Exam Details
Exam Code
:HPE6-A84Exam Name
:Aruba Certified Network Security Expert WrittenCertification
:HP CertificationsVendor
:HPTotal Questions
:60 Q&AsLast Updated
:Mar 09, 2025
HP HP Certifications HPE6-A84 Questions & Answers
-
Question 11:
A customer wants CPPM to authenticate non-802.1X-capable devices. An admin has created the service shown in the exhibits below: What is one recommendation to improve security?
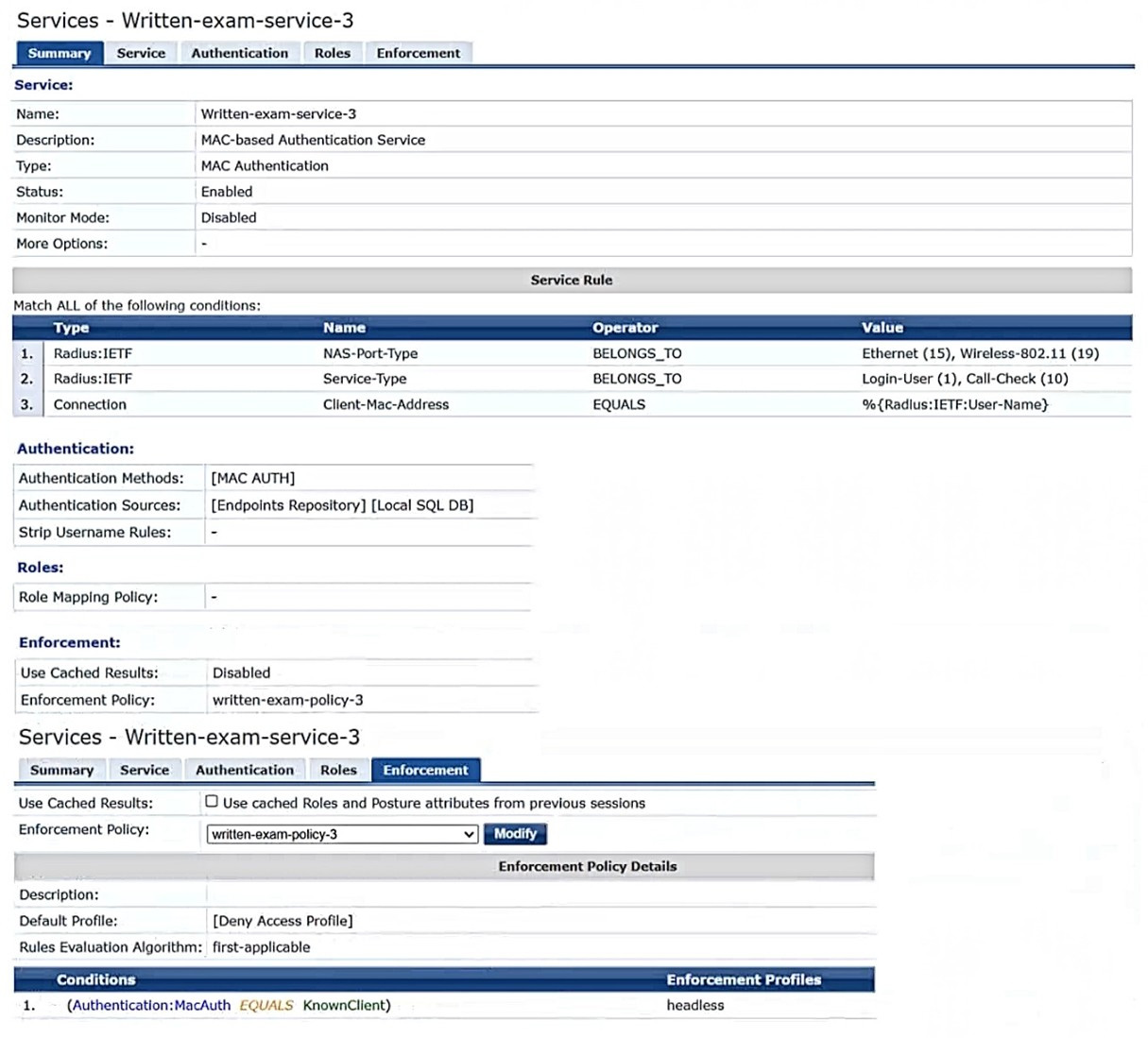
A. Adding an enforcement policy rule that denies access to endpoints with the Conflict flaq
B. Using Active Directory as the authentication source
C. Creating and using a custom MAC-Auth authentication method
D. Enabling caching of posture and roles
-
Question 12:
Refer to the exhibit.
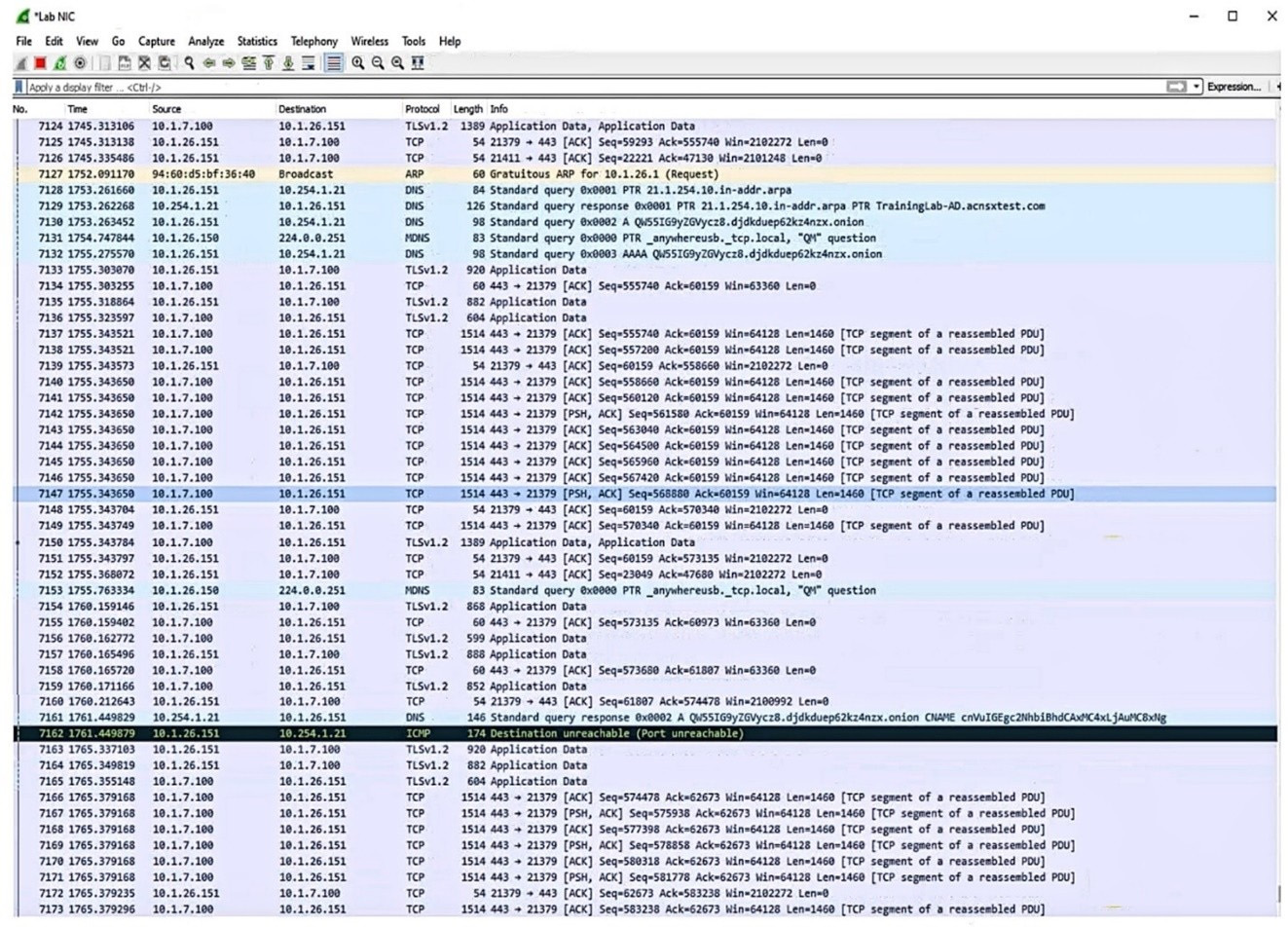
Which security issue is possibly indicated by this traffic capture?
A. An attempt at a DoS attack by a device acting as an unauthorized DNS server
B. A port scan being run on the 10.1.7.0/24 subnet
C. A command and control channel established with DNS tunneling
D. An ARP poisoning or man-in-the-middle attempt by the device at 94:60:d5:bf:36:40
-
Question 13:
A customer requires a secure solution for connecting remote users to the corporate main site. You are designing a client-to-site virtual private network (VPN) based on Aruba VIA and Aruba Mobility Controllers acting as VPN Concentrators (VPNCs). Remote users will first use the VIA client to contact the VPNCs and obtain connection settings.
The users should only be allowed to receive the settings if they are the customer's "RemoteEmployees" AD group. After receiving the settings, the VIA clients will automatically establish VPN connections, authenticating to CPPM with certificates.
What should you do to help ensure that only authorized users obtain VIA connection settings?
A. Set up the VPNCs' VIA web authentication profile to use CPPM as the authentication server; set up a service on CPPM that uses AD as the authentication source.
B. Set up the VPNCs' VIA web authentication profile to use an AD domain controller as the LDAP server.
C. Set up the VPNCs' VIA connection profile to use two authentication profiles, one RADIUS profile to CPPM and one LDAP profile to AD.
D. Set up the VPNCs' VIA connection profile to use one authentication profile, which is set to the AD domain controller's hostname.
-
Question 14:
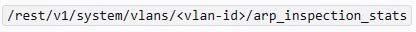
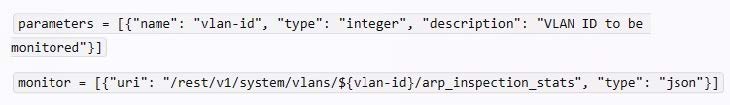
You are working with a developer to design a custom NAE script for a customer. The NAE agent should trigger an alert when ARP inspection drops packets on a VLAN. The customer wants the admins to be able to select the correct VLAN ID for the agent to monitor when they create the agent.
What should you tell the developer to do?
A. Use this variable, %{vlan-id} when defining the monitor URI in the NAE agent script.
B. Define a VLAN ID parameter; reference that parameter when defining the monitor URI.
C. Create multiple monitors within the script from which admins can select when they create the agent.
D. Use a callback action to collect the ID of the VLAN on which admins have enabled NAE monitoring.
-
Question 15:
Refer to the scenario.
A customer has an Aruba ClearPass cluster. The customer has AOS-CX switches that implement 802.1X authentication to ClearPass Policy Manager (CPPM).
Switches are using local port-access policies.
The customer wants to start tunneling wired clients that pass user authentication only to an Aruba gateway cluster. The gateway cluster should assign these clients to the "eth- internet" role. The gateway should also handle assigning clients
to their VLAN, which is VLAN 20.
The plan for the enforcement policy and profiles is shown below:
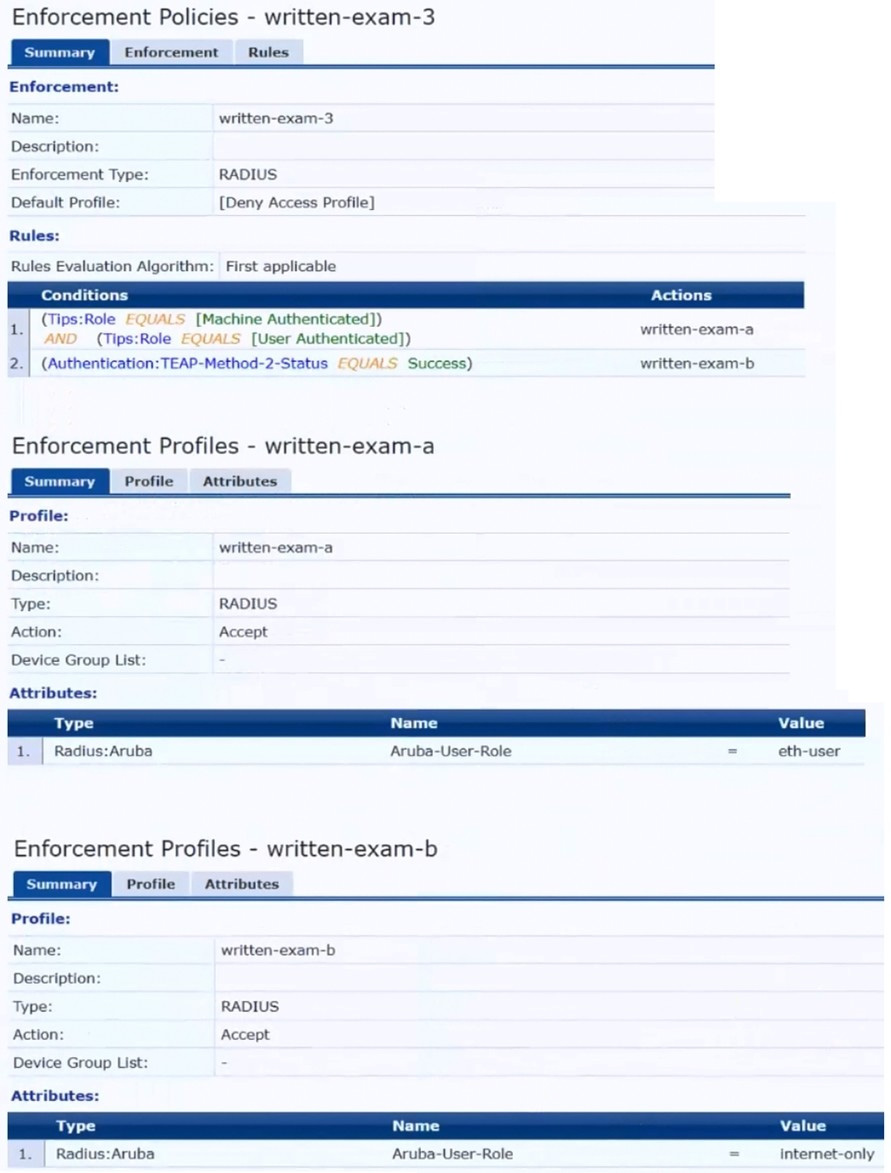
The gateway cluster has two gateways with these IP addresses:
Gateway 1
1.
VLAN 4085 (system IP) = 10.20.4.21
2.
VLAN 20 (users) = 10.20.20.1
3.
VLAN 4094 (WAN) = 198.51.100.14
Gateway 2
1.
VLAN 4085 (system IP) = 10.20.4.22
2.
VLAN 20 (users) = 10.20.20.2
3.
VLAN 4094 (WAN) = 198.51.100.12
VRRP on VLAN 20 = 10.20.20.254
The customer requires high availability for the tunnels between the switches and the gateway cluster. If one gateway falls, the other gateway should take over its tunnels. Also, the switch should be able to discover the gateway cluster regardless of whether one of the gateways is in the cluster.
What is one change that you should make to the solution?
A. Change the ubt-client-vlan to VLAN 13.
B. Configure edge ports in VLAN trunk mode.
C. Remove VLAN assignments from role configurations on the gateways.
D. Configure the UBT solution to use VLAN extend mode.
-
Question 16:
You are configuring gateway IDS/IPS settings in Aruba Central.
For which reason would you set the Fail Strategy to Bypass?
A. To permit traffic if the IPS engine falls to inspect It
B. To enable the gateway to honor the allowlist settings configured in IDS/IPS policies
C. To tell gateways to stop enforcing IDS/IPS policies if they lose connectivity to the Internet
D. To avoid wasting IPS engine resources on filtering traffic for unauthenticated clients
-
Question 17:
Refer to the scenario.
# Introduction to the customer
You are helping a company add Aruba ClearPass to their network, which uses Aruba network infrastructure devices.
The company currently has a Windows domain and Windows CA. The Window CA issues certificates to domain computers, domain users, and servers such as domain controllers. An example of a certificate issued by the Windows CA is shown here.
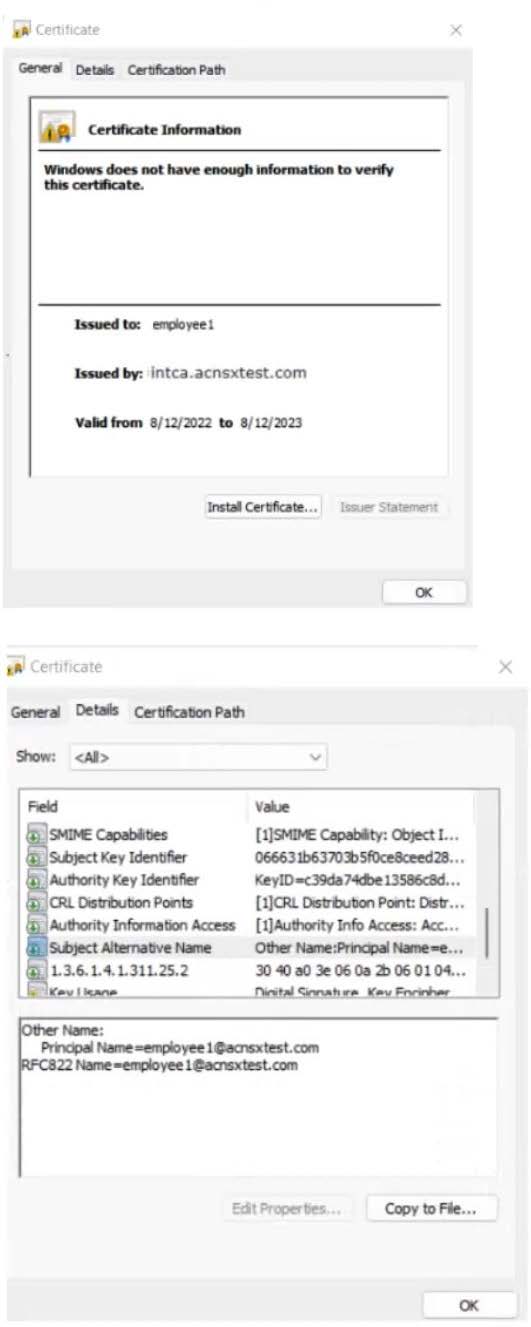
The company is in the process of adding Microsoft Endpoint Manager (Intune) to manage its mobile clients. The customer is maintaining the on-prem AD for now and uses Azure AD Connect to sync with Azure AD.
# Requirements for issuing certificates to mobile clients
The company wants to use ClearPass Onboard to deploy certificates automatically to mobile clients enrolled in Intune. During this process, Onboard should communicate with Azure AD to validate the clients. High availability should also be
provided for this scenario; in other words, clients should be able to get certificates from Subscriber 2 if Subscriber 1 is down.
The Intune admins intend to create certificate profiles that include a UPN SAN with the UPN of the user who enrolled the device.
# Requirements for authenticating clients
The customer requires all types of clients to connect and authenticate on the same corporate SSID.
The company wants CPPM to use these authentication methods:
1.
EAP-TLS to authenticate users on mobile clients registered in Intune
2.
TEAR, with EAP-TLS as the inner method to authenticate Windows domain computers and the users on them To succeed, EAP-TLS (standalone or as a TEAP method) clients must meet these requirements:
1.
Their certificate is valid and is not revoked, as validated by OCSP
2.
The client's username matches an account in AD # Requirements for assigning clients to roles After authentication, the customer wants the CPPM to assign clients to ClearPass roles based on the following rules:
1.
Clients with certificates issued by Onboard are assigned the "mobile-onboarded" role
2.
Clients that have passed TEAP Method 1 are assigned the "domain-computer" role
3.
Clients in the AD group "Medical" are assigned the "medical-staff" role
4.
Clients in the AD group "Reception" are assigned to the "reception-staff" role The customer requires CPPM to assign authenticated clients to AOS firewall roles as follows:
1.
Assign medical staff on mobile-onboarded clients to the "medical-mobile" firewall role
2.
Assign other mobile-onboarded clients to the "mobile-other" firewall role
3.
Assign medical staff on domain computers to the "medical-domain" firewall role
4.
All reception staff on domain computers to the "reception-domain" firewall role
5.
All domain computers with no valid user logged in to the "computer-only" firewall role
6.
Deny other clients access # Other requirements Communications between ClearPass servers and on-prem AD domain controllers must be encrypted. # Network topology For the network infrastructure, this customer has Aruba APs and Aruba gateways, which are managed by Central. APs use tunneled WLANs, which tunnel traffic to the gateway cluster. The customer also has AOS-CX switches that are not
managed by Central at this point.
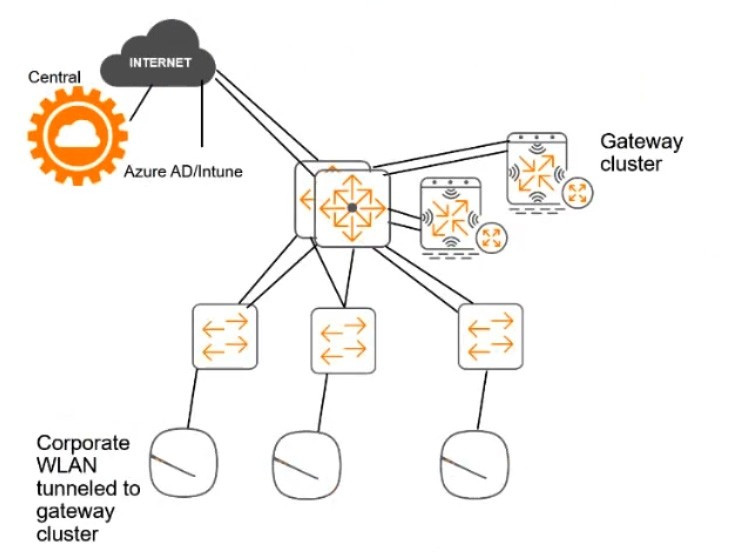
# ClearPass cluster IP addressing and hostnames A customer's ClearPass cluster has these IP addresses:
1.
Publisher = 10.47.47.5
2.
Subscriber 1 = 10.47.47.6
3.
Subscriber 2 = 10.47.47.7
4.
Virtual IP with Subscriber 1 and Subscriber 2 = 10.47.47.8 The customer's DNS server has these entries
1.
cp.acnsxtest.com = 10.47.47.5
2.
cps1.acnsxtest.com = 10.47.47.6
3.
cps2.acnsxtest.com = 10.47.47.7
4.
radius.acnsxtest.com = 10.47.47.8
5.
onboard.acnsxtest.com = 10.47.47.8 You cannot see flow attributes for wireless clients. What should you check?
A. Deep packet inspection is enabled on the role to which the Aruba APs assign the wireless clients.
B. Firewall application visibility is enabled on the Aruba gateways, and the gateways have been rebooted.
C. Gateway IDS/IPS is enabled on the Aruba gateways, and the gateways have been rebooted.
D. Deep packet inspection is enabled on the Aruba Aps, and the APs have been rebooted.
-
Question 18:
Refer to the scenario.
A customer has asked you to review their AOS-CX switches for potential vulnerabilities. The configuration for these switches is shown below:
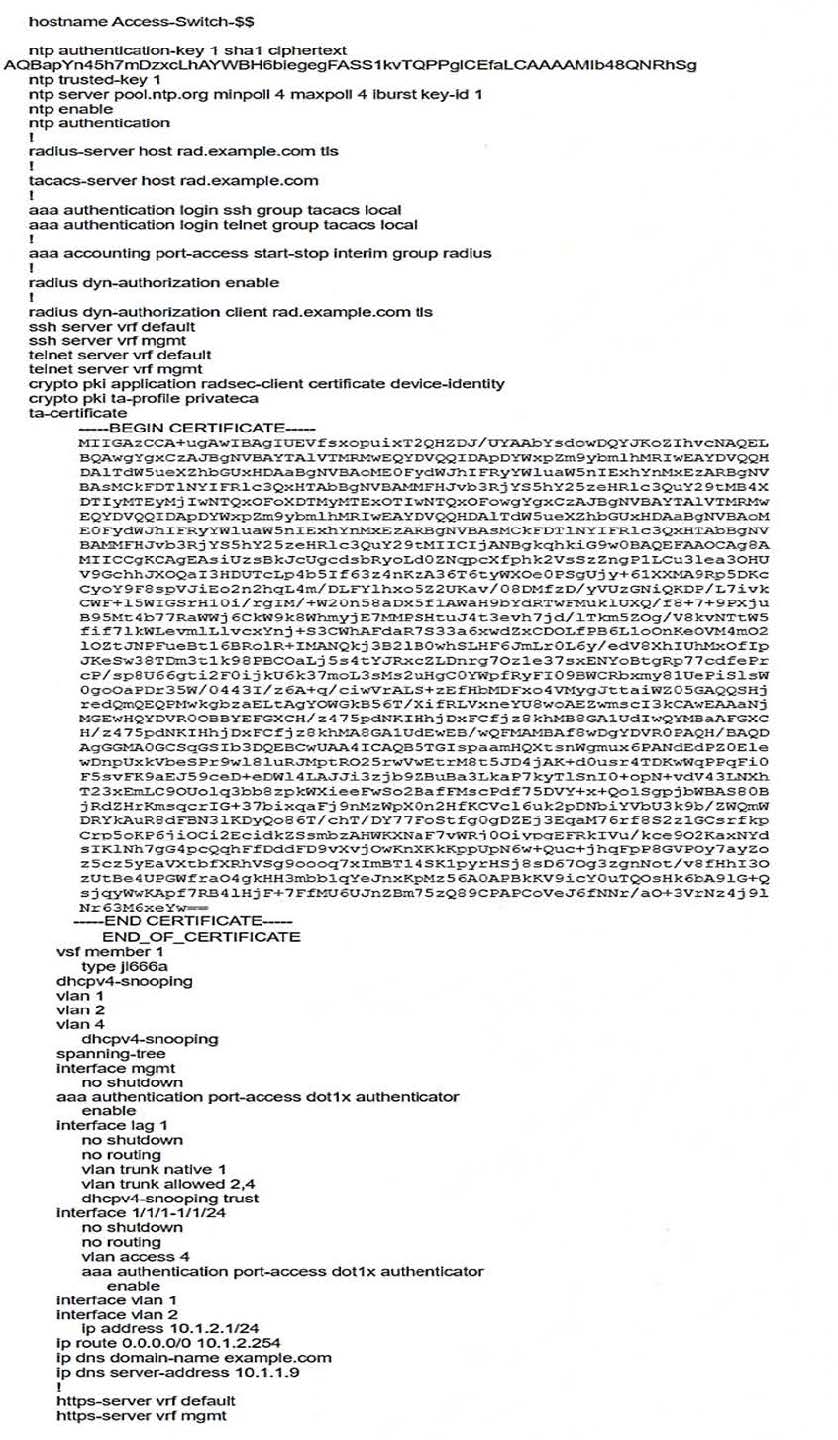
What is one recommendation to make?
A. Let the RADIUS server confiqure VLANs on LAG 1 dynamically.
B. Use MDS instead of SHA1 for the NTP authentication key.
C. Encrypt the certificate in the TA-profile.
D. Create a control plane ACL to limit the sources that can access the switch with SSH.
-
Question 19:
Refer to the scenario.
An organization wants the AOS-CX switch to trigger an alert if its RADIUS server (cp.acnsxtest.local) rejects an unusual number of client authentication requests per hour. After some discussions with other Aruba admins, you are still not sure
how many rejections are usual or unusual. You expect that the value could be different on each switch.
You are helping the developer understand how to develop an NAE script for this use case.
You are helping the developer find the right URI for the monitor.
Refer to the exhibit.
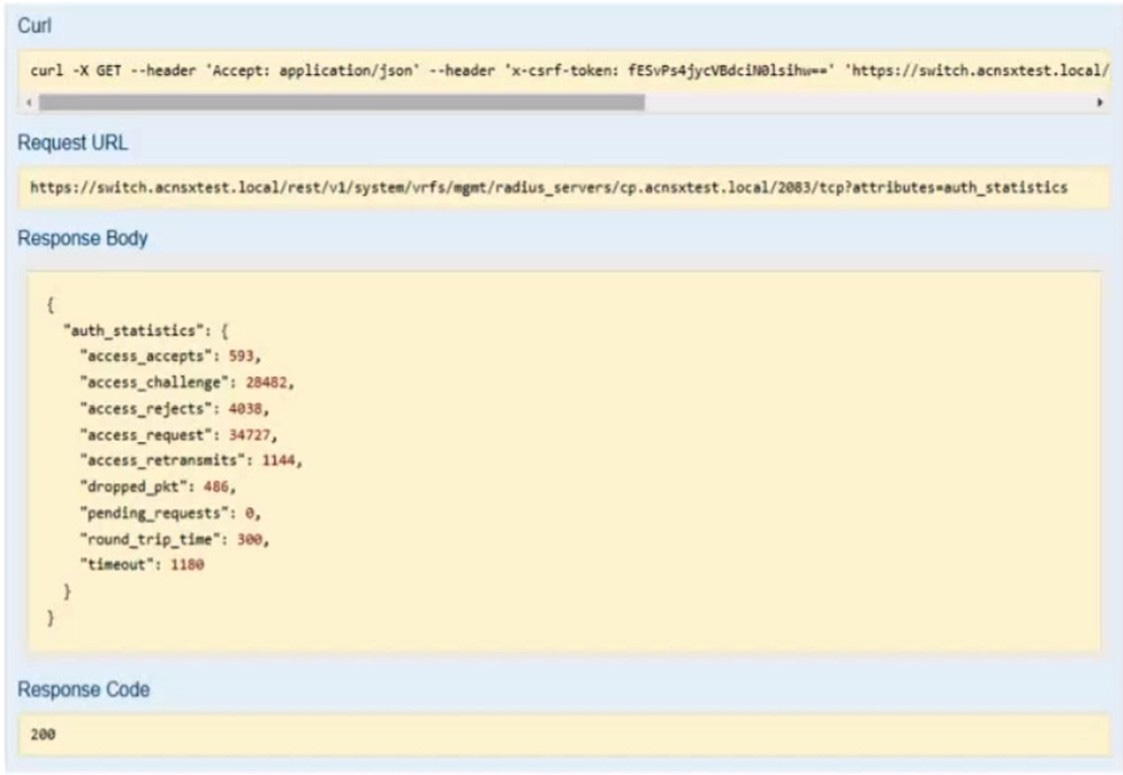
You have used the REST API reference interface to submit a test call. The results are shown in the exhibit.
Which URI should you give to the developer?
A. /rest/v1/system/vrfs/mgmt/radius/servers/cp.acnsxtest.local/2083/tcp?attributes=authstatisti cs
B. /rest/v1/system/vrfs/mgmt/radius/servers/cp.acnsxtest.local/2083/tcp?attributes=authstatisti cs?attributes=access_rejects
C. /rest/v1/system/vrfs/mgmt/radius/_servers/cp.acnsxtest.local/2083/tcp
D. /rest/v1/system/vrfs/mgmt/radius/servers/cp.acnsxtest.local/2083/tcp?attributes=authstatisti cs.access_rejects
-
Question 20:
Refer to the scenario.
A customer is migrating from on-prem AD to Azure AD as its sole domain solution. The customer also manages both wired and wireless devices with Microsoft Endpoint Manager (Intune).
The customer wants to improve security for the network edge. You are helping the customer design a ClearPass deployment for this purpose. Aruba network devices will authenticate wireless and wired clients to an Aruba ClearPass Policy Manager (CPPM) cluster (which uses version 6.10).
The customer has several requirements for authentication. The clients should only pass EAP-TLS authentication if a query to Azure AD shows that they have accounts in Azure AD. To further refine the clients' privileges, ClearPass also should use information collected by Intune to make access control decisions.
Assume that the Azure AD deployment has the proper prerequisites established.
You are planning the CPPM authentication source that you will reference as the authentication source in 802.1X services.
How should you set up this authentication source?
A. As Kerberos type
B. As Active Directory type
C. As HTTP type, referencing the Intune extension
D. AS HTTP type, referencing Azure AD's FODN
Related Exams:
HP0-D15
Administering HP CloudSystem Matrix SolutionsHP0-D20
Architecting the HP Matrix Operating EnvironmentHP2-E56
Selling HP SMB SolutionsHP2-H88
Selling HP Business Personal Systems Hardware 2019HP2-I14
Selling HP Supplies 2020HP2-I15
Selling HP Business Personal Systems Hardware 2020HP2-I17
Selling HP Printing Hardware 2020HP2-I44
Selling HP Workstations 2022HP2-I73
Selling HP Retail and Hospitality Solutions 2024HP2-N51
HP Application Lifecycle Management 12.x Software
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only HP exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your HPE6-A84 exam preparations and HP certification application, do not hesitate to visit our Vcedump.com to find your solutions here.