Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Mar 21, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 391:
A forensic investigator is analyzing a recent breach case. An external USB drive was discovered to be connected and transmitting the data outside of the organization, and the owner of the USB drive could not be identified. Video surveillance shows six people during a two-month period had close contact with the affected asset. How must this type of evidence be categorized?
A. best evidence
B. indirect evidence
C. direct evidence
D. corroborative evidence
-
Question 392:
An engineer configured regular expression ".*\.([Dd][Oo][Cc]|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1.[01]" on Cisco ASA firewall. What does this regular expression do?
A. It captures .doc, .xls, and .pdf files in HTTP v1.0 and v1.1.
B. It captures documents in an HTTP network session.
C. It captures Word, Excel, and PowerPoint files in HTTP v1.0 and v1.1.
D. It captures .doc, .xls, and .ppt files extensions in HTTP v1.0.
-
Question 393:
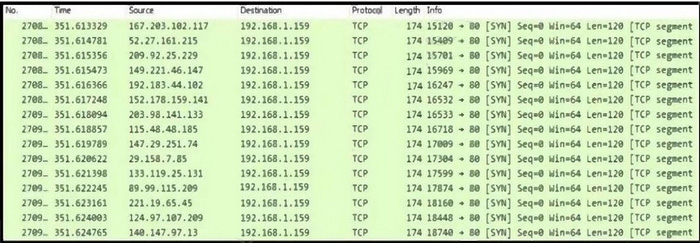
Refer to exhibit. An engineer is investigating an intrusion and is analyzing the pcap file. Which two key elements must an engineer consider? (Choose two.)
A. variable "info" field and unchanging sequence number
B. high volume of SYN packets with very little variance in time
C. SYN packets acknowledged from several source IP addresses
D. identical length of 120 and window size (64)
E. same source IP address with a destination port 80
-
Question 394:
A user reports difficulties accessing certain external web pages. When an engineer examines traffic to and from the external domain in full packet captures, they notice that many SYNs have the same sequence number, source, and destination IP address, but they have different payloads. What is causing this situation?
A. failure of the full packet capture solution
B. misconfiguration of a web filter
C. insufficient network resources
D. TCP injection
-
Question 395:
What is the impact of false negative alerts when compared to true negative alerts?
A. A false negative is someone trying to hack into the system and no alert is raised, and a true negative is an event that never happened and an alert was not raised.
B. A true negative is an alert for an exploit attempt when no attack was detected, and a false negative is when no attack happens and an alert is still raised.
C. A true negative is a legitimate attack that triggers a brute force alert, and a false negative is when no alert and no attack is occurring.
D. A false negative is an event that alerts for injection attack when no attack is happening, and a true negative is an attack that happens and an alert that is appropriately raised.
-
Question 396:
What matches the regular expression r(ege)+x?
A. r(ege)x
B. regeegex
C. rx
D. rege+x
-
Question 397:
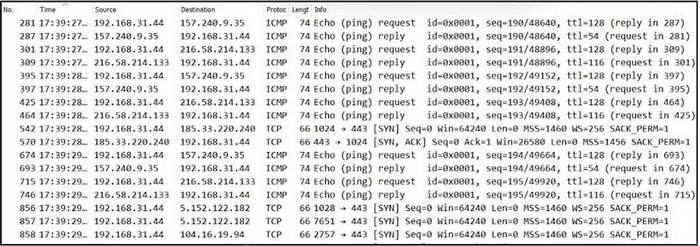
Refer to the exhibit. What is occurring in this network traffic?
A. legitimate network traffic
B. flood of SYN-ACK packets
C. ICMP flood
D. flood of SYN packets
-
Question 398:
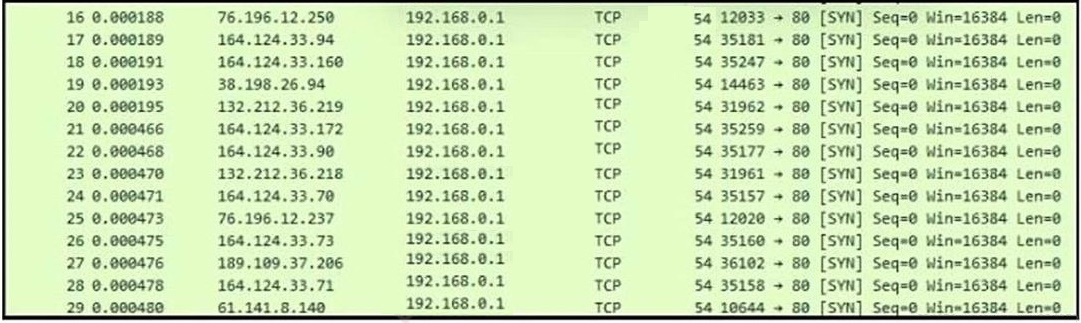
Refer to the exhibit. What is occurring?
A. ARP spoofing attack
B. man-in-the-middle attack
C. brute-force attack
D. denial-of-service attack
-
Question 399:
Which action matches the weaponization step of the Cyber Kill Chain Model?
A. Develop a specific malware to exploit a vulnerable server.
B. Construct a trojan and deliver it to the victim.
C. Match a known script to a vulnerability.
D. Scan open services and ports on a server.
-
Question 400:
What describes the framework that enables to control user access to critical information in the heterogenous technology environments?
A. vulnerability scanner
B. configuration management
C. mobile device management
D. identity and access management
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.