Exam Details
Exam Code
:ECSAV10Exam Name
:EC-Council Certified Security Analyst (ECSA) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:354 Q&AsLast Updated
:Mar 24, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAV10 Questions & Answers
-
Question 321:
George, a freelance Security Auditor and Penetration Tester, was working on a pen testing assignment for Xsecurity. George is an ESCA certified professional and was following the LPT methodology in performing a comprehensive security assessment of the company. After the initial reconnaissance, scanning and enumeration phases, he successfully recovered a user password and was able to log on to a Linux machine located on the network. He was also able to access the / etc/passwd file; however, the passwords were stored as a single "x" character.
What will George do to recover the actual encrypted passwords?
A. George will perform sniffing to capture the actual passwords
B. George will perform replay attack to collect the actual passwords
C. George will escalate his privilege to root level and look for /etc/shadow file
D. George will perform a password attack using the pre-computed hashes also known as a rainbow attack
-
Question 322:
An attacker targeted to attack network switches of an organization to steal confidential information such as
network subscriber information, passwords, etc. He started transmitting data through one switch to another
by creating and sending two 802.1Q tags, one for the attacking switch and the other for victim switch. By
sending these frames. The attacker is fooling the victim switch into thinking that the frame is intended for it.
The target switch then forwards the frame to the victim port.
Identify the type of attack being performed by the attacker?
A. SNMP brute forcing
B. MAC flooding
C. IP spoofing
D. VLAN hopping
-
Question 323:
Joe, an ECSA certified professional, is working on a pen testing engagement for one of his SME clients. He discovered the host file in one of the Windows machines has the following entry:
213.65.172.55 microsoft.com
After performing a Whois lookup, Joe discovered the IP does not refer to Microsoft.com. The network
admin denied modifying the host files.
Which type of attack does this scenario present?
A. DNS starvation
B. DNS poisoning
C. Phishing
D. MAC spoofing
-
Question 324:
The Rhythm Networks Pvt Ltd firm is a group of ethical hackers. Rhythm Networks was asked by their client Zombie to identify how the attacker penetrated their firewall. Rhythm discovered the attacker modified the addressing information of the IP packet header and the source address bits field to bypass the firewall. What type of firewall bypassing technique was used by the attacker?
A. Source routing
B. Proxy Server
C. HTTP Tunneling
D. Anonymous Website Surfing Sites
-
Question 325:
Todd is working on an assignment involving auditing of a web service. The scanning phase reveals the
web service is using an Oracle database server at the backend. He wants to check the TNS Listener
configuration file for configuration errors.
Which of the following directories contains the TNS Listener configuration file, by default:
A. $ORACLE_HOME/bin
B. $ORACLE_HOME/network /admin
C. $ORACLE_HOME/network /bin
D. $ORACLE_HOME/network
-
Question 326:
Cedric, who is a software support executive working for Panacx Tech. Inc., was asked to install Ubuntu operating system in the computers present in the organization. After installing the OS, he came to know that there are many unnecessary services and packages in the OS that were automatically installed without his knowledge. Since these services or packages can be potentially harmful and can create various security threats to the host machine, he was asked to disable all the unwanted services. In order to stop or disable these unnecessary services or packages from the Ubuntu distributions, which of the following commands should Cedric employ?
A. # update-rc.d -f [service name] remove
B. # chkconfig [service name] –del
C. # chkconfig [service name] off
D. # service [service name] stop
-
Question 327:
A team of cyber criminals in Germany has sent malware-based emails to workers of a fast-food center which is having multiple outlets spread geographically. When any of the employees click on the malicious email, it will give backdoor access to the point of sale (POS) systems located at various outlets. After gaining access to the POS systems, the criminals will be able to obtain credit card details of the fast-food center's customers. In the above scenario, identify the type of attack being performed on the fast-food center?
A. Phishing
B. Vishing
C. Tailgating
D. Dumpster diving
-
Question 328:
As a part of the pen testing process, James performs a FIN scan as given below:
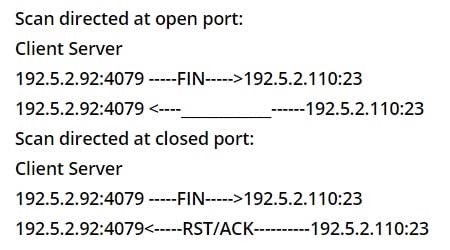
What will be the response if the port is open?
A. No response
B. FIN/RST
C. FIN/ACK
D. RST
-
Question 329:
Peter works as a lead penetration tester in a security service firm named Xsecurity. Recently, Peter was assigned a white-box pen test assignment testing the security of an IDS system deployed by a client. During the preliminary information gathering, Peter discovered the TTL to reach the IDS system from his end is 30. Peter created a Trojan and fragmented it in to 1-character packets using the Colasoft packet builder tool. He then used a packet flooding utility to bombard the IDS with these fragmented packets with the destination address of a target host behind the IDS whose TTL is 35. What is Peter trying to achieve?
A. Peter is trying to bypass the IDS system using a Trojan
B. Peter is trying to bypass the IDS system using the broadcast address
C. Peter is trying to bypass the IDS system using the insertion attack
D. Peter is trying to bypass the IDS system using inconsistent packets
-
Question 330:
While scanning a server, you found rpc, nfs and mountd services running on it. During the investigation, you were told that NFS Shares were mentioned in the /etc/exports list of the NFS server. Based on this information, which among the following commands would you issue to view the NFS Shares running on the server?
A. showmount
B. nfsenum
C. mount
D. rpcinfo
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAV10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.