses.
B. Establish persistence.
C. Bypass file access controls.
D. Implement beaconing.
-
Question 773:
An analyst is reviewing the following output:

Vulnerability found: Improper neutralization of script-related HTML tag Which of the following was most likely used to discover this?
A. Reverse engineering using a debugger
B. A static analysis vulnerability scan
C. A passive vulnerability scan
D. A database vulnerability scan
-
Question 774:
A security analyst discovers the following firewall log entries during an incident:
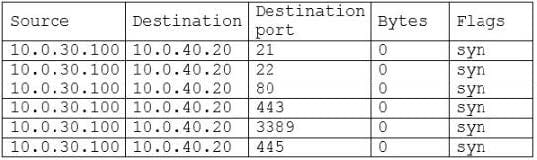
Which of the following is MOST likely occurring?
A. Banner grabbing
B. Port scanning
C. Beaconing
D. Data exfiltration
-
Question 775:
After an incident involving a phishing email, a security analyst reviews the following email access log:
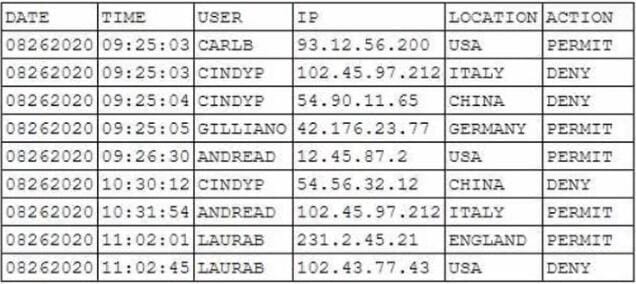
Based on this information, which of the following accounts was MOST likely compromised?
A. CARLB
B. CINDYP
C. GILLIANO
D. ANDREAD
E. LAURAB
-
Question 776:
A security analyst is revising a company's MFA policy to prohibit the use of short message service (SMS) tokens. The Chief Information Officer has questioned this decision and asked for justification. Which of the following should the analyst provide as justification for the new policy?
A. SMS relies on untrusted, third-party carrier networks.
B. SMS tokens are limited to eight numerical characters.
C. SMS is not supported on all handheld devices in use.
D. SMS is a cleartext protocol and does not support encryption.
-
Question 777:
A security analyst discovers a standard user has unauthorized access to the command prompt, PowerShell, and other system utilities. Which of the following is the BEST action for the security analyst to take?
A. Disable the appropriate settings in the administrative template of the Group Policy.
B. Use AppLocker to create a set of whitelist and blacklist rules specific to group membership.
C. Modify the registry keys that correlate with the access settings for the System32 directory.
D. Remove the user's permissions from the various system executables.
-
Question 778:
An organization's Chief Information Security Officer is creating a position that will be responsible for implementing technical controls to protect data, including ensuring backups are properly maintained. Which of the following roles would MOST likely include these responsibilities?
A. Data protection officer
B. Data owner
C. Backup administrator
D. Data custodian
E. Internal auditor
-
Question 779:
A security analyst who works in the SOC receives a new requirement to monitor for indicators of compromise. Which of the following is the first action the analyst should take in this situation?
A. Develop a dashboard to track the indicators of compromise.
B. Develop a query to search for the indicators of compromise.
C. Develop a new signature to alert on the indicators of compromise.
D. Develop a new signature to block the indicators of compromise.
-
Question 780:
During an incident response procedure, a security analyst acquired the needed evidence from the hard drive of a compromised machine. Which of the following actions should the analyst perform NEXT to ensure the data integrity of the evidence?
A. Generate hashes for each file from the hard drive.
B. Create a chain of custody document.
C. Determine a timeline of events using correct time synchronization.
D. Keep the cloned hard drive in a safe place.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.