Exam Details
Exam Code
:ECSAV10Exam Name
:EC-Council Certified Security Analyst (ECSA) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:354 Q&AsLast Updated
:Mar 24, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAV10 Questions & Answers
-
Question 21:
Which one of the following tools of trade is a commercial shellcode and payload generator written in Python by Dave Aitel?
A. Microsoft Baseline Security Analyzer (MBSA)
B. CORE Impact
C. Canvas
D. Network Security Analysis Tool (NSAT)
-
Question 22:
By default, the TFTP server listens on UDP port 69. Which of the following utility reports the port status of target TCP and UDP ports on a local or a remote computer and is used to troubleshoot TCP/IP connectivity issues?
A. PortQry
B. Netstat
C. Telnet
D. Tracert
-
Question 23:
SQL injection attacks are becoming significantly more popular amongst hackers and there has been an
estimated 69 percent increase of this attack type.
This exploit is used to great effect by the hacking community since it is the primary way to steal sensitive
data from web applications. It takes advantage of non-validated input vulnerabilities to pass SQL
commands through a web application for execution by a back-end database.
The below diagram shows how attackers launched SQL injection attacks on web applications.
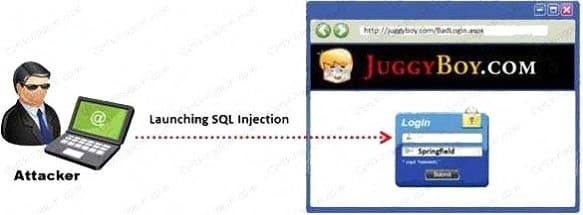
Which of the following can the attacker use to launch an SQL injection attack?
A. Blah' "2=2 -"
B. Blah' and 2=2 -
C. Blah' and 1=1 -
D. Blah' or 1=1 -
-
Question 24:
The framework primarily designed to fulfill a methodical and organized way of addressing five threat classes to network and that can be used to access, plan, manage, and maintain secure computers and communication networks is:
A. Nortells Unified Security Framework
B. The IBM Security Framework
C. Bell Labs Network Security Framework
D. Microsoft Internet Security Framework
-
Question 25:
Many security and compliance projects begin with a simple idea: assess the organization's risk, vulnerabilities, and breaches. Implementing an IT security risk assessment is critical to the overall security posture of any organization. An effective security risk assessment can prevent breaches and reduce the impact of realized breaches.
What is the formula to calculate risk?
A. Risk = Budget x Time
B. Risk = Goodwill x Reputation
C. Risk = Loss x Exposure factor
D. Risk = Threats x Attacks
-
Question 26:
Which of the following approaches to vulnerability assessment relies on the administrator providing baseline of system configuration and then scanning continuously without incorporating any information found at the time of scanning?

A. Service-based Assessment Solutions
B. Product-based Assessment Solutions
C. Tree-based Assessment
D. Inference-based Assessment
-
Question 27:
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast. On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently. What could be Tyler issue with his home wireless network?
A. 2.4 Ghz Cordless phones
B. Satellite television
C. CB radio
D. Computers on his wired network
-
Question 28:
Besides the policy implications of chat rooms, Internet Relay Chat (IRC) is frequented by attackers and used as a command and control mechanism. IRC normally uses which one of the following TCP ports?
A. 6566 TCP port
B. 6771 TCP port
C. 6667 TCP port
D. 6257 TCP port
-
Question 29:
Kyle is performing the final testing of an application he developed for the accounting department. His last
round of testing is to ensure that the program is as secure as possible. Kyle runs the following command.
What is he testing at this point?
include
#include
int main(int argc, char *argv[])
{
char buffer[10];
if (argc < 2)
{
fprintf(stderr, "USAGE: %s string\n", argv[0]);
return 1;
}
strcpy(buffer, argv[1]);
return 0;
}
A. Buffer overflow
B. Format string bug
C. Kernal injection
D. SQL injection
-
Question 30:
A WHERE clause in SQL specifies that a SQL Data Manipulation Language (DML) statement should only affect rows that meet specified criteria; The criteria are expressed in the form of predicates. WHERE clauses are not mandatory clauses of SQL DML statements, but can be used to limit the number of rows affected by a SQL DML statement or returned by a query.
A pen tester is trying to gain access to a database by inserting exploited query statements with a WHERE
clause. The pen tester wants to retrieve all the entries from the database using the WHERE clause from a
particular table (e.g.
StudentTable).
What query does he need to write to retrieve the information?
A. EXTRACT* FROM StudentTable WHERE roll_number = 1 order by 1000
B. DUMP * FROM StudentTable WHERE roll_number = 1 AND 1=1-
C. SELECT * FROM StudentTable WHERE roll_number = '' or '1' = '1`
D. RETRIVE * FROM StudentTable WHERE roll_number = 1'#
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAV10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.