Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Mar 29, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 151:
A security team discovered a large number of company-issued devices with non-work- related software installed. Which of the following policies would most likely contain language that would prohibit this activity?
A. NDA
B. BPA
C. AUP D. SLA
-
Question 152:
A security analyst receives an alert that indicates a user's device is displaying anomalous behavior The analyst suspects the device might be compromised. Which of the following should the analyst to first?
A. Reboot the device
B. Set the host-based firewall to deny an incoming connection
C. Update the antivirus definitions on the device
D. Isolate the device
-
Question 153:
Which of the following security design features can an development team to analyze the deletion eoting Of data sets the copy?
A. Stored procedures
B. Code reuse
C. Version control
D. Continunus
-
Question 154:
Which of the following measures the average time that equipment will operate before it breaks?
A. SLE
B. MTBF
C. RTO
D. ARO
-
Question 155:
A company recently enhanced mobile device configuration by implementing a set of security controls: biometrics, context-aware authentication, and full device encryption. Even with these settings in place, an unattended phone was used by a malicious actor to access corporate data.
Which of the following additional controls should be put in place first?
A. GPS tagging
B. Remote wipe
C. Screen lock timer
D. SEAndroid
-
Question 156:
An employee's laptop was stolen last month. This morning, the was returned by the A cyberrsecurity analyst retrieved laptop and has since cybersecurity incident checklist Four incident handlers are responsible for executing the checklist. Which of the following best describes the process for evidence collection assurance?
A. Time stamp
B. Chain of custody
C. Admissibility
D. Legal hold
-
Question 157:
Stakeholders at an organisation must be kept aware of any incidents and receive updates on status changes as they occur. Which of the following Plans would fulfill this requirement?
A. Communication plan
B. Disaster recovery plan
C. Business continuity plan
D. Risk plan
-
Question 158:
A security analyst is reviewing the following logs:
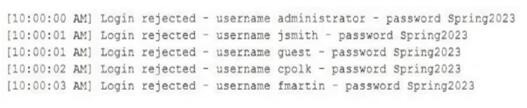
Which of the following attacks is most likely occurring?
A. Password spraying
B. Account forgery
C. Pass-the-hash
D. Brute-force
-
Question 159:
A candidate attempts to go to but accidentally visits http://comptiia.org. The malicious website looks exactly like the legitimate website. Which of the following best describes this type of attack?
A. Reconnaissance
B. Impersonation
C. Typosquatting
D. Watering-hole
-
Question 160:
A new security engineer has started hardening systems. One o( the hardening techniques the engineer is using involves disabling remote logins to the NAS. Users are now reporting the inability lo use SCP to transfer files to the NAS, even though the data is still viewable from the users' PCs. Which of the following is the MOST likely cause of this issue?
A. TFTP was disabled on the local hosts.
B. SSH was turned off instead of modifying the configuration file.
C. Remote login was disabled in the networkd.conf instead of using the sshd. conf.
D. Network services are no longer running on the NAS
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.