Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 161:
A security administrator needs a method to secure data in an environment that includes some form of checks so that the administrator can track any changes. Which of the following should the administrator set up to achieve this goal?
A. SPF
B. GPO
C. NAC
D. FIM
-
Question 162:
An administrator is reviewing a single server's security logs and discovers the following:
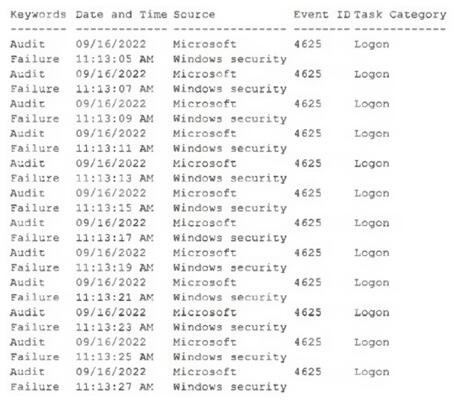
Which of the following best describes the action captured in this log file?
A. Brute-force attack
B. Privilege escalation
C. Failed password audit
D. Forgotten password by the user
-
Question 163:
Which of the following must be considered when designing a high-availability network? (Choose two.)
A. Ease of recovery
B. Ability to patch
C. Physical isolation
D. Responsiveness
E. Attack surface
F. Extensible authentication
-
Question 164:
Which of the following strategies shifts risks that are not covered in an organization's risk strategy?
A. Risk transference
B. Risk avoidance
C. Risk mitigation
D. Risk acceptance
-
Question 165:
Which of the following agreements defines response time, escalation points, and performance metrics?
A. BPA
B. MOA
C. NDA
D. SLA
-
Question 166:
A bakery has a secret recipe that it wants to protect. Which of the following objectives should be added to the company's security awareness training?
A. Insider threat detection
B. Risk analysis
C. Phishing awareness
D. Business continuity planning
-
Question 167:
A user would like to install software and features that are not available with a mobile device's default software. Which of the following would all the user to install unauthorized software and enable new features?
A. SQLi
B. Cross-site scripting
C. Jailbreaking
D. Side loading
-
Question 168:
A company has had several malware incidents that have been traced back to users accessing personal SaaS applications on the internet from the company network. The company has a policy that states users can only access business-related cloud applications from within the company network. Which of the following technical solutions should be used to enforce the policy?
A. Implement single sign-on using an identity provider
B. Leverage a cloud access security broker.
C. Configure cloud security groups
D. Install a virtual private cloud endpoint
-
Question 169:
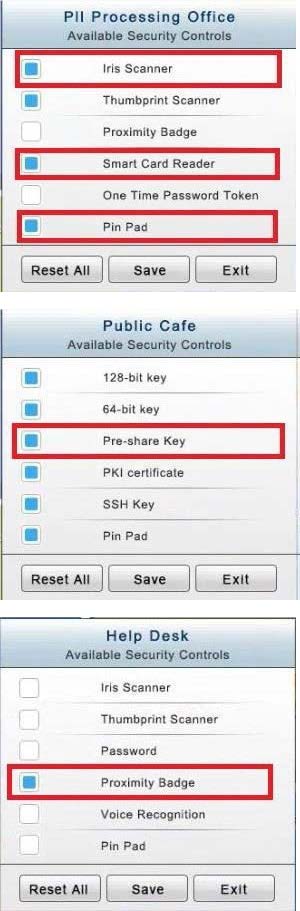
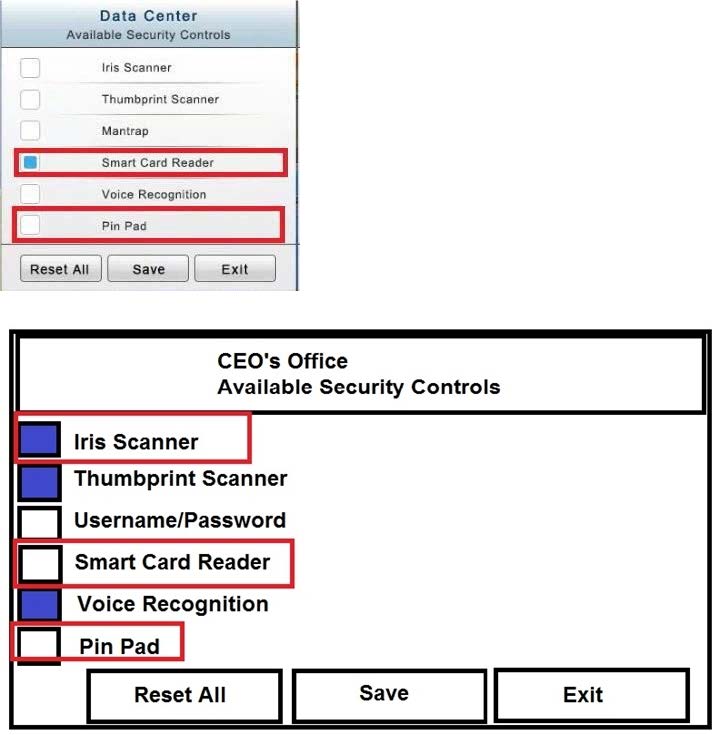
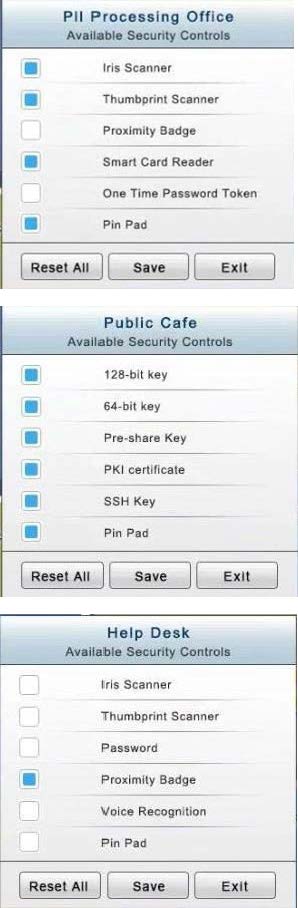
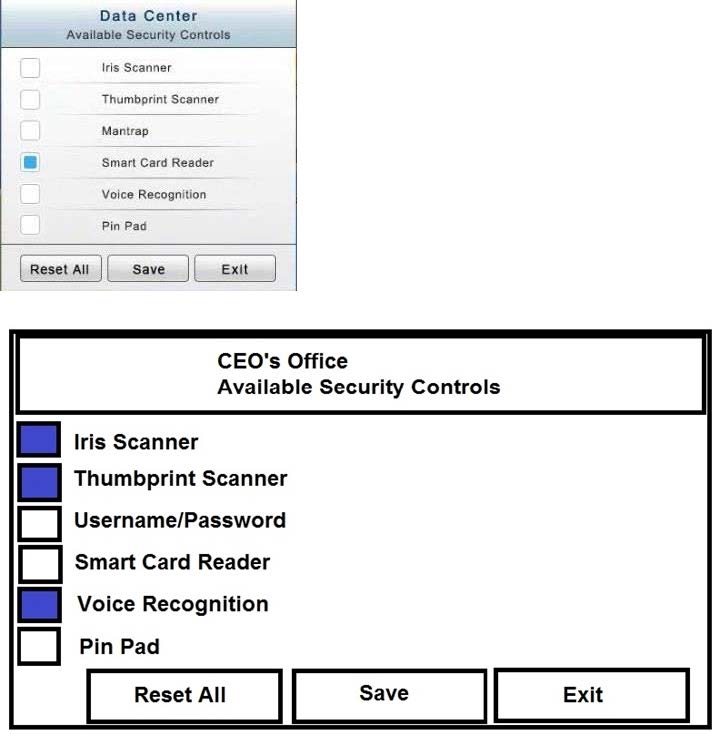
You have just received some room and WiFi access control recommendations from a security consulting company. Click on each building to bring up available security controls. Please implement the following requirements:
The Chief Executive Officer's (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three-factor authentication, while retaining the expensive iris render.
The Public Cafe has wireless available to customers. You need to secure the WAP with WPA and place a passphrase on the customer receipts.
In the Data Center you need to include authentication from the "something you know" category and take advantage of the existing smartcard reader on the door.
In the Help Desk Office, you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.
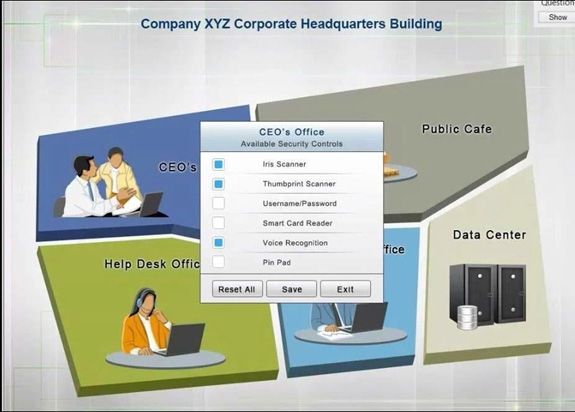
Instructions: The original security controls for each office can be reset at any time by selecting the Reset button. Once you have met the above requirements for each office, select the Save button. When you have completed the entire simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
-
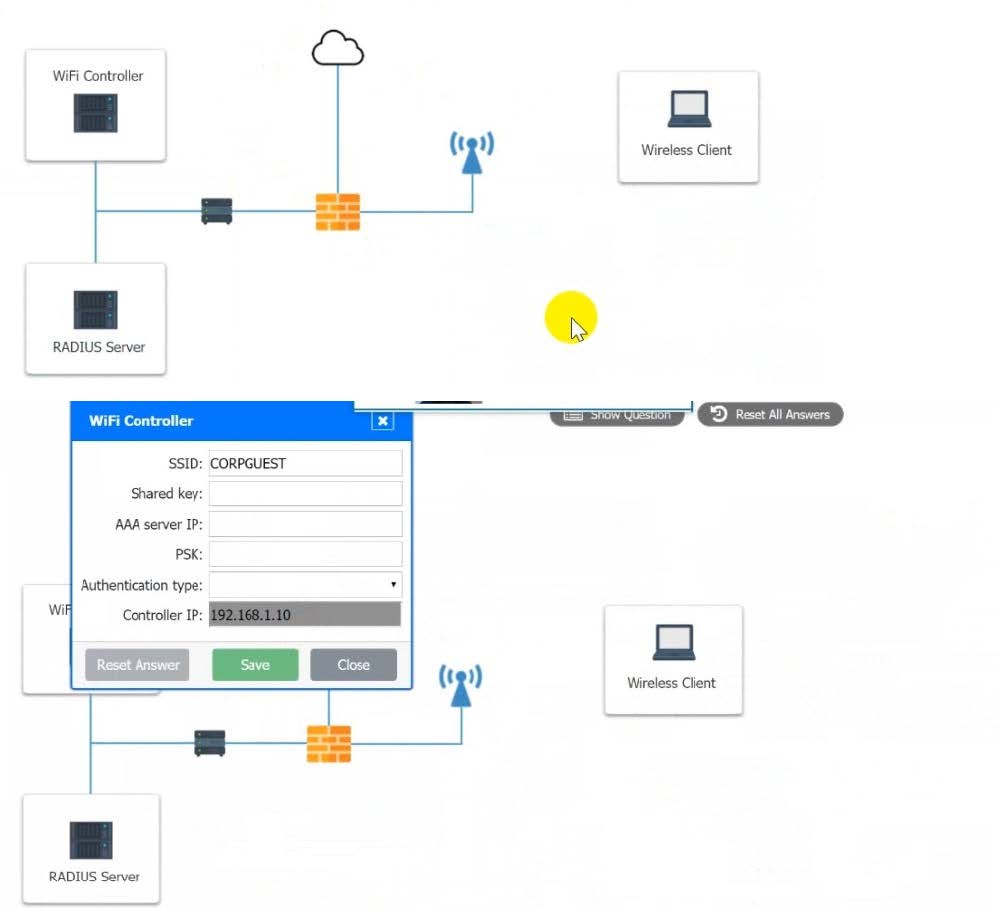
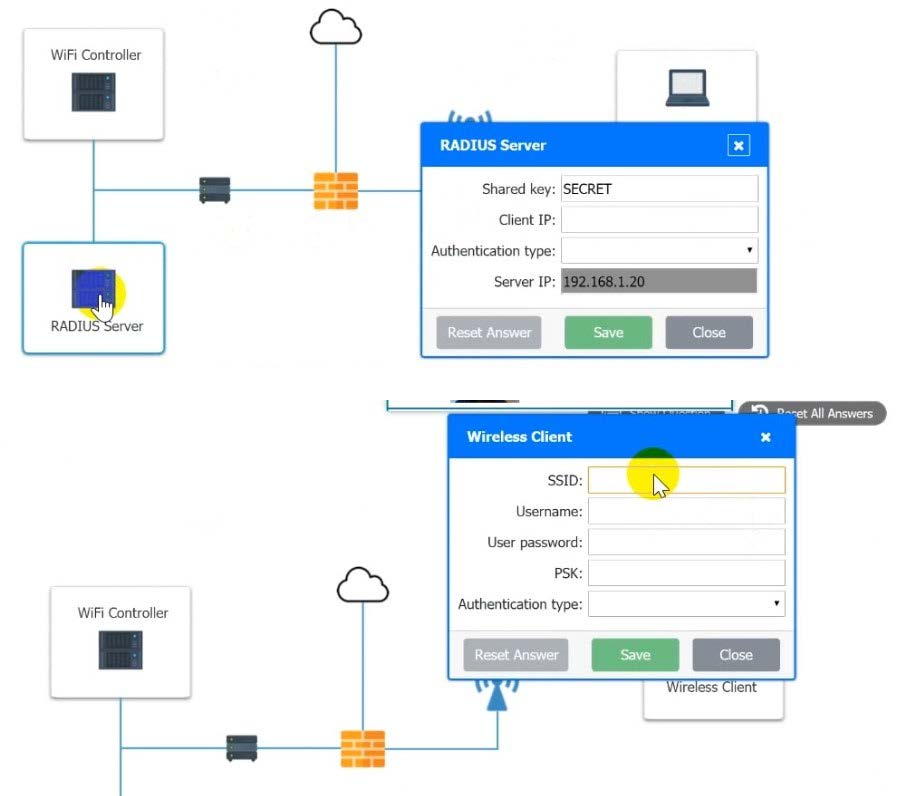
Question 170:
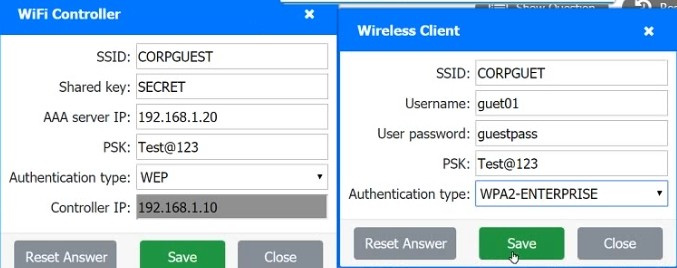
CORRECT TEXT
A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
Perform the following slops:
1.
Configure the RADIUS server.
2.
Configure the WiFi controller.
3.
Preconfigure the client for an incoming guest. The guest AD credentials are:
User: guest01 Password: guestpass
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.