Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 791:
A development team is discussing the implementation of parameterized queries to address several software vulnerabilities. Which of the following is the most likely type of vulnerability the team is trying to remediate?
A. SQL injection
B. CSRF
C. On-path attack
D. XSS
-
Question 792:
Which of the flowing is the best reason why organizations need operational security controls?
A. To supplement areas that other controls cannot address
B. To limit physical access to areas that contain sensitive data
C. To assess compliance automatically against a secure baseline
D. To prevent disclosure by potential insider threats
-
Question 793:
While observing several host machines, a security analyst notices a program is overwriting data to a buffer. Which of the following controls will best mitigate this issue?
A. Data execution prevention
B. Output encoding
C. Prepared statements
D. Parameterized queries
-
Question 794:
A security analyst is evaluating the following support ticket:
Issue: Marketing campaigns are being filtered by the customer's email servers.
Description: Our marketing partner cannot send emails using our email address. The following log messages were collected from multiple customers:
The SPF result is PermError.
The SPF result is SoftFail or Fail.
The 550 SPF check failed.
Which of the following should the analyst do next?
A. Ask the marketing partner's ISP to disable the DKIM setting.
B. Request approval to disable DMARC on the company's ISP.
C. Ask the customers to disable SPF validation.
D. Request a configuration change on the company's public DNS.
-
Question 795:
An application must pass a vulnerability assessment to move to the next gate. Consequently, any security issues that are found must be remediated prior to the next gate. Which of the following best describes the method for end-to-end vulnerability assessment?
A. Security regression testing
B. Static analysis
C. Dynamic analysis
D. Stress testing
-
Question 796:
Which of the following ICS network protocols has no inherent security functions on TCP port 502?
A. CIP
B. DHCP
C. SSH
D. Modbus
-
Question 797:
A Chief Information Officer wants to implement a BYOD strategy for all company laptops and mobile phones. The Chief Information Security Officer is concerned with ensuring all devices are patched and running some sort of protection against malicious software. Which of the following existing technical controls should a security analyst recommend to BEST meet all the requirements?
A. EDR
B. Port security
C. NAC
D. Segmentation
-
Question 798:
A security analyst receives a report indicating a system was compromised due to malware that was downloaded from the internet using TFTP. The analyst is instructed to block TFTP at the corporate firewall. Given the following portion of the current firewall rule set:
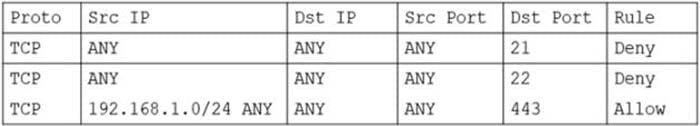
Which of the following rules should be added to accomplish this goal?
A. UDP ANY ANY ANY 20 Deny
B. UDP ANY ANY 69 69 Deny
C. UDP ANY ANY 67 68 Deny
D. UDP ANY ANY ANY 69 Deny
E. UDP ANY ANY ANY 69 Deny
-
Question 799:
A security analyst found the following entry in a server log:

The analyst executed netstat and received the following output: Which of the following lines in the output confirms this was successfully executed by the server?
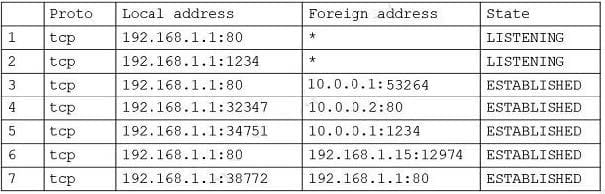
A. 1
B. 2
C. 3
D. 4
E. 5
F. 6
G. 7
-
Question 800:
Which of the following weaknesses associated with common SCADA systems are the MOST critical for organizations to address architecturally within their networks? (Choose two.)
A. Boot processes that are neither measured nor attested
B. Legacy and unpatchable systems software
C. Unnecessary open ports and protocols
D. No OS kernel mandatory access controls
E. Unauthenticated commands
F. Insecure filesystem permissions
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.