Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:509 Q&AsLast Updated
:Mar 31, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 161:
A security analyst is responding to an incident that involves a malicious attack on a network data closet. Which of the following best explains how the analyst should properly document the incident?
A. Back up the configuration file for all network devices.
B. Record and validate each connection.
C. Create a full diagram of the network infrastructure.
D. Take photos of the impacted items.
-
Question 162:
A cybersecurity analyst is participating with the DLP project team to classify the organization's data. Which of the following is the primary purpose for classifying data?
A. To identify regulatory compliance requirements
B. To facilitate the creation of DLP rules
C. To prioritize IT expenses
D. To establish the value of data to the organization
-
Question 163:
During an incident, a security analyst discovers a large amount of PII has been emailed externally from an employee to a public email address. The analyst finds that the external email is the employee's personal email. Which of the following should the analyst recommend be done first?
A. Place a legal hold on the employee's mailbox.
B. Enable filtering on the web proxy.
C. Disable the public email access with CASB.
D. Configure a deny rule on the firewall.
-
Question 164:
During an incident, some IoCs of possible ransomware contamination were found in a group of servers in a segment of the network. Which of the following steps should be taken next?
A. Isolation
B. Remediation
C. Reimaging
D. Preservation
-
Question 165:
An MSSP received several alerts from customer 1, which caused a missed incident response deadline for customer 2. Which of the following best describes the document that was violated?
A. KPI
B. SLO
C. SLA
D. MOU
-
Question 166:
A security analyst observed the following activities in chronological order:
1.
Protocol violation alerts on external firewall
2.
Unauthorized internal scanning activity
3.
Changes in outbound network performance
Which of the following best describes the goal of the threat actor?
A. Data exfiltration
B. Unusual traffic spikes
C. Rogue devices
D. Irregular peer-to-peer communication
-
Question 167:
A high volume of failed RDP authentication attempts was logged on a critical server within a one-hour period. All of the attempts originated from the same remote IP address and made use of a single valid domain user account. Which of the following would be the most effective mitigating control to reduce the rate of success of this brute-force attack?
A. Enabling a user account lockout after a limited number of failed attempts
B. Installing a third-party remote access tool and disabling RDP on all devices
C. Implementing a firewall block for the remote system's IP address
D. Increasing the verbosity of log-on event auditing on all devices
-
Question 168:
During an incident in which a user machine was compromised, an analyst recovered a binary file that potentially caused the exploitation. Which of the following techniques could be used for further analysis?
A. Fuzzing
B. Static analysis
C. Sandboxing
D. Packet capture
-
Question 169:
An analyst is reviewing system logs while threat hunting:
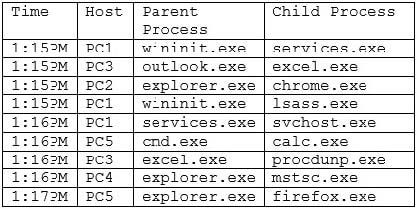
Which of the following hosts should be investigated first?
A. PC1 B. PC2
C. PC3
D. PC4
E. PC5
-
Question 170:
A web developer reports the following error that appeared on a development server when testing a new application:
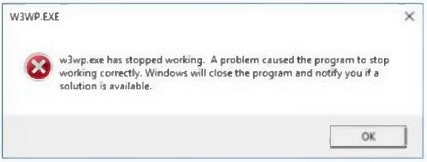
Which of the following tools can be used to identify the application's point of failure?
A. OpenVAS
B. Angry IP scanner
C. Immunity debugger
D. Burp Suite
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.