Exam Details
Exam Code
:ECSAV10Exam Name
:EC-Council Certified Security Analyst (ECSA) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:354 Q&AsLast Updated
:Apr 13, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAV10 Questions & Answers
-
Question 151:
You work as an IT security auditor hired by a law firm in Boston. You have been assigned the responsibility to audit the client for security risks. When assessing the risk to the clients network, what step should you take first?
A. Analyzing, categorizing and prioritizing resources
B. Evaluating the existing perimeter and internal security
C. Checking for a written security policy
D. Analyzing the use of existing management and control architecture
-
Question 152:
Today, most organizations would agree that their most valuable IT assets reside within applications and databases. Most would probably also agree that these are areas that have the weakest levels of security, thus making them the prime target for malicious activity from system administrators, DBAs, contractors, consultants, partners, and customers.
Which of the following flaws refers to an application using poorly written encryption code to securely encrypt and store sensitive data in the database and allows an attacker to steal or modify weakly protected data such as credit card numbers, SSNs, and other authentication credentials?
A. SSI injection attack
B. Insecure cryptographic storage attack
C. Hidden field manipulation attack
D. Man-in-the-Middle attack
-
Question 153:
A pen tester has extracted a database name by using a blind SQL injection. Now he begins to test the table inside the database using the below query and finds the table: http://juggyboy.com/page.aspx?id=1; IF (LEN(SELECT TOP 1 NAME from sysobjects where xtype='U')=3) WAITFOR DELAY '00:00:10'-http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),1,1)))=101) WAITFOR DELAY '00:00:10'-http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),2,1)))=109) WAITFOR DELAY '00:00:10'-http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),3,1)))=112) WAITFOR DELAY '00:00:10'-What is the table name?
A. CTS
B. QRT
C. EMP
D. ABC
-
Question 154:
You have compromised a lower-level administrator account on an Active Directory network of a small
company in Dallas, Texas. You discover Domain Controllers through enumeration. You connect to one of
the Domain Controllers on port 389 using Idp.exe.
What are you trying to accomplish here?
A. Poison the DNS records with false records
B. Enumerate MX and A records from DNS
C. Establish a remote connection to the Domain Controller
D. Enumerate domain user accounts and built-in groups
-
Question 155:
Identify the correct formula for Return on Investment (ROI).
A. ROI = ((Expected Returns - Cost of Investment) / Cost of Investment) * 100
B. ROI = (Expected Returns + Cost of Investment) / Cost of Investment
C. ROI = (Expected Returns Cost of Investment) / Cost of Investment
D. ROI = ((Expected Returns + Cost of Investment) / Cost of Investment) * 100
-
Question 156:
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants to hack
into his former company's network. Since Simon remembers some of the server names, he attempts to run
the AXFR and IXFR commands using DIG.
What is Simon trying to accomplish here?
A. Enumerate all the users in the domain
B. Perform DNS poisoning
C. Send DOS commands to crash the DNS servers
D. Perform a zone transfer
-
Question 157:
Identify the type of authentication mechanism represented below:
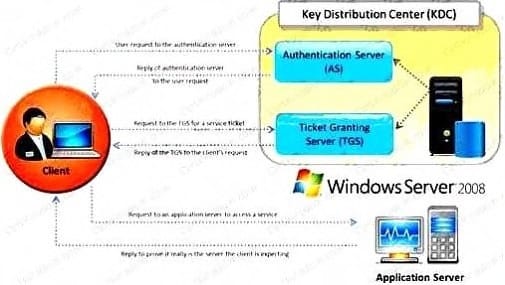
A. NTLMv1
B. NTLMv2
C. LAN Manager Hash
D. Kerberos
-
Question 158:
Wireshark is a network analyzer. It reads packets from the network, decodes them, and presents them in an easy-to- understand format. Which one of the following is the command-line version of Wireshark, which can be used to capture the live packets from the wire or to read the saved capture files?
A. Tcpdump
B. Capinfos
C. Tshark
D. Idl2wrs
-
Question 159:
Terri works for a security consulting firm that is currently performing a penetration test on First National Bank in Tokyo. Terri's duties include bypassing firewalls and switches to gain access to the network. Terri sends an IP packet to one of the company's switches with ACK bit and the source address of her machine set. What is Terri trying to accomplish by sending this IP packet?
A. Poison the switch's MAC address table by flooding it with ACK bits
B. Enable tunneling feature on the switch
C. Trick the switch into thinking it already has a session with Terri's computer
D. Crash the switch with a DoS attack since switches cannot send ACK bits
-
Question 160:
Windows stores user passwords in the Security Accounts Manager database (SAM), or in the Active Directory database in domains. Passwords are never stored in clear text; passwords are hashed and the results are stored in the SAM. NTLM and LM authentication protocols are used to securely store a user's password in the SAM database using different hashing methods.
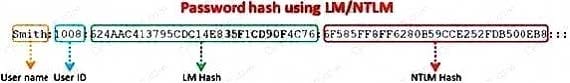
The SAM file in Windows Server 2008 is located in which of the following locations?
A. c:\windows\system32\config\SAM
B. c:\windows\system32\drivers\SAM
C. c:\windows\system32\Setup\SAM
D. c:\windows\system32\Boot\SAM
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAV10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.