Exam Details
Exam Code
:N10-009Exam Name
:CompTIA Network+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:390 Q&AsLast Updated
:Mar 28, 2025
CompTIA CompTIA Certifications N10-009 Questions & Answers
-
Question 11:
A user reports having intermittent connectivity issues to the company network. The network configuration for the user reveals the following: IP address: 192.168.1.10
Subnet mask: 255.255.255.0 Default gateway: 192.168.1.254 The network switch shows the following ARP table:
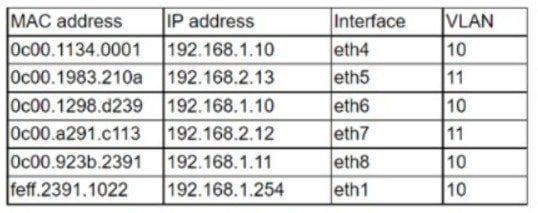
Which of the following is the most likely cause of the user's connection issues?
A. A port with incorrect VLAN assigned
B. A switch with spanning tree conflict
C. Another PC with manually configured IP
D. A router with overlapping route tables
-
Question 12:
An organization has a security staff shortage and must prioritize efforts in areas where the staff will have the most impact. In particular, the focus is to avoid expending resources on identifying non-relevant events. A security analyst is reviewing web server logs and sees the following:
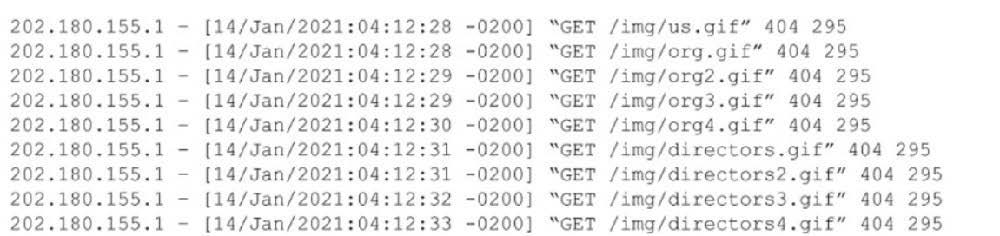
Which of the following should the analyst recommend?
A. Configuring the web server log to filter out 404 errors on image files
B. Updating firewall rules to block 202.180.155.1
C. Resyncing the network time server and monitoring logs for future anomalous behavior
D. Checking with the penetration testing team to see if the team ran any scans on January 14, 2021
-
Question 13:
Which of the following disaster recovery metrics describes the average length of time a piece of equipment can be expected to operate normally?
A. RPO
B. RTO
C. MTTR
D. MTBF
-
Question 14:
A network administrator needs to create a way to redirect a network resource that has been on the local network but is now hosted as a SaaS solution. Which of the following records should be used to accomplish the task?
A. TXT
B. AAA
C. PTR
D. CNAME
-
Question 15:
Which of the following DNS records maps an alias to a true name?
A. AAAA
B. NS
C. TXT
D. CNAME
-
Question 16:
Which of the following OSI model layers will ensure messages are transmitted to their destinations and no data is duplicated?
A. Session
B. Data link
C. Network
D. Transport
-
Question 17:
A network administrator is notified that a user cannot access resources on the network. The network administrator checks the physical connections to the workstation labeled User and sees the Ethernet is properly connected. However, the network interface's indicator lights are not blinking on either the computer or the switch. Which of the following is the most likely cause?
A. The switch failed.
B. The default gateway is wrong.
C. The port is shut down.
D. The VLAN assignment is incorrect.
-
Question 18:
Which of the following objectives does an evil twin achieve?
A. DNS poisoning
B. Log-in credentials
C. ARP spoofing
D. Denial of service
-
Question 19:
A network engineer is installing hardware in a newly renovated data center. Major concerns that were addressed during the renovation induded air circulation, building power redundancy, and the need for continuous monitoring. The network engineer IS creating alerts based on the following operation specifications:
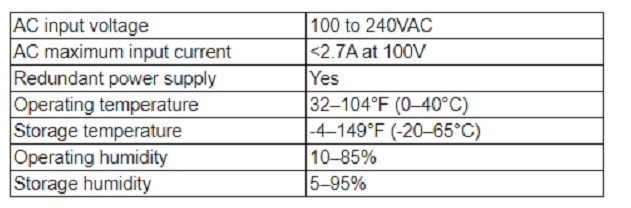
Which of the following should the network engineer configure?
A. Environmental monitoring alerts for humidity greater than 95%
B. SIEM to parse syslog events for a failed power supply
C. SNMP traps to report when the chassis temperature exceeds 950F (3500)
D. UPS monitoring to report when input voltage drops below 220VAC
-
Question 20:
A network administrator needs to add access points to the network because coverage in some areas is improper. Which of the following should the administrator do first?
A. Interference analysis
B. Wireless survey
C. Traffic analysis
D. Packet capture
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your N10-009 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.