Exam Details
Exam Code
:156-215.81Exam Name
:Check Point Certified Security Administrator - R81 (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:400 Q&AsLast Updated
:Mar 07, 2025
CheckPoint Checkpoint Certifications 156-215.81 Questions & Answers
-
Question 81:
If an administrator wants to restrict access to a network resource only allowing certain users to access it, and only when they are on a specific network what is the best way to accomplish this?
A. Create an inline layer where the destination is the target network resource Define sub- rules allowing only specific sources to access the target resource
B. Use a "New Legacy User at Location", specifying the LDAP user group that the users belong to, at the desired location
C. Create a rule allowing only specific source IP addresses access to the target network resource.
D. Create an Access Role object, with specific users or user groups specified, and specific networks defined Use this access role as the "Source" of an Access Control rule
-
Question 82:
Bob and Joe both have Administrator Roles on their Gaia Platform. Bob logs in on the WebUI and then Joe logs in through CLI. Choose what BEST describes the following scenario, where Bob and Joe are both logged in:
A. Since they both are logged in on different interfaces, they will both be able to make changes.
B. When Joe logs in. Bob will be logged out automatically.
C. The database will be locked by Bob and Joe will not be able to make any changes.
D. Bob will receive a prompt that Joe has logged in.
-
Question 83:
What is the user ID of a user that have all the privileges of a root user?
A. User ID 1
B. User ID 2
C. User ID 0
D. User ID 99
-
Question 84:
View the rule below. What does the pen-symbol in the left column mean?
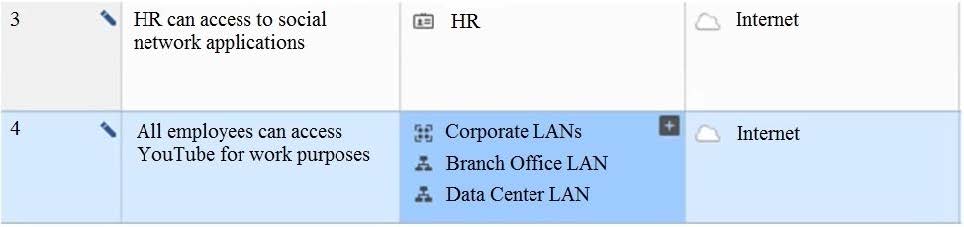
A. Those rules have been published in the current session.
B. Rules have been edited by the logged in administrator, but the policy has not been published yet.
C. Another user has currently locked the rules for editing.
D. The configuration lock is present. Click the pen symbol in order to gain the lock.
-
Question 85:
At what point is the Internal Certificate Authority (ICA) created?
A. During the primary Security Management Server installation process.
B. Upon creation of a certificate
C. When an administrator decides to create one
D. When an administrator initially logs into SmartConsole.
-
Question 86:
True or False: The destination server for Security Gateway logs depends on a Security Management Server configuration.
A. False, log servers are configured on the Log Server General Properties
B. True, all Security Gateways will only forward logs with a SmartCenter Server configuration
C. True, all Security Gateways forward logs automatically to the Security Management Server
D. False, log servers are enabled on the Security Gateway General Properties
-
Question 87:
A layer can support different combinations of blades What are the supported blades:
A. Firewall. URLF, Content Awareness and Mobile Access
B. Firewall (Network Access Control). Application and URL Filtering. Content Awareness and Mobile Access
C. Firewall. NAT, Content Awareness and Mobile Access
D. Firewall (Network Access Control). Application and URL Filtering and Content Awareness
-
Question 88:
Which two of these Check Point Protocols are used by ?
A. ELA and CPD
B. FWD and LEA
C. FWD and CPLOG
D. ELA and CPLOG
-
Question 89:
What is the BEST command to view configuration details of all interfaces in Gaia CLISH?
A. ifconfig -a
B. show interfaces
C. show interfaces detail
D. show configuration interface
-
Question 90:
Fill in the blank: Permanent VPN tunnels can be set on all tunnels in the community, on all tunnels for specific gateways, or__________.
A. On all satellite gateway to satellite gateway tunnels
B. On specific tunnels for specific gateways
C. On specific tunnels in the community
D. On specific satellite gateway to central gateway tunnels
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215.71
Check Point Certified Security Administrator R71156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)156-315.80
Check Point Certified Security Expert - R80 (CCSE)156-315.81
Check Point Certified Security Expert - R81 (CCSE)156-315.81.20
Check Point Certified Security Expert - R81.20156-560
Check Point Certified Cloud Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.81 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.