Exam Details
Exam Code
:CAS-005Exam Name
:CompTIA SecurityXCertification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:261 Q&AsLast Updated
:Mar 31, 2025
CompTIA CompTIA Certifications CAS-005 Questions & Answers
-
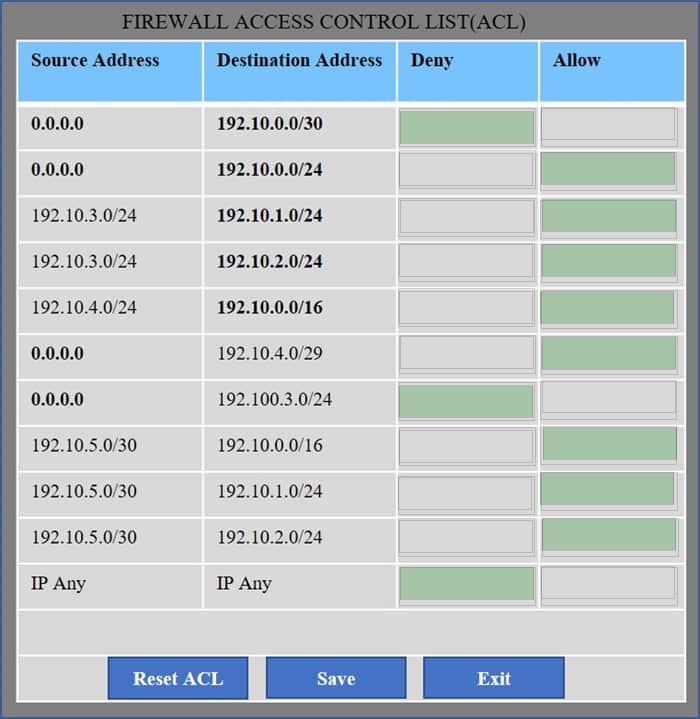
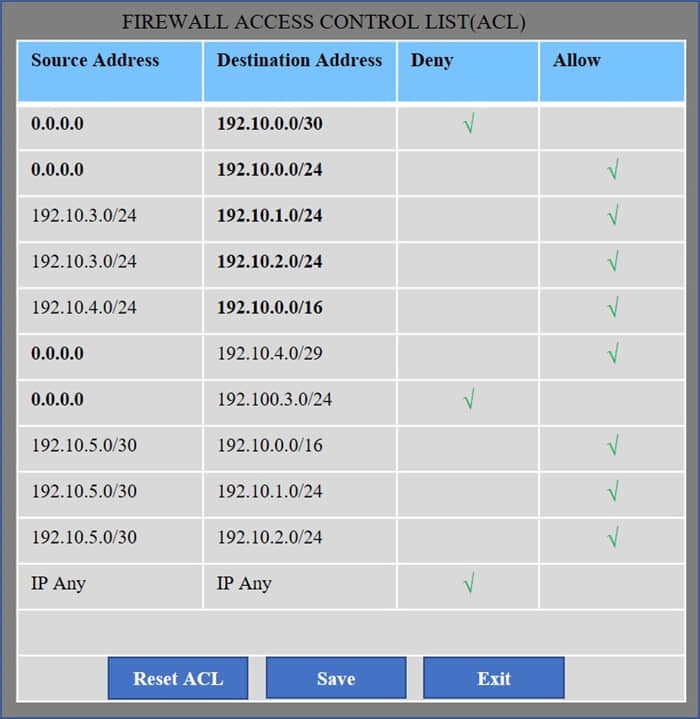
Question 191:
HOTSPOT
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP address. The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and 192.10.2.0/24 for the remote
site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.
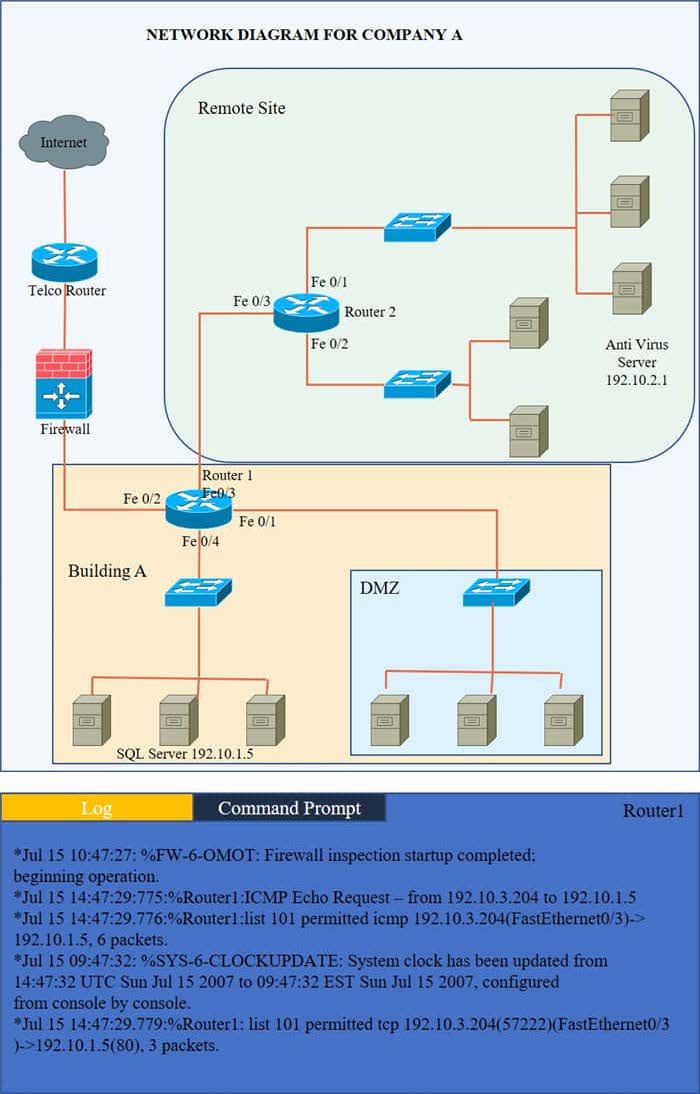
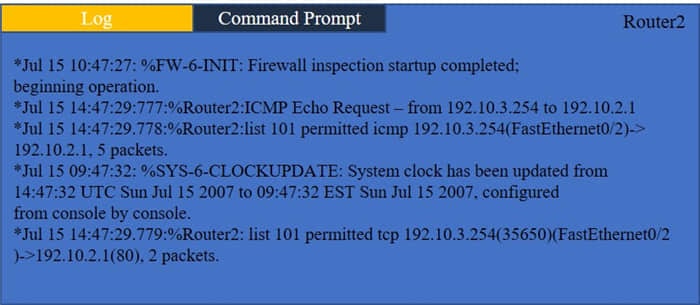
Hot Area:
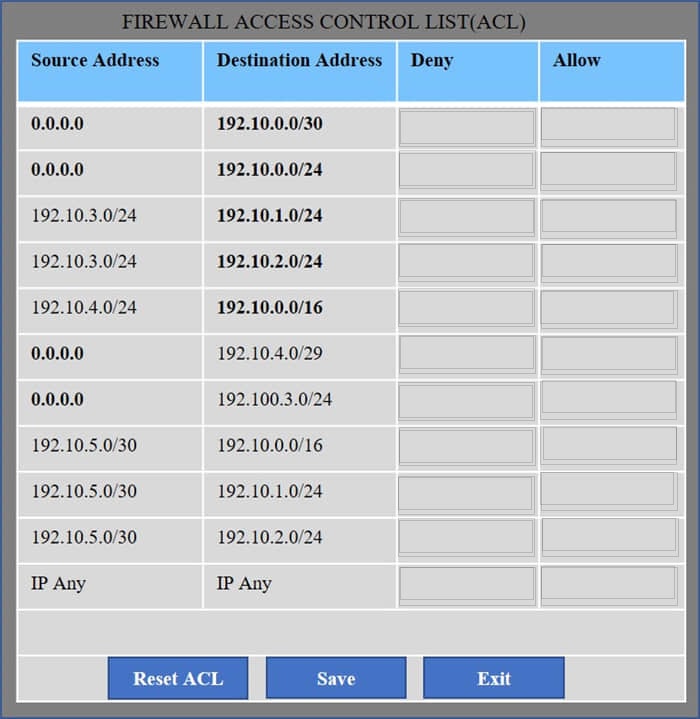
-
Question 192:
HOTSPOT
A product development team has submitted code snippets for review prior to release.
INSTRUCTIONS
Analyze the code snippets, and then select one vulnerability, and one fix for each code snippet.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Code Snippet 1
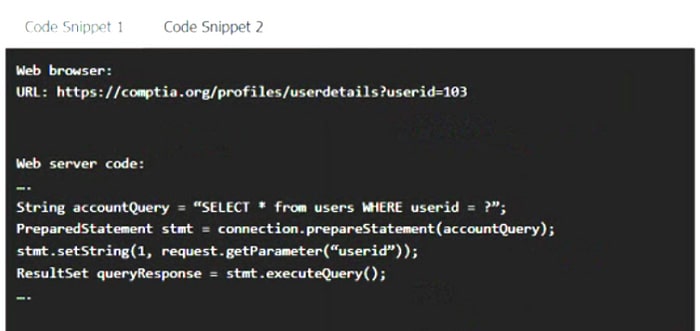
Code Snippet 2
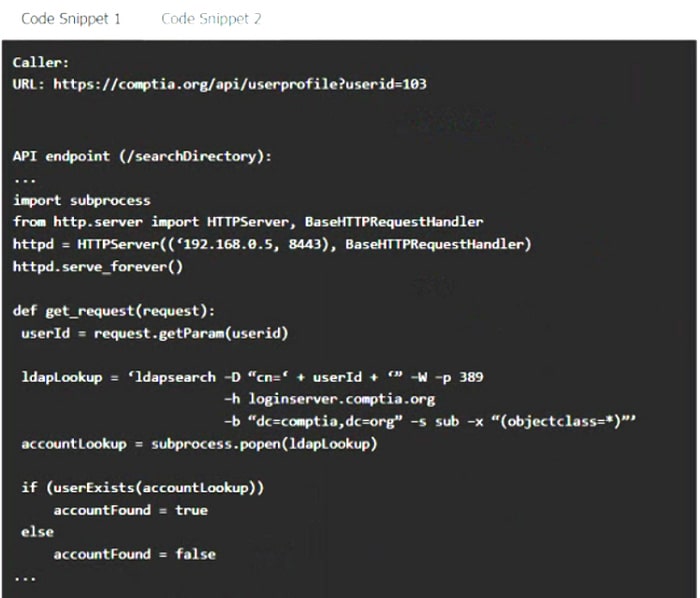
Hot Area:

-
Question 193:
An IT director is working on a solution to meet the challenge of remotely managing laptop devices and securely locking them down. The solution must meet the following requirements:
1.
Cut down on patch management.
2.
Make use of standard configurations.
3.
Allow for custom resource configurations.
4.
Provide access to the enterprise system from multiple types of devices.
Which of the following would meet these requirements?
A. MDM
B. Emulator
C. Hosted hypervisor
D. VDI
-
Question 194:
A security analyst received a report that a suspicious flash drive was picked up in the office's waiting area, located beyond the secured door. The analyst investigated the drive and found malware designed to harvest and transmit credentials. Security cameras in the area where the flash drive was discovered showed a vendor representative dropping the drive. Which of the following should the analyst recommend as an additional way to identify anyone who enters the building, in the event the camera system fails?
A. Employee badge logs
B. Phone call logs
C. Vehicle registration logs
D. Visitor logs
-
Question 195:
An IoT device implements an encryption module built within its SoC, where the asymmetric private key has been defined in a write-once read-many portion of the SoC hardware. Which of the following should the IoT manufacture do if the private key is compromised?
A. Use over-the-air updates to replace the private key.
B. Manufacture a new IoT device with a redesigned SoC.
C. Replace the public portion of the IoT key on its servers.
D. Release a patch for the SoC software.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-005 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.