Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:556 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 191:
An organization has deployed a cloud-based storage system for shared data that is in phase two of the data life cycle. Which of the following controls should the security team ensure are addressed? (Choose two.)
A. Data classification
B. Data destruction
C. Data loss prevention
D. Encryption
E. Backups
F. Access controls
-
Question 192:
An analyst is conducting routine vulnerability assessments on the company infrastructure. When performing these scans, a business-critical server crashes, and the cause is traced back to the vulnerability scanner. Which of the following is the cause of this issue?
A. The scanner is running without an agent installed.
B. The scanner is running in active mode.
C. The scanner is segmented improperly
D. The scanner is configured with a scanning window
-
Question 193:
An organization's threat intelligence team notes a recent trend in adversary privilege escalation procedures. Multiple threat groups have been observed utilizing native Windows tools to bypass system controls and execute commands with privileged credentials. Which of the following controls would be most effective to reduce the rate of success of such attempts?
A. Set user account control protection to the most restrictive level on all devices
B. Implement MFA requirements for all internal resources
C. Harden systems by disabling or removing unnecessary services
D. Implement controls to block execution of untrusted applications
-
Question 194:
A new zero-day vulnerability was released. A security analyst is prioritizing which systems should receive deployment of compensating controls deployment first. The systems have been grouped into the categories shown below:
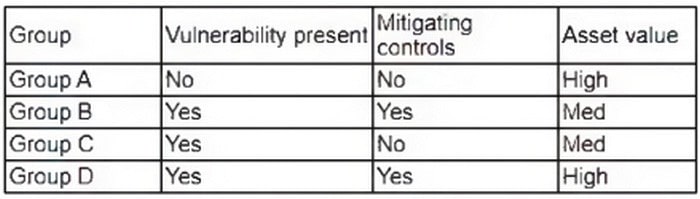
Which of the following groups should be prioritized for compensating controls?
A. Group A
B. Group B
C. Group C
D. Group D
-
Question 195:
A Chief Information Security Officer wants to map all the attack vectors that the company faces each day. Which of the following recommendations should the company align their security controls around?
A. OSSTMM
B. Diamond Model of Intrusion Analysis
C. OWASP
D. MITRE ATTandCK
-
Question 196:
Which of the following actions would an analyst most likely perform after an incident has been investigated?
A. Risk assessment
B. Root cause analysis
C. Incident response plan
D. Tabletop exercise
-
Question 197:
A recent audit of the vulnerability management program outlined the finding for increased awareness of secure coding practices. Which of the following would be best to address the finding?
A. Establish quarterly SDLC training on the top vulnerabilities for developers
B. Conduct a yearly inspection of the code repositories and provide the report to management.
C. Hire an external penetration test of the network
D. Deploy more vulnerability scanners for increased coverage
-
Question 198:
Which of the following best describes the process of requiring remediation of a known threat within a given time frame?
A. SLA
B. MOU
C. Best-effort patching
D. Organizational governance
-
Question 199:
Which of the following risk management principles is accomplished by purchasing cyber insurance?
A. Accept
B. Avoid
C. Mitigate
D. Transfer
-
Question 200:
An organization enabled a SIEM rule to send an alert to a security analyst distribution list when ten failed logins occur within one minute. However, the control was unable to detect an attack with nine failed logins. Which of the following best represents what occurred?
A. False positive
B. True negative
C. False negative
D. True positive
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.