Exam Details
Exam Code
:HPE6-A84Exam Name
:Aruba Certified Network Security Expert WrittenCertification
:HP CertificationsVendor
:HPTotal Questions
:60 Q&AsLast Updated
:Jun 24, 2025
HP HP Certifications HPE6-A84 Questions & Answers
-
Question 21:
Several AOS-CX switches are responding to SNMPv2 GET requests for the public community. The customer only permits SNMPv3. You have asked a network admin to fix this problem. The admin says, "I tried to remove the community, but the CLI output an error."
What should you recommend to remediate the vulnerability and meet the customer's requirements?
A. Enabling control plane policing to automatically drop SNMP GET requests
B. Setting the snmp-server settings to "snmpv3-only"
C. Adding an SNMP community with a long random name
D. Enabling SNMPv3, which implicitly disables SNMPv1/v2
-
Question 22:
Refer to the scenario.
A customer is migrating from on-prem AD to Azure AD as its sole domain solution. The customer also manages both wired and wireless devices with Microsoft Endpoint Manager (Intune).
The customer wants to improve security for the network edge. You are helping the customer design a ClearPass deployment for this purpose. Aruba network devices will authenticate wireless and wired clients to an Aruba ClearPass Policy Manager (CPPM) cluster (which uses version 6.10).
The customer has several requirements for authentication. The clients should only pass EAP-TLS authentication if a query to Azure AD shows that they have accounts in Azure AD. To further refine the clients' privileges, ClearPass also should use information collected by Intune to make access control decisions.
You are planning to use Azure AD as the authentication source in 802.1X services.
What should you make sure that the customer understands is required?
A. An app registration on Azure AD that references the CPPM's FQDN
B. Windows 365 subscriptions
C. CPPM's RADIUS certificate was imported as trusted in the Azure AD directory
D. Azure AD Domain Services
-
Question 23:
Refer to the scenario.
An organization wants the AOS-CX switch to trigger an alert if its RADIUS server (cp.acnsxtest.local) rejects an unusual number of client authentication requests per hour. After some discussions with other Aruba admins, you are still not sure how many rejections are usual or unusual. You expect that the value could be different on each switch. You are helping the developer understand how to develop an NAE script for this use case.
The developer explains that they plan to define the rule with logic like this:
monitor > value
However, the developer asks you what value to include.
What should you recommend?
A. Checking one of the access switches' RADIUS statistics and adding 10 to the number listed for rejects
B. Defining a baseline and referring to it for the value
C. Using 10 (per hour) as a good starting point for the value
D. Defining a parameter and referring to it (self ^ramsfname]) for the value
-
Question 24:
A company has an Aruba ClearPass server at 10.47.47.8, FQDN radius.acnsxtest.local. This exhibit shows ClearPass Policy Manager's (CPPM's) settings for an Aruba Mobility Controller (MC).
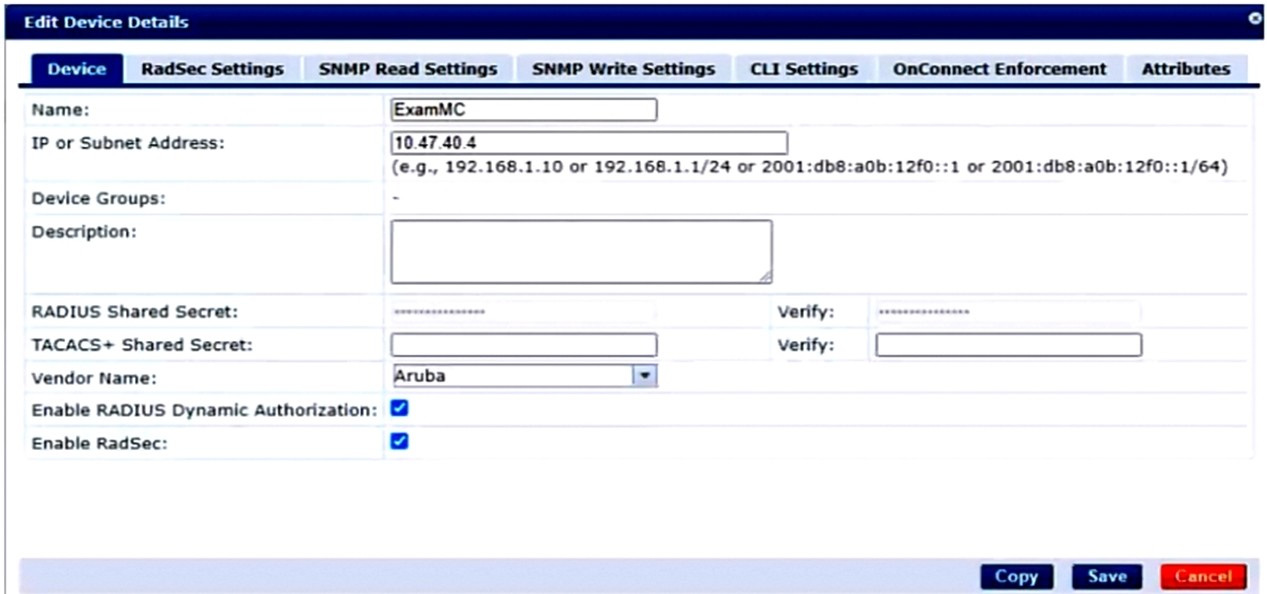
The MC is already configured with RADIUS authentication settings for CPPM, and RADIUS requests between the MC and CPPM are working. A network admin enters and commits this command to enable dynamic authorization on the MC:
aaa rfc-3576-server 10.47.47.8
But when CPPM sends CoA requests to the MC, they are not working. This exhibit shows the RFC 3576 server statistics on the MC:

How could you fix this issue?
A. Change the UDP port in the MCs' RFC 3576 server config to 3799.
B. Enable RadSec on the MCs' RFC 3676 server config.
C. Configure the MC to obtain the time from a valid NTP server.
D. Make sure that CPPM is using an ArubaOS Wireless RADIUS CoA enforcement profile.
-
Question 25:
A customer has an AOS 10 architecture, which includes Aruba APs. Admins have recently enabled WIDS at the high level. They also enabled alerts and email notifications for several events, as shown in the exhibit.
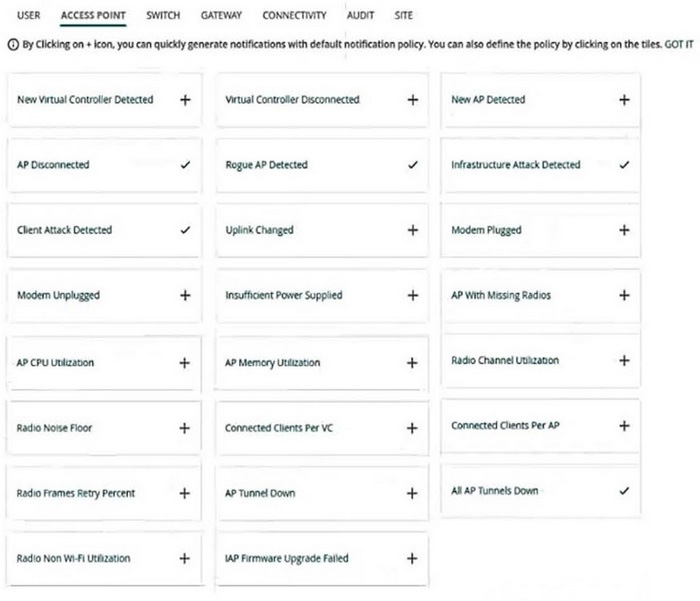
Admins are complaining that they are getting so many emails that they have to ignore them, so they are going to turn off all notifications.
What is one step you could recommend trying first?
A. Send the email notifications directly to a specific folder, and only check the folder once a week.
B. Disable email notifications for Roque AP, but leave the Infrastructure Attack Detected and Client Attack Detected notifications on.
C. Change the WIDS level to custom, and enable only the checks most likely to indicate real threats.
D. Disable just the Rogue AP and Client Attack Detected alerts, as they overlap with the Infrastructure Attack Detected alert.
-
Question 26:
A customer's admins have added RF Protect licenses and enabled WIDS for a customer's AOS 8-based solution. The customer wants to use the built-in capabilities of APs without deploying dedicated air monitors (AMs). Admins tested rogue AP detection by connecting an unauthorized wireless AP to a switch. The rogue AP was not detected even after several hours.
What is one point about which you should ask?
A. Whether APs' switch ports support all the VLANs that are accessible at the edge
B. Whether admins enabled wireless containment
C. Whether admins set at least one radio on each AP to air monitor mode
D. Whether the customer is using non-standard Wi-Fi channels in the deployment
-
Question 27:
A company has Aruba gateways that are Implementing gateway IDS/IPS in IDS mode. The customer complains that admins are receiving too frequent of repeat email notifications for the same threat. The threat itself might be one that the admins should investigate, but the customer does not want the email notification to repeat as often.
Which setting should you adjust in Aruba Central?
A. Report scheduling settings
B. Alert duration and threshold settings
C. The IDS policy setting (strict, medium, or lenient)
D. The allowlist settings in the IDS policy
-
Question 28:
Refer to the scenario.
A customer requires these rights for clients in the "medical-mobile" AOS firewall role on Aruba Mobility Controllers (MCs):
1.
Permitted to receive IP addresses with DHCP
2.
Permitted access to DNS services from 10.8.9.7 and no other server
3.
Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
4.
Denied access to other 10.0.0.0/8 subnets
5.
Permitted access to the Internet
6.
Denied access to the WLAN for a period of time if they send any SSH traffic
7.
Denied access to the WLAN for a period of time if they send any Telnet traffic
8.
Denied access to all high-risk websites
External devices should not be permitted to initiate sessions with "medical-mobile" clients, only send return traffic.
The exhibits below show the configuration for the role.
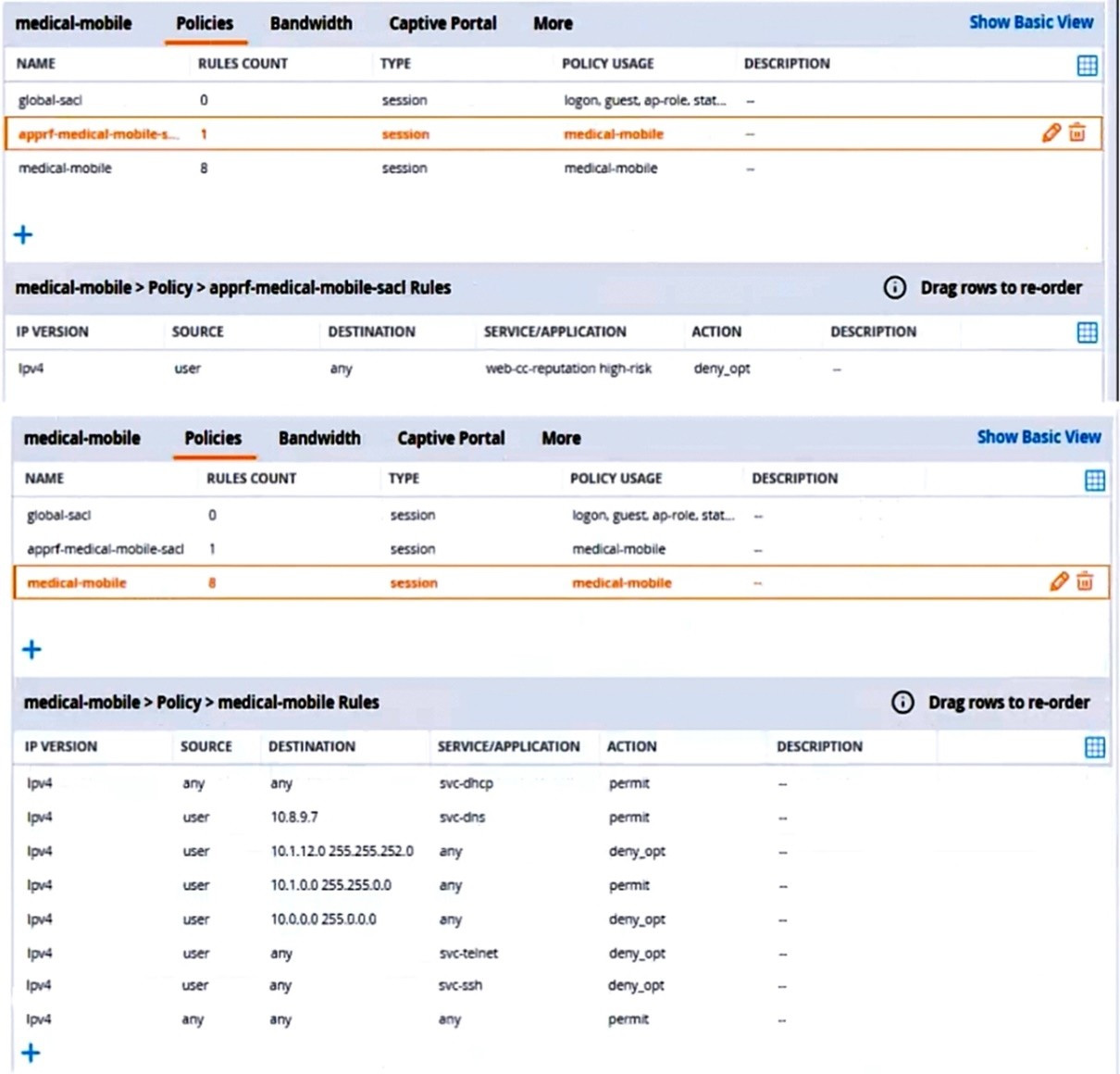
There are multiple issues with the configuration.
What is one of the changes that you must make to the policies to meet the scenario requirements? (In the options, rules in a policy are referenced from top to bottom. For example, "medical-mobile" rule 1 is "ipv4 any any svc-dhcp permit," and rule 8 is "ipv4 any any any permit'.)
A. In the "medical-mobile" policy, change the source in rule 1 to "user."
B. In the "medical-mobile" policy, change the subnet mask in rule 3 to 255.255.248.0.
C. In the "medical-mobile" policy, move rules 6 and 7 to the top of the list.
D. Move the rule in the "apprf-medical-mobile-sacl" policy between rules 7 and 8 in the "medical-mobile" policy.
-
Question 29:
Refer to the scenario.
# Introduction to the customer
You are helping a company add Aruba ClearPass to their network, which uses Aruba network infrastructure devices.
The company currently has a Windows domain and Windows CA. The Window CA issues certificates to domain computers, domain users, and servers such as domain controllers. An example of a certificate issued by the Windows CA is
shown here.
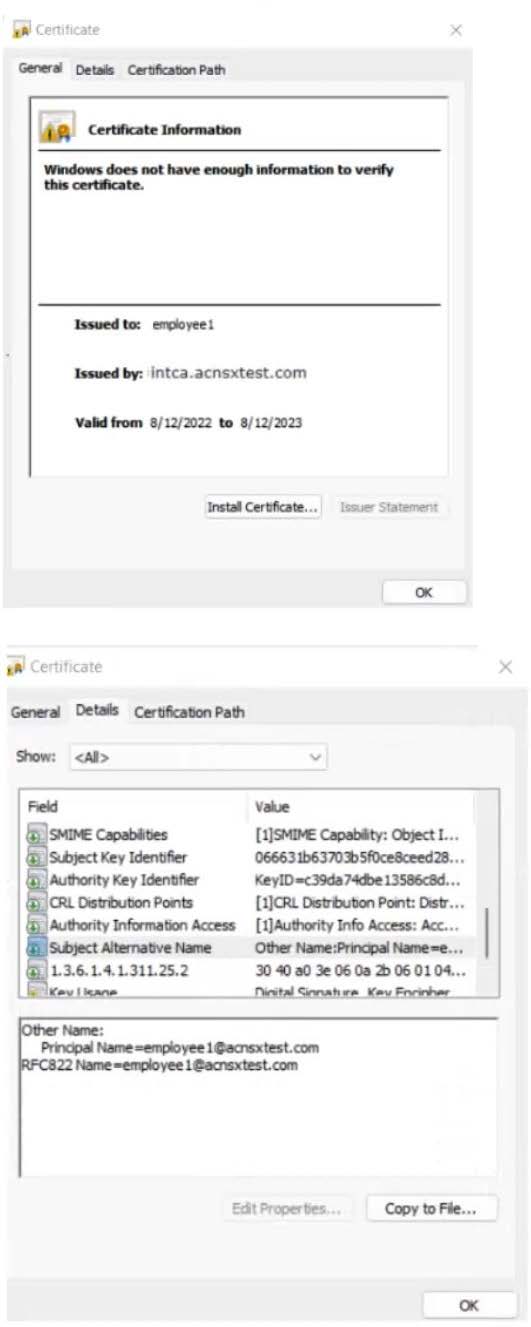
The company is in the process of adding Microsoft Endpoint Manager (Intune) to manage its mobile clients. The customer is maintaining the on-prem AD for now and uses Azure AD Connect to sync with Azure AD.
# Requirements for issuing certificates to mobile clients
The company wants to use ClearPass Onboard to deploy certificates automatically to mobile clients enrolled in Intune. During this process, Onboard should communicate with Azure AD to validate the clients. High availability should also be
provided for this scenario; in other words, clients should be able to get certificates from Subscriber 2 if Subscriber 1 is down.
The Intune admins intend to create certificate profiles that include a UPN SAN with the UPN of the user who enrolled the device.
# Requirements for authenticating clients
The customer requires all types of clients to connect and authenticate on the same corporate SSID.
The company wants CPPM to use these authentication methods:
1.
EAP-TLS to authenticate users on mobile clients registered in Intune
2.
TEAR, with EAP-TLS as the inner method to authenticate Windows domain computers and the users on them To succeed, EAP-TLS (standalone or as a TEAP method) clients must meet these requirements:
1.
Their certificate is valid and is not revoked, as validated by OCSP
2.
The client's username matches an account in AD # Requirements for assigning clients to roles After authentication, the customer wants the CPPM to assign clients to ClearPass roles based on the following rules:
1.
Clients with certificates issued by Onboard are assigned the "mobile-onboarded" role
2.
Clients that have passed TEAP Method 1 are assigned the "domain-computer" role
3.
Clients in the AD group "Medical" are assigned the "medical-staff" role
4.
Clients in the AD group "Reception" are assigned to the "reception-staff" role The customer requires CPPM to assign authenticated clients to AOS firewall roles as follows:
1.
Assign medical staff on mobile-onboarded clients to the "medical-mobile" firewall role
2.
Assign other mobile-onboarded clients to the "mobile-other" firewall role
3.
Assign medical staff on domain computers to the "medical-domain" firewall role
4.
All reception staff on domain computers to the "reception-domain" firewall role
5.
All domain computers with no valid user logged in to the "computer-only" firewall role
6.
Deny other clients access # Other requirements Communications between ClearPass servers and on-prem AD domain controllers must be encrypted. # Network topology For the network infrastructure, this customer has Aruba APs and Aruba gateways, which are managed by Central. APs use tunneled WLANs, which tunnel traffic to the gateway cluster. The customer also has AOS-CX switches that are not
managed by Central at this point.
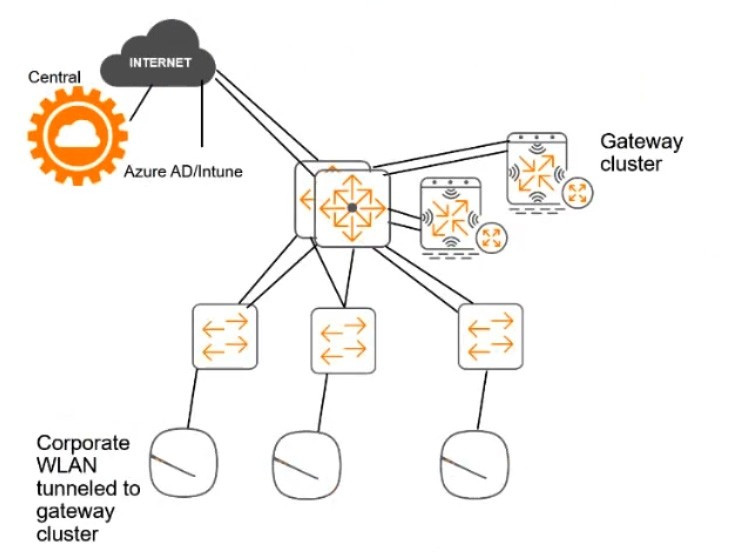
# ClearPass cluster IP addressing and hostnames
A customer's ClearPass cluster has these IP addresses:
1.
Publisher = 10.47.47.5
2.
Subscriber 1 = 10.47.47.6
3.
Subscriber 2 = 10.47.47.7
4.
Virtual IP with Subscriber 1 and Subscriber 2 = 10.47.47.8
The customer's DNS server has these entries
1.
cp.acnsxtest.com = 10.47.47.5
2.
cps1.acnsxtest.com = 10.47.47.6
3.
cps2.acnsxtest.com = 10.47.47.7
4.
radius.acnsxtest.com = 10.47.47.8
5.
onboard.acnsxtest.com = 10.47.47.8
On CPPM, you are creating the authentication method shown in the exhibit below:
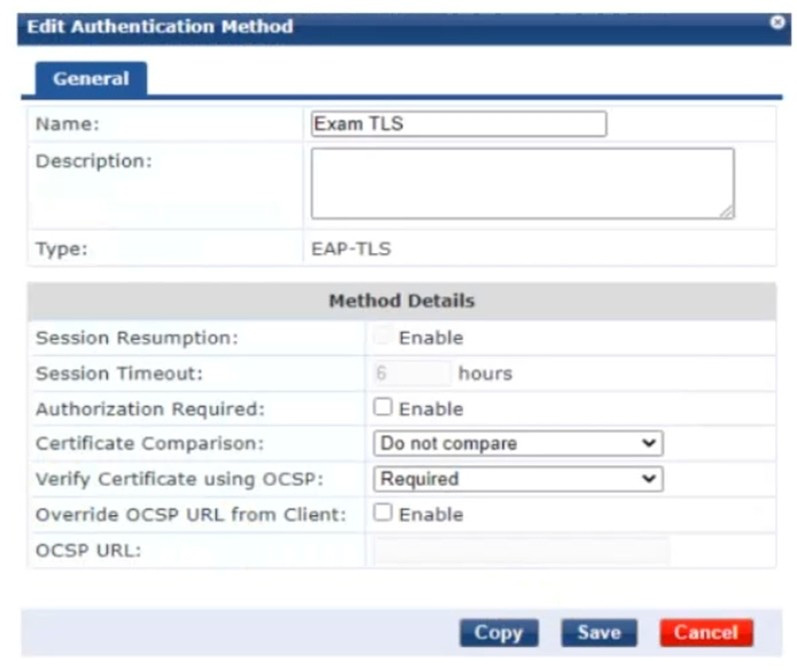
You will use the method for standalone EAP-TLS and for inner methods in TEAP. What should you do?
A. Configure OCSP override and set the OCSP URL to localhost/onboard/mdps ocspphp/2
B. Enable certificate comparison.
C. Enable authorization.
D. Configure OCSP override and leave the OCSP URL blank.
-
Question 30:
Refer to the exhibit.
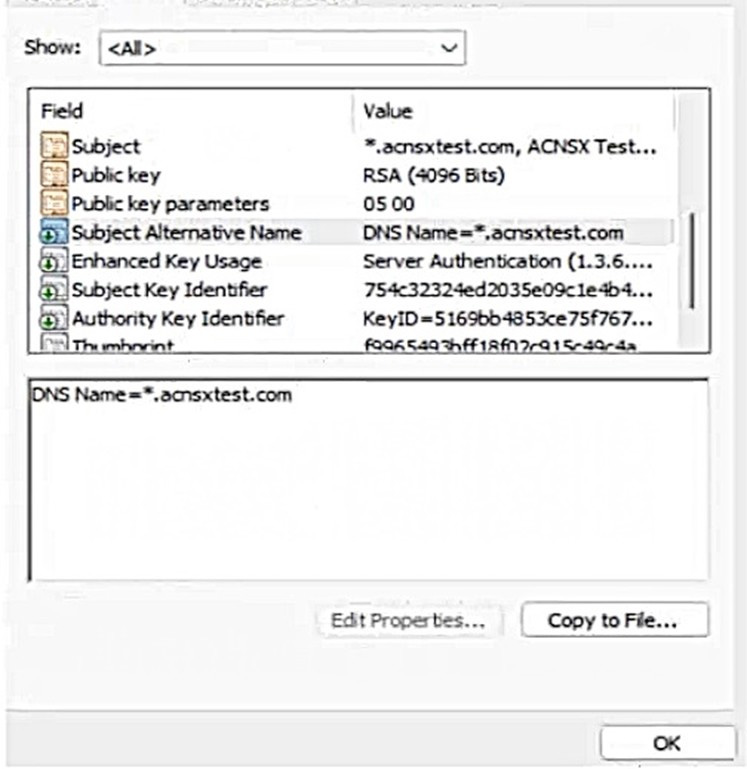
You have been given this certificate to install on a ClearPass server for the RADIUS/EAP and RadSec usages.
What is one issue?
A. The certificate has a wildcard in the subject common name.
B. The certificate uses a fully qualified the '.local" domain name.
C. The certificate does not have a URI subject alternative name
D. The certificate does not have an IP subject alternative name
Related Exams:
HP0-003
HP OpenView Service Desk 5.xHP0-045
Supporting the ESL E-Series LobrariesHP0-052
Planning and Design of HP 9000/HP Integrity Server SolutionsHP0-053
Enterprise Integration and Management of HP ProLiant ServersHP0-054
Compaq/Oracle 8i I and P with Windows NTHP0-055
Implementing HP ProLiant ServersHP0-058
Configuration and Management of HP Integrity Mid-Range ServersHP0-063
LF PROFESSIONAL COLOR WORKFLOW MANAGEMENTHP0-064
HP BladeSystems C-Class Solutions 1HP0-065
Planning and Designing ProLiant Solutions for the Enterprise
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only HP exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your HPE6-A84 exam preparations and HP certification application, do not hesitate to visit our Vcedump.com to find your solutions here.