Exam Details
Exam Code
:ECSAV10Exam Name
:EC-Council Certified Security Analyst (ECSA) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:354 Q&AsLast Updated
:Mar 24, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAV10 Questions & Answers
-
Question 31:
After passing her CEH exam, Carol wants to ensure that her network is completely secure. She
implements a DMZ, statefull firewall, NAT, IPSEC, and a packet filtering firewall. Since all security
measures were taken, none of the hosts on her network can reach the Internet.
Why is that?
A. IPSEC does not work with packet filtering firewalls
B. NAT does not work with IPSEC
C. NAT does not work with statefull firewalls
D. Statefull firewalls do not work with packet filtering firewalls
-
Question 32:
Paulette works for an IT security consulting company that is currently performing an audit for the firm ACE Unlimited. Paulette's duties include logging on to all the company's network equipment to ensure IOS versions are up-to-date and all the other security settings are as stringent as possible. Paulette presents the following screenshot to her boss so he can inform the clients about necessary changes need to be made. From the screenshot, what changes should the client company make? Exhibit:
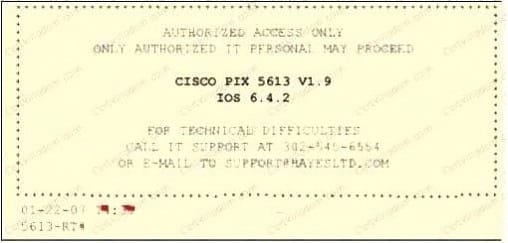
A. The banner should not state "only authorized IT personnel may proceed"
B. Remove any identifying numbers, names, or version information
C. The banner should include the Cisco tech support contact information as well
D. The banner should have more detail on the version numbers for the network equipment
-
Question 33:
Which of the following policies helps secure data and protects the privacy of organizational information?
A. Special-Access Policy
B. Document retention Policy
C. Cryptography Policy
D. Personal Security Policy
-
Question 34:
How many bits is Source Port Number in TCP Header packet?
A. 48
B. 32
C. 64
D. 16
-
Question 35:
What is a good security method to prevent unauthorized users from "tailgating"?
A. Electronic key systems
B. Man trap
C. Pick-resistant locks
D. Electronic combination locks
-
Question 36:
When you are running a vulnerability scan on a network and the IDS cuts off your connection, what type of IDS is being used?
A. Passive IDS
B. Active IDS
C. Progressive IDS
D. NIPS
-
Question 37:
Mason is footprinting an organization to gather competitive intelligence. He visits the company's website for contact information and telephone numbers but does not find any. He knows the entire staff directory was listed on their website 12 months. How can he find the directory?
A. Visit Google's search engine and view the cached copy
B. Crawl and download the entire website using the Surfoffline tool and save them to his computer
C. Visit the company's partners' and customers' website for this information
D. Use Way Back Machine in Archive.org web site to retrieve the Internet archive
-
Question 38:
NTP protocol is used to synchronize the system clocks of computers with a remote time server or time source over a network. Which one of the following ports is used by NTP as its transport layer?
A. TCP port 152
B. UDP port 177
C. UDP port 123
D. TCP port 113
-
Question 39:
Which one of the following is a command line tool used for capturing data from the live network and copying those packets to a file?
A. Wireshark: Capinfos
B. Wireshark: Tcpdump
C. Wireshark: Text2pcap
D. Wireshark: Dumpcap
-
Question 40:
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.
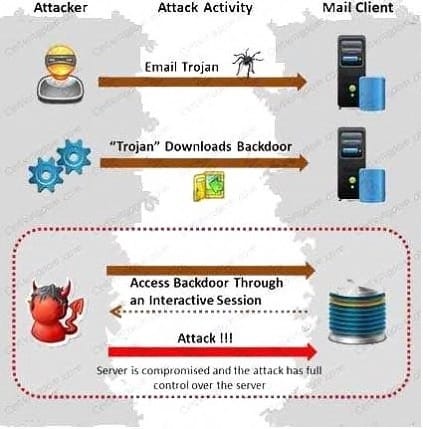
Which of the following techniques do attackers use to create backdoors to covertly gather critical information about a target machine?
A. Internal network mapping to map the internal network of the target machine
B. Port scanning to determine what ports are open or in use on the target machine
C. Sniffing to monitor all the incoming and outgoing network traffic
D. Social engineering and spear phishing attacks to install malicious programs on the target machine
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAV10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.