Exam Details
Exam Code
:SY0-701Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:718 Q&AsLast Updated
:Apr 03, 2025
CompTIA CompTIA Certifications SY0-701 Questions & Answers
-
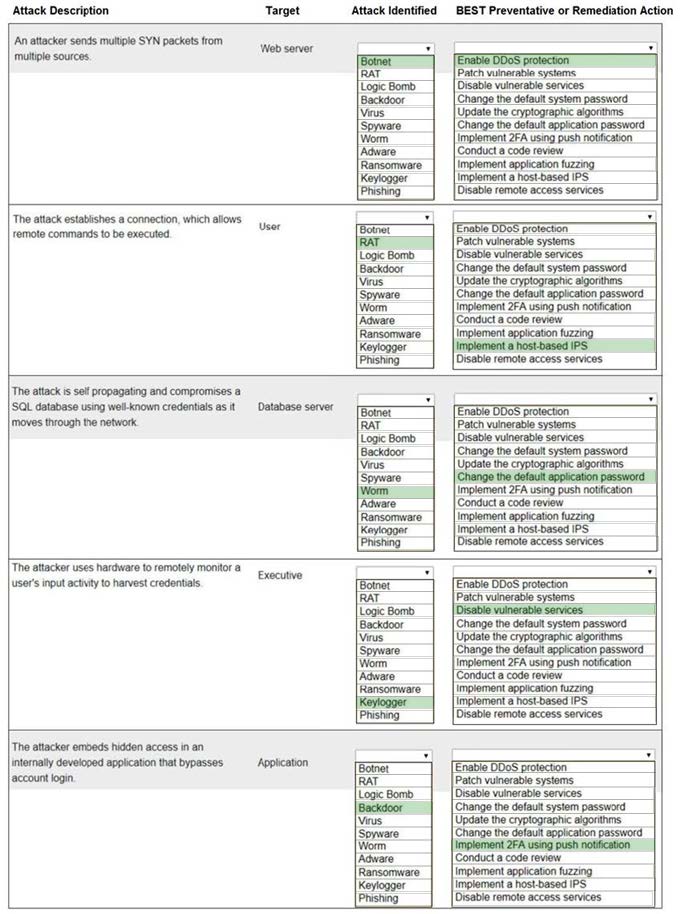
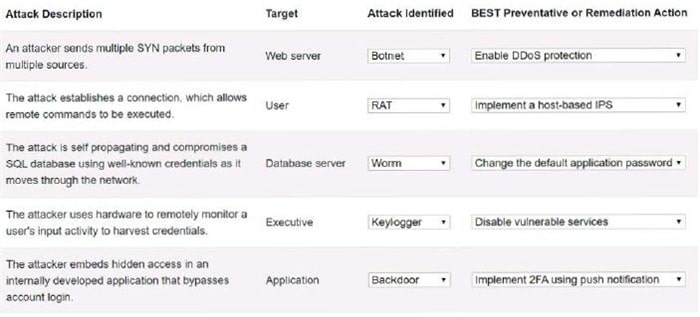
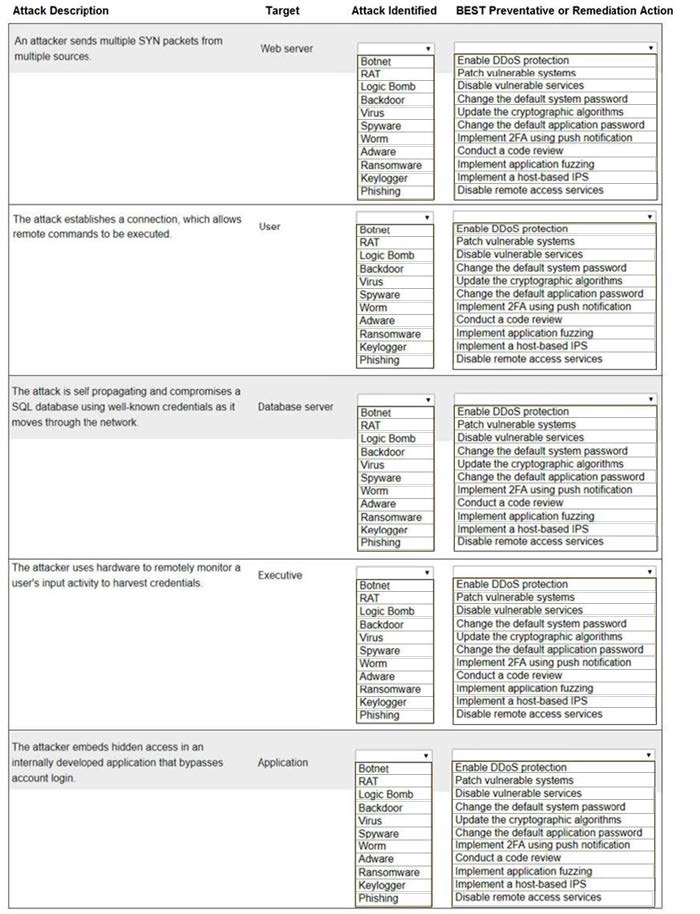
Question 281:
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Hot Area:
-
Question 282:
A security operations center determines that the malicious activity detected on a server is normal. Which of the following activities describes the act of ignoring detected activity in the future?
A. Tuning
B. Aggregating
C. Quarantining
D. Archiving
-
Question 283:
Which of the following vulnerabilities is exploited when an attacker overwrites a register with a malicious address?
A. VM escape
B. SQL injection
C. Buffer overflow
D. Race condition
-
Question 284:
One of a company's vendors sent an analyst a security bulletin that recommends a BIOS update. Which of the following vulnerability types is being addressed by the patch?
A. Virtualization
B. Firmware
C. Application
D. Operating system
-
Question 285:
During an investigation, an incident response team attempts to understand the source of an incident. Which of the following incident response activities describes this process?
A. Analysis
B. Lessons learned
C. Detection
D. Containment
-
Question 286:
Which of the following is used to quantitatively measure the criticality of a vulnerability?
A. CVE
B. CVSS
C. CIA
D. CERT
-
Question 287:
Which of the following is the most likely to be used to document risks, responsible parties, and thresholds?
A. Risk tolerance
B. Risk transfer
C. Risk register
D. Risk analysis
-
Question 288:
A company is discarding a classified storage array and hires an outside vendor to complete the disposal. Which of the following should the company request from the vendor?
A. Certification
B. Inventory list
C. Classification
D. Proof of ownership
-
Question 289:
An organization is leveraging a VPN between its headquarters and a branch location. Which of the following is the VPN protecting?
A. Data in use
B. Data in transit
C. Geographic restrictions
D. Data sovereignty
-
Question 290:
A security engineer is implementing FDE for all laptops in an organization. Which of the following are the most important for the engineer to consider as part of the planning process? (Select two).
A. Key escrow
B. TPM presence
C. Digital signatures
D. Data tokenization
E. Public key management
F. Certificate authority linking
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-701 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.