Exam Details
Exam Code
:ECSAV10Exam Name
:EC-Council Certified Security Analyst (ECSA) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:354 Q&AsLast Updated
:Mar 24, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAV10 Questions & Answers
-
Question 331:
SecGlobal Corporation hired Michael, a penetration tester. Management asked Michael to perform cloud penetration testing on the company's cloud infrastructure. As a part of his task, he started checking all the agreements with cloud service provider and came to a conclusion that it is not possible to perform penetration testing on the cloud services that are being used by the organization due to the level of responsibilities between company and the Cloud Service Provider (CSP). Identify the type of cloud service deployed by the organization?
A. Platform as a service (PaaS)
B. Software as a service (SaaS)
C. Anything as a service (XaaS)
D. Infrastructure as a service (IaaS)
-
Question 332:
Alisa is a Network Security Manager at Aidos Cyber Security. During a regular network audit, she sent
specially crafted ICMP packet fragments with different offset values into the network, causing a system
crash.
Which attack Alisa is trying to perform?
A. Ping-of-death attack
B. Fraggle attack
C. Session hijacking
D. Smurf attack
-
Question 333:
Which of the following roles of Microsoft Windows Active Directory refers to the ability of an active directory to transfer roles to any domain controller (DC) in the enterprise?
A. Master Browser (MB)
B. Global Catalog (GC)
C. Flexible Single Master Operation (FSMO)
D. Rights Management Services (RMS)
-
Question 334:
A user unknowingly installed a fake malicious banking app in his Android mobile. This app includes a configuration file that consists of phone numbers of the bank. When the user makes a call to the bank, he is automatically redirected to the number being used by the attacker. The attacker impersonates as a banking official. Also, the app allows the attacker to call the user, then the app displays fake caller ID on the user's mobile resembling call from a legitimate bank. Identify the attack being performed on the Android mobile user?
A. Tailgating
B. SMiShing
C. Vishing
D. Eavesdropping
-
Question 335:
How does OS Fingerprinting help you as a pen tester?
A. It defines exactly what software the target has installed
B. It doesn't depend on the patches that have been applied to fix existing security holes
C. It opens a security-delayed window based on the port being scanned
D. It helps to research vulnerabilities that you can use to exploit on a target system
-
Question 336:
The penetration testing team of MirTech Inc. identified the presence of various vulnerabilities in the web application coding. They prepared a detailed report addressing to the web developers regarding the findings. In the report, the penetration testing team advised the web developers to avoid the use of dangerous standard library functions. They also informed the web developers that the web application copies the data without checking whether it fits into the target destination memory and is susceptible in supplying the application with large amount of data. According to the findings by the penetration testing team, which type of attack was possible on the web application?
A. Buffer overflow
B. SQL injection
C. Cross-site scripting
D. Denial-of-service
-
Question 337:
An organization has deployed a web application that uses encoding technique before transmitting the data over the Internet. This encoding technique helps the organization to hide the confidential data such as user credentials, email attachments, etc. when in transit. This encoding technique takes 3 bytes of binary data and divides it into four chunks of 6 bits. Each chunk is further encoded into respective printable character. Identify the encoding technique employed by the organization?
A. Unicode encoding
B. Base64 encoding
C. URL encoding
D. HTMS encoding
-
Question 338:
During an internal network audit, you are asked to see if there is any RPC server running on the network and if found, enumerate the associate RPC services. Which port would you scan to determine the RPC server and which command will you use to enumerate the RPC services?
A. Port 111, rpcinfo
B. Port 111, rpcenum
C. Port 145, rpcinfo
D. Port 145, rpcenum
-
Question 339:
James is an attacker who wants to attack XYZ Inc. He has performed reconnaissance over all the publicly available resources of the company and identified the official company website http://xyz.com. He scanned all the pages of the company website to find for any potential vulnerabilities to exploit. Finally, in the user account login page of the company's website, he found a user login form which consists of several fields that accepts user inputs like username and password. He also found than any non-validated query that is requested can be directly communicated to the active directory and enable unauthorized users to obtain direct access to the databases. Since James knew an employee named Jason from XYZ Inc., he enters a valid username "jason" and injects "jason)(and))" in the username field. In the password field, James enters "blah" and clicks Submit button. Since the complete URL string entered by James becomes "(and (USER=jason)(and))(PASS=blah))," only the first filter is processed by the Microsoft Active Directory, that is, the query "(and(USER=jason)(and))" is processed. Since this query always stands true, James successfully logs into the user account without a valid password of Jason. In the above scenario, identify the type of attack performed by James?
A. LDAP injection attack
B. HTML embedding attack
C. Shell injection attack
D. File injection attack
-
Question 340:
Richard is working on a web app pen testing assignment for one of his clients. After preliminary
information, gathering and vulnerability scanning Richard runs the SQLMAP tool to extract the database
information.
Which of the following commands will give Richard an output as shown in the screenshot?
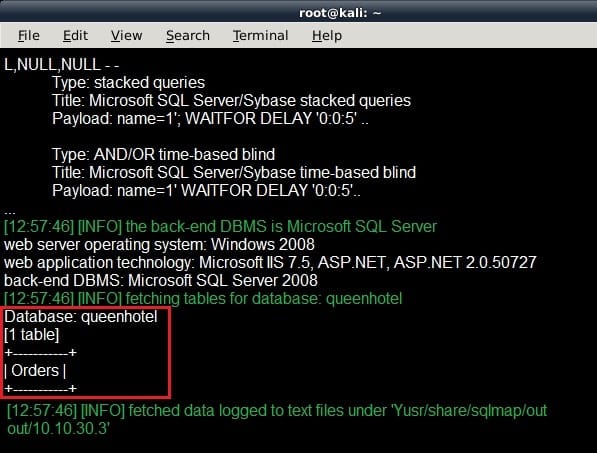
A. sqlmap –url http://quennhotel.com/about.aspx?name=1 –D queenhotel --tables
B. sqlmap –url http://quennhotel.com/about.aspx?name=1 –dbs
C. sqlmap –url http://quennhotel.com/about.aspx?name=1 –D queenhotel –T --columns
D. sqlmap –url http://quennhotel.com/about.aspx?name=1 –database queenhotel –tables
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAV10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.