Exam Details
Exam Code
:SY0-701Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:718 Q&AsLast Updated
:Apr 11, 2025
CompTIA CompTIA Certifications SY0-701 Questions & Answers
-
Question 271:
Employees in the research and development business unit receive extensive training to ensure they understand how to best protect company data. Which of the following is the type of data these employees are most likely to use in day-to-day work activities?
A. Encrypted
B. Intellectual property
C. Critical
D. Data in transit
-
Question 272:
An employee receives a text message that appears to have been sent by the payroll department and is asking for credential verification. Which of the following social engineering techniques are being attempted? (Choose two.)
A. Typosquatting
B. Phishing
C. Impersonation
D. Vishing
E. Smishing
F. Misinformation
-
Question 273:
A small business uses kiosks on the sales floor to display product information for customers. A security team discovers the kiosks use end-of-life operating systems. Which of the following is the security team most likely to document as a security implication of the current architecture?
A. Patch availability
B. Product software compatibility
C. Ease of recovery
D. Cost of replacement
-
Question 274:
A newly identified network access vulnerability has been found in the OS of legacy loT devices. Which of the following would best mitigate this vulnerability quickly?
A. Insurance
B. Patching
C. Segmentation
D. Replacement
-
Question 275:
A security analyst reviews domain activity logs and notices the following:

Which of the following is the best explanation for what the security analyst has discovered?
A. The user jsmith's account has been locked out.
B. A keylogger is installed on [smith's workstation
C. An attacker is attempting to brute force ismith's account.
D. Ransomware has been deployed in the domain.
-
Question 276:
Security controls in a data center are being reviewed to ensure data is properly protected and that human life considerations are included. Which of the following best describes how the controls should be set up?
A. Remote access points should fail closed.
B. Logging controls should fail open.
C. Safety controls should fail open.
D. Logical security controls should fail closed.
-
Question 277:
An analyst is evaluating the implementation of Zero Trust principles within the data plane. Which of the following would be most relevant for the analyst to evaluate?
A. Secured zones
B. Subject role
C. Adaptive identity
D. Threat scope reduction
-
Question 278:
Which of the following has been implemented when a host-based firewall on a legacy Linux system allows connections from only specific internal IP addresses?
A. Compensating control
B. Network segmentation
C. Transfer of risk
D. SNMP traps
-
Question 279:
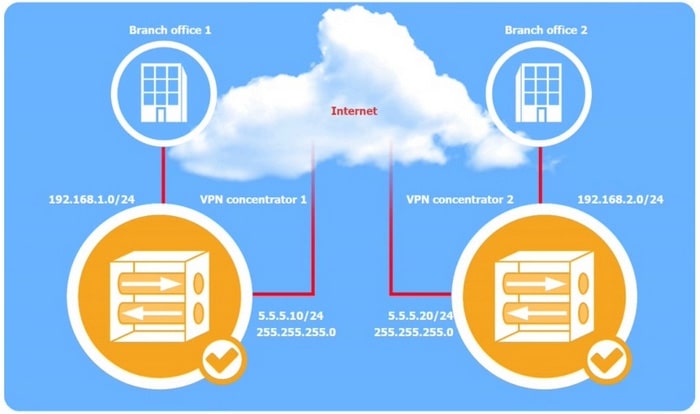
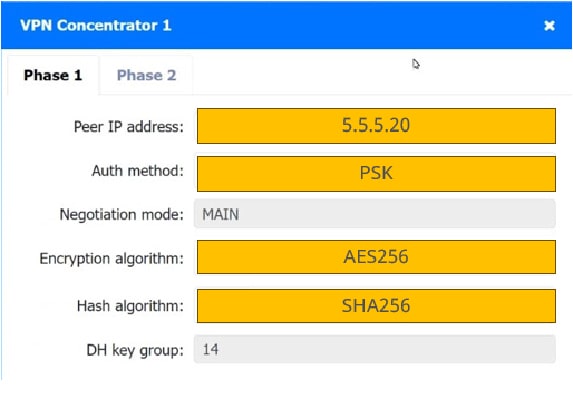
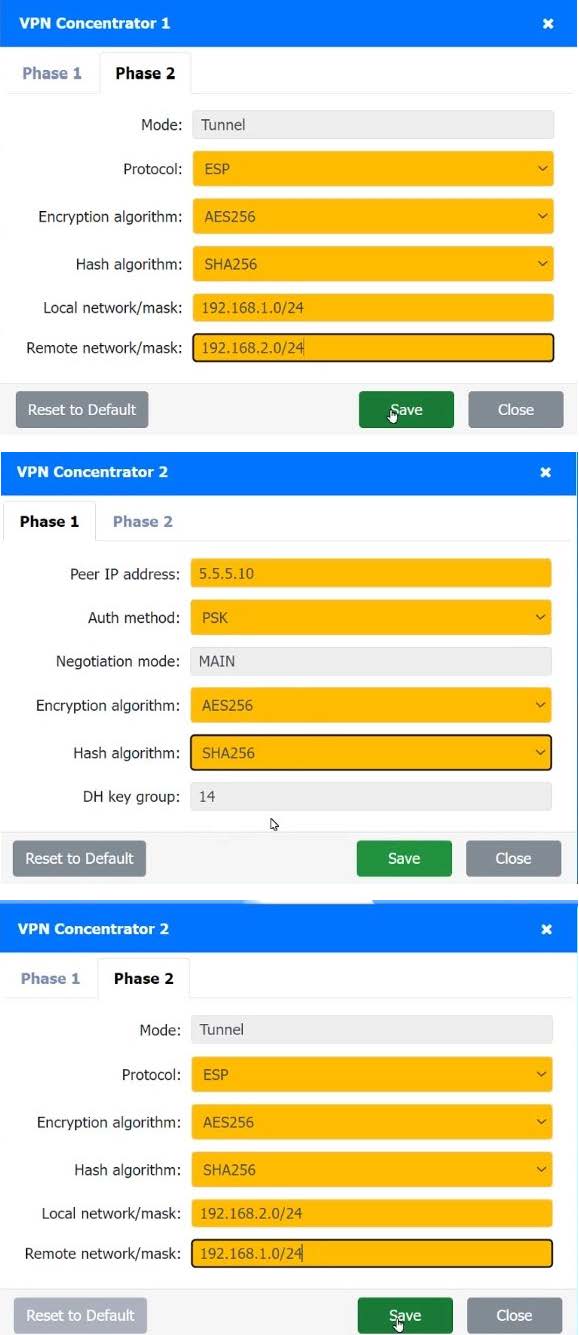
SIMULATION
A systems administrator is configuring a site-to-site VPN between two branch offices. Some of the settings have already been configured correctly. The systems administrator has been provided the following requirements as part of completing the configuration:
1.
Most secure algorithms should be selected
2.
All traffic should be encrypted over the VPN
3.
A secret password will be used to authenticate the two VPN concentrators
INSTRUCTIONS
Click on the two VPN Concentrators to configure the appropriate settings.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A. See the part for all the Solution
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
-
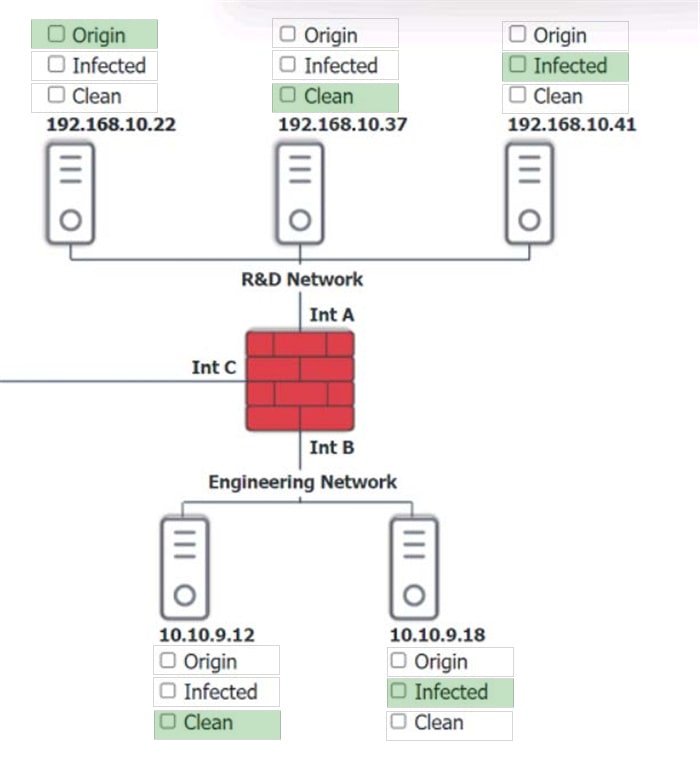
Question 280:
You are security administrator investigating a potential infection on a network.
Click on each host and firewall. Review all logs to determine which host originated the Infecton and then deny each remaining hosts clean or infected.
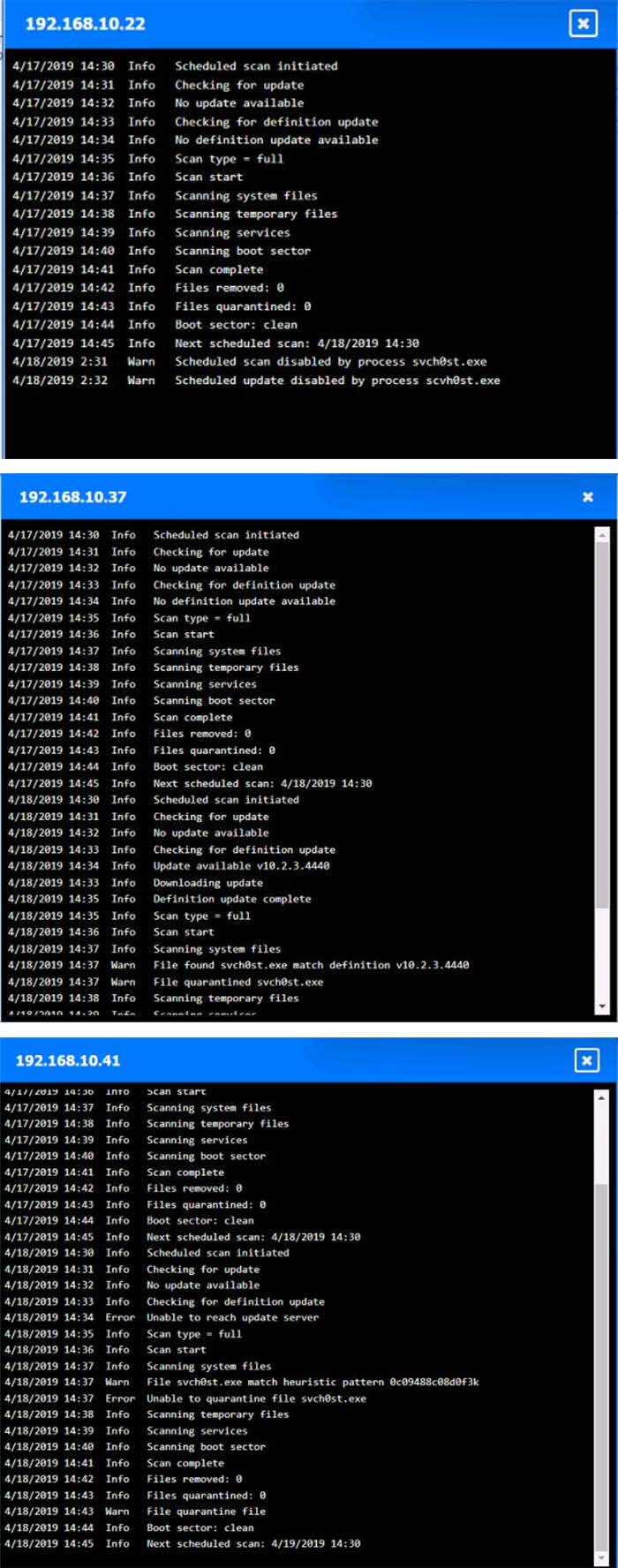
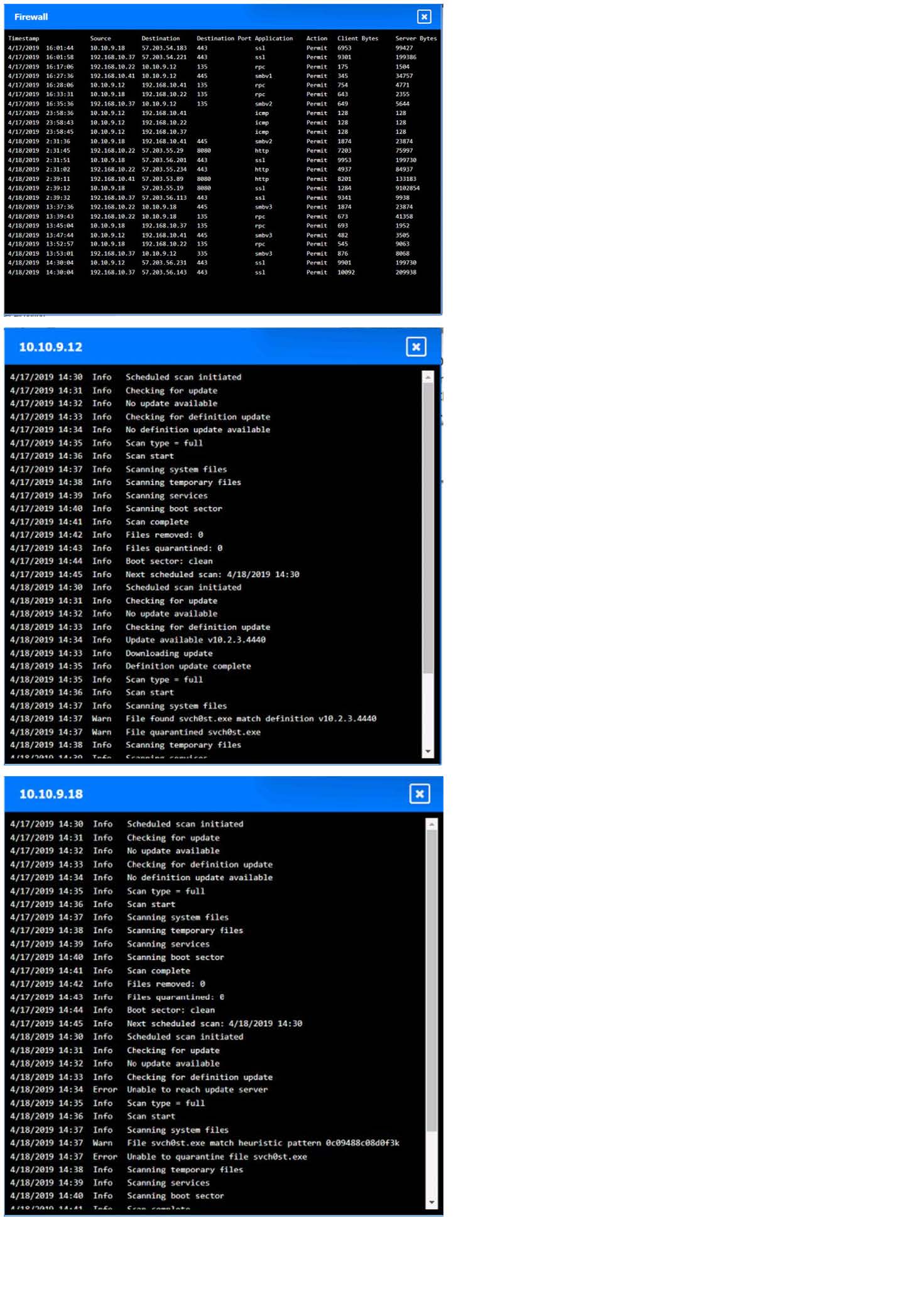
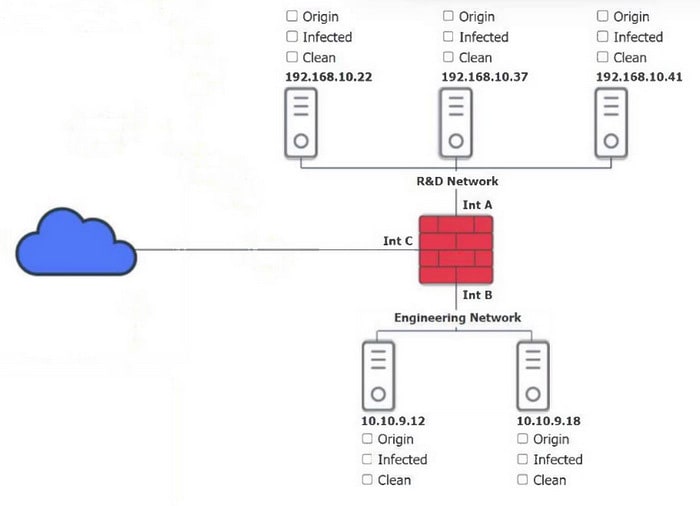
Hot Area:
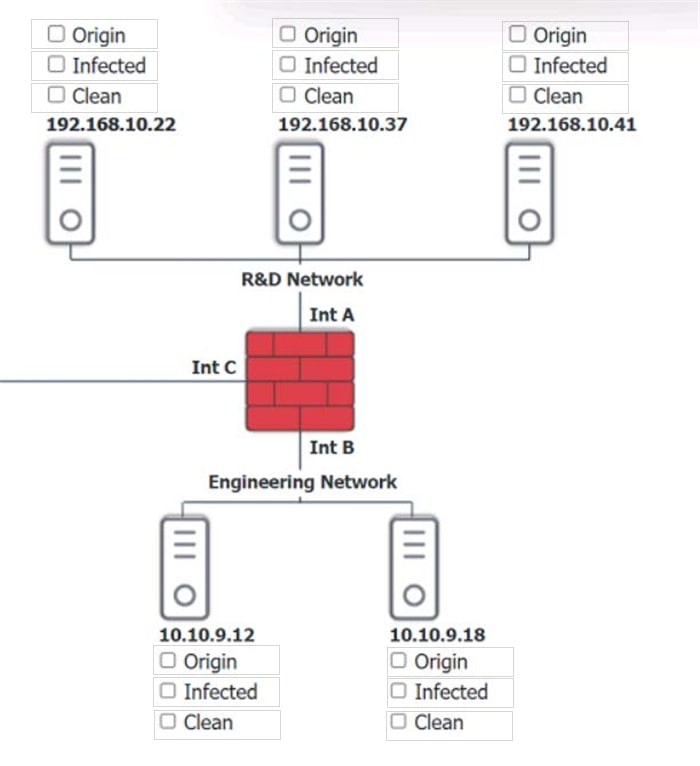
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-701 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.