Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Apr 15, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 1:
What is the difference between attack surface and vulnerability?
A. A vulnerability is a way of taking advantage of a system or resource, and an attack surface is a specific technique utilized by the vulnerability.
B. An attack surface is a way of taking advantage of a system or resource, and a vulnerability is a specific technique utilized by the vulnerability.
C. An attack surface describes how software or a system is exposed to potential attacks, and a vulnerability is an actual weakness that exposes the potential risk.
D. A vulnerability describes how software or a system is exposed to potential attacks, and an attack surface is an actual weakness that exposes the potential risk.
-
Question 2:
What is a description of "phishing" as a social engineering attack?
A. Fake Social Security Administration personnel contact random individuals, inform them that there has been a computer problem on their end, and ask that those individuals confirm their Social Security Number, all for the purpose of committing identity theft.
B. A hacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. The recipient is then tricked into clicking a malicious link.
C. The attacker focuses on creating a good pretext, or a fabricated scenario, that is used to try and steal victims
-
Question 3:
Which technique is a low-bandwidth attack?
A. evasion
B. phishing
C. session hijacking
D. social engineering
-
Question 4:
What are two differences between tampered disk images and untampered disk images? (Choose two.)
A. The image is tampered if the stored hash and the computed hash are identical.
B. Tampered images are used as an element for the root cause analysis report.
C. Untampered images can be used as law enforcement evidence.
D. Tampered images are used in a security Investigation process.
E. The image is untampered if the existing stored hash matches the computed one.
-
Question 5:
What do host-based firewalls protect workstations from?
A. viruses
B. unwanted traffic
C. zero-day vulnerabilities
D. malicious web scripts
-
Question 6:
Which option describes indicators of attack?
A. blocked phishing attempt on a company
B. spam emails on an employee workstation
C. virus detection by the AV software
D. malware reinfection within a few minutes of removal
-
Question 7:
Refer to the exhibit.
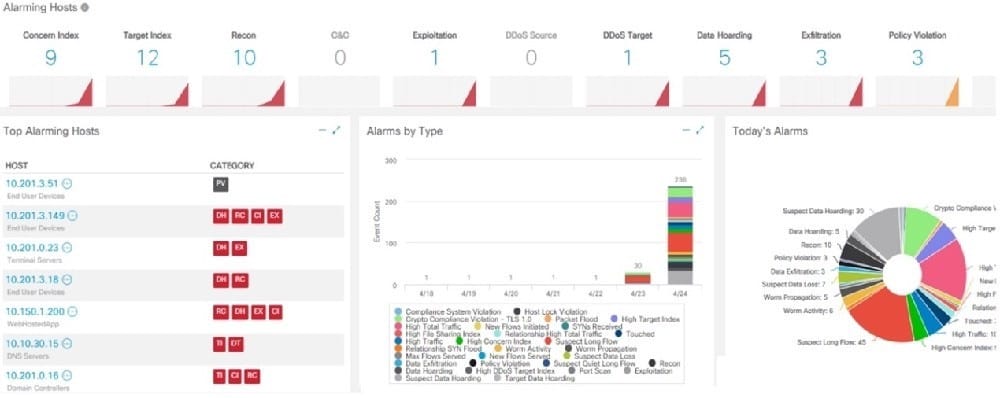
A company's user HTTP connection to a malicious site was blocked according to configured policy. What is the source technology used for this measure?
A. network application control
B. firewall
C. IPS
D. web proxy
-
Question 8:
Refer to the exhibit.

An attacker gained initial access to the company's network and ran an Nmap scan to advance with the lateral movement technique and to search the sensitive data. Which two elements can an attacker identify from the scan? (Choose two.)
A. workload and the configuration details
B. functionality and purpose of the server
C. number of users and requests that the server is handling
D. running services
E. user accounts and SID
-
Question 9:
Refer to the exhibit.
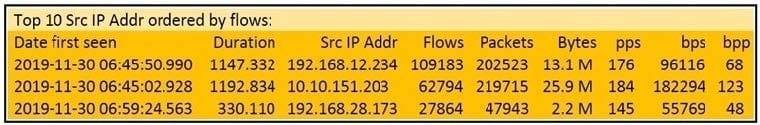
What is the outcome of the command?
A. TCP rule that detects TCP packets with the ACK flag in an external FTP server
B. TCP rule that detects TCP packets with a SYN flag in the internal network
C. TCP rule that detects TCP packets with a ACK flag in the internal network
D. TCP rule that detects TCP packets with the SYN flag in an external FTP server
-
Question 10:
What are two categories of DDoS attacks? (Choose two.)
A. direct
B. reflected
C. split brain
D. scanning
E. phishing
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.