Exam Details
Exam Code
:ECSAV10Exam Name
:EC-Council Certified Security Analyst (ECSA) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:354 Q&AsLast Updated
:Apr 02, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAV10 Questions & Answers
-
Question 141:
Which of the following will not handle routing protocols properly?
A. "Internet-router-firewall-net architecture"
B. "Internet-firewall-router-net architecture"
C. "Internet-firewall -net architecture"
D. "Internet-firewall/router(edge device)-net architecture"
-
Question 142:
Which of the following external pen testing tests reveals information on price, usernames and passwords, sessions, URL characters, special instructors, encryption used, and web page behaviors?
A. Check for Directory Consistency and Page Naming Syntax of the Web Pages
B. Examine Server Side Includes (SSI)
C. Examine Hidden Fields
D. Examine E-commerce and Payment Gateways Handled by the Web Server
-
Question 143:
ESTION NO: 92 In Linux, /etc/shadow file stores the real password in encrypted format for user's account with added properties associated with the user's password.
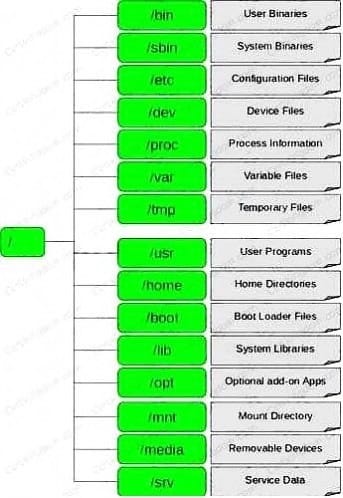
In the example of a /etc/shadow file below, what does the bold letter string indicate? Vivek: $1$fnffc$GteyHdicpGOfffXX40w#5:13064:0:99999:7
A. Number of days the user is warned before the expiration date
B. Minimum number of days required between password changes
C. Maximum number of days the password is valid
D. Last password changed
-
Question 144:
Which of the following is not a characteristic of a firewall?
A. Manages public access to private networked resources
B. Routes packets between the networks
C. Examines all traffic routed between the two networks to see if it meets certain criteria
D. Filters only inbound traffic but not outbound traffic
-
Question 145:
In which of the following firewalls are the incoming or outgoing packets blocked from accessing services for which there is no proxy?
A. Circuit level firewalls
B. Packet filters firewalls
C. Stateful multilayer inspection firewalls
D. Application level firewalls
-
Question 146:
Which of the following statements is true about Multi-Layer Intrusion Detection Systems (mIDSs)?
A. Decreases consumed employee time and increases system uptime
B. Increases detection and reaction time
C. Increases response time
D. Both Decreases consumed employee time and increases system uptime and Increases response time
-
Question 147:
An external intrusion test and analysis identify security weaknesses and strengths of the client's systems and networks as they appear from outside the client's security perimeter, usually from the Internet. The goal of an external intrusion test and analysis is to demonstrate the existence of known vulnerabilities that could be exploited by an external attacker.
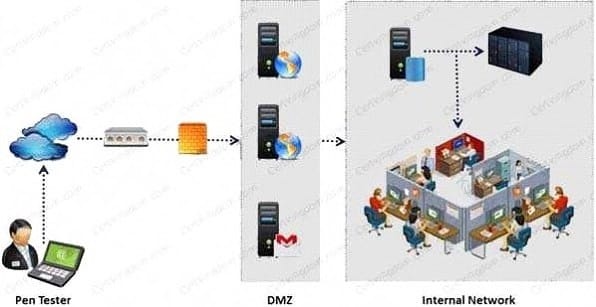
During external penetration testing, which of the following scanning techniques allow you to determine a port's state without making a full connection to the host?
A. XMAS Scan
B. SYN scan
C. FIN Scan
D. NULL Scan
-
Question 148:
Which of the following equipment could a pen tester use to perform shoulder surfing?
A. Binoculars
B. Painted ultraviolet material
C. Microphone
D. All the above
-
Question 149:
Transmission control protocol accepts data from a data stream, divides it into chunks, and adds a TCP header creating a TCP segment. The TCP header is the first 24 bytes of a TCP segment that contains the parameters and state of an end-to- end TCP socket. It is used to track the state of communication between two TCP endpoints. For a connection to be established or initialized, the two hosts must synchronize. The synchronization requires each side to send its own initial sequence number and to receive a confirmation of exchange in an acknowledgment (ACK) from the other side The below diagram shows the TCP Header format:
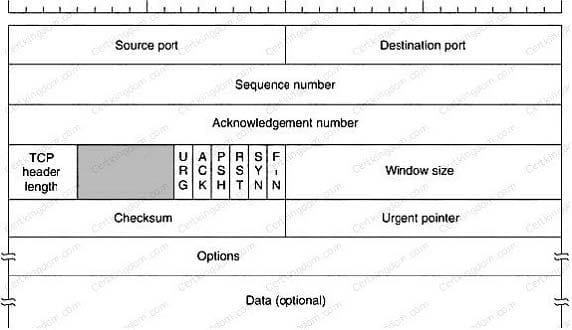
A. 16 bits
B. 32 bits
C. 8 bits
D. 24 bits
-
Question 150:
An automated electronic mail message from a mail system which indicates that the user does not exist on that server is called as?
A. SMTP Queue Bouncing
B. SMTP Message Bouncing
C. SMTP Server Bouncing
D. SMTP Mail Bouncing
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAV10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.