Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 781:
An organization is concerned about the security posture of vendors with access to its facilities and systems. The organization wants to implement a vendor review process to ensure the policies implemented by vendors are in line with its own. Which of the following will provide the highest assurance of compliance?
A. An in-house red-team report
B. A vendor self-assessment report
C. An independent third-party audit report
D. Internal and external scans from an approved third-party vulnerability vendor
-
Question 782:
A manufacturing company has joined the information sharing and analysis center for its sector. As a benefit, the company will receive structured IoC data contributed by other members. Which of the following best describes the utility of this data?
A. Other members will have visibility into instances of positive IoC identification within the manufacturing company's corporate network.
B. The manufacturing company will have access to relevant malware samples from all other manufacturing sector members.
C. Other members will automatically adjust their security postures to defend the manufacturing company's processes.
D. The manufacturing company can ingest the data and use tools to autogenerate security configurations for all of its infrastructure.
-
Question 783:
A cybersecurity analyst is concerned about attacks that use advanced evasion techniques. Which of the following would best mitigate such attacks?
A. Keeping IPS rules up to date
B. Installing a proxy server
C. Applying network segmentation
D. Updating the antivirus software
-
Question 784:
While reviewing a vulnerability assessment, an analyst notices the following issue is identified in the report:
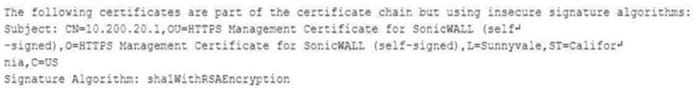
To address this finding, which of the following would be most appropriate for the analyst to recommend to the network engineer?
A. Reconfigure the device to support only connections leveraging TLSv1.2.
B. Obtain a new self-signed certificate and select AES as the hashing algorithm.
C. Replace the existing certificate with a certificate that uses only MDS for signing.
D. Use only signed certificates with cryptographically secure certificate sources.
-
Question 785:
An analyst needs to understand how an attacker compromised a server. Which of the following procedures will best deliver the information that is necessary to reconstruct the steps taken by the attacker?
A. Scan the affected system with an anti-malware tool and check for vulnerabilities with a vulnerability scanner.
B. Extract the server's system timeline, verifying hashes and network connections during a certain time frame.
C. Clone the entire system and deploy it in a network segment built for tests and investigations while monitoring the system during a certain time frame.
D. Clone the server's hard disk and extract all the binary files, comparing hash signatures with malware databases.
-
Question 786:
A new prototype for a company's flagship product was leaked on the internet. As a result, the management team has locked out all USB dives. Optical drive writers are not present on company computers. The sales team has been granted an exception to share sales presentation files with third parties. Which of the following would allow the IT team to determine which devices are USB enabled?
A. Asset tagging
B. Device encryption
C. Data loss prevention
D. SIEM logs
-
Question 787:
A security officer needs to find a solution to the current data privacy and protection gap found in the last security assessment. Which of the following is the most cost-effective solution?
A. Require users to sign NDAs.
B. Create a data minimization plan.
C. Add access control requirements.
D. Implement a data loss prevention solution.
-
Question 788:
A development team recently released a new version of a public-facing website for testing prior to production. The development team is soliciting the help of various teams to validate the functionality of the website due to its high visibility. Which of the following activities best describes the process the development team is initiating?
A. Static analysis
B. Stress testing
C. Code review
D. User acceptance testing
-
Question 789:
An organization is performing a risk assessment to prioritize resources for mitigation and remediation based on impact. Which of the following metrics, in addition to the CVSS for each CVE, would best enable the organization to prioritize is efforts?
A. OS type
B. OS or application versions
C. Patch availability
D. System architecture
E. Mission criticality
-
Question 790:
A security analyst s monitoring a company's network traffic and finds ping requests going to accounting and human resources servers from a SQL server. Upon investigation, the analyst discovers a technician responded to potential network connectivity issues. Which of the following is the best way for the security analyst to respond?
A. Report this activity as a false positive, as the activity is legitimate.
B. Isolate the system and begin a forensic investigation to determine what was compromised.
C. Recommend network segmentation to the management team as a way to secure the various environments.
D. Implement host-bases firewalls on all systems to prevent ping sweeps in the future.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.