Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Mar 21, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 11:
What is the purpose of a ransomware attack?
A. to escalate privileges
B. to make files inaccessible by encrypting the data
C. to send keystrokes to a threat actor
D. to decrypt encrypted data and disks
-
Question 12:
Refer to the exhibit.
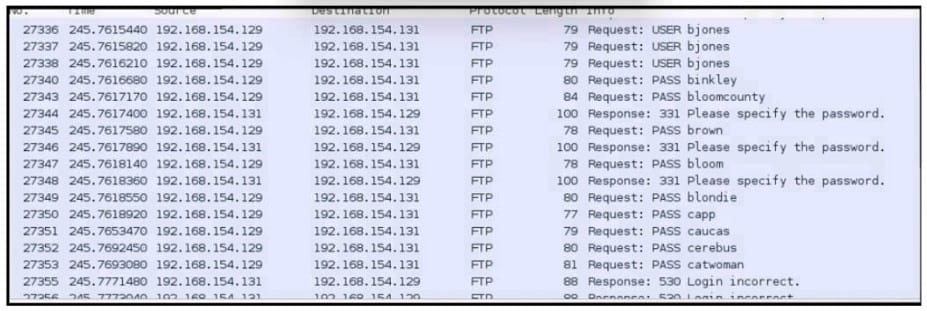
A SOC engineer is analyzing the provided Cuckoo Sandbox report for a file that has been downloaded from an URL, received via email. What is the state of this file?
A. The file was identified as PE32 executable for MS Windows and the Yara filed lists it as Trojan.
B. The file was detected as executable and was matched by PEiD threat signatures for further analysis.
C. The file was detected as executable, but no suspicious features are identified.
D. The calculated SHA256 hash of the file was matched and identified as malicious.
-
Question 13:
An information security analyst inspects the .pcap file and observes encrypted unusual SSH traffic flow over nonstandard ports. Which technology makes this behavior feasible?
A. NAT
B. tunneling
C. P2P
D. TOR
-
Question 14:
How can TOR impact data visibility inside an organization?
A. no impact
B. increases security
C. increases data integrity
D. decreases visibility
-
Question 15:
Refer to the exhibit.
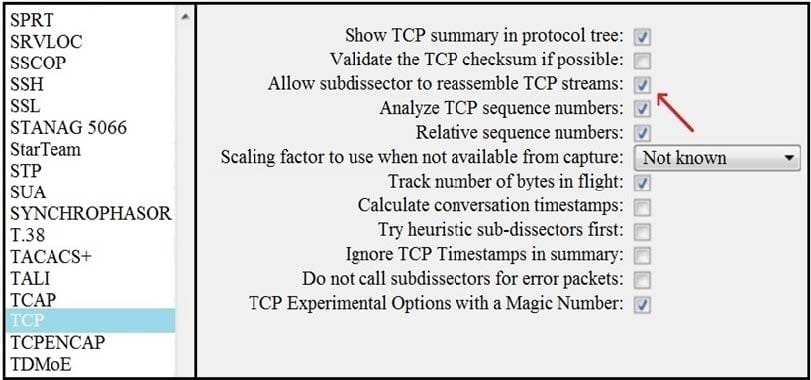
An engineer needs to identify certificate information on server1234567890. What does the exhibit indicate?
A. Elliptic-curve cryptography is used for the public keys.
B. Key exchange is not secure as the SHA256 hashing algorithm is used.
C. The certificate is signed by GTS CA on May 24 and is invalid.
D. Asymmetric cryptography is used for key exchange.
-
Question 16:
What is the functionality of an IDS?
A. forensic tool used to perform an in-depth analysis and debugging
B. software or device which monitors and identifies malicious network activity
C. device or software that detects and blocks suspicious files
D. endpoint protection software that prevents viruses and malware
-
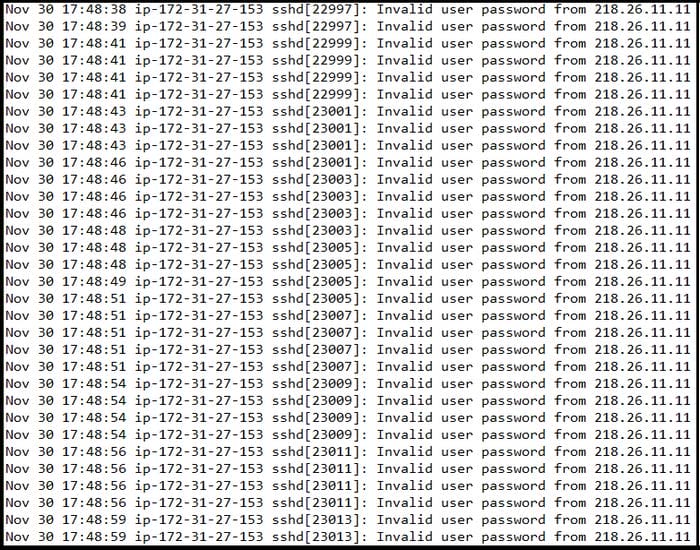
Question 17:
Refer to the exhibit.
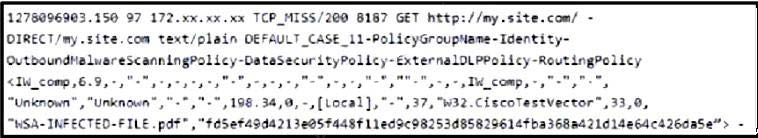
Which technology produced the log?
A. antivirus
B. IPS/IDS
C. firewall
D. proxy
-
Question 18:
Refer to exhibit.
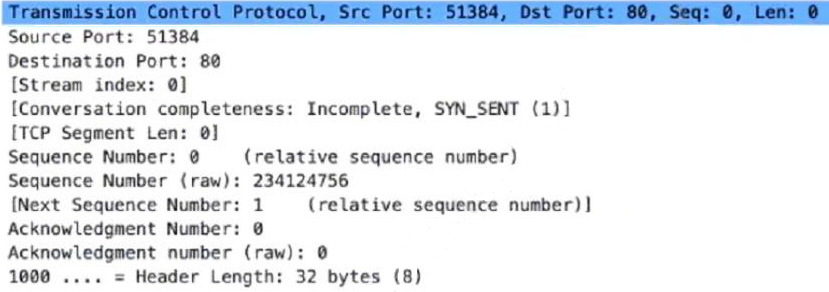
Which alert is identified from this packet?
A. SSDP amplification
B. SYN flood
C. TCP fragmentation attack
D. Fraggle attack
-
Question 19:
Refer to the exhibit.
What should be interpreted from this packet capture?
A. 192.168.7.138 is sending a packet from port 1983 to port 1983 of IP address 192.168.1.18 using UDP protocol.
B. 192.168.7.138 is sending a packet from port 1983 to port 1983 of IP address 192.168.1.18 using TCP protocol.
C. 192.168.1.18 is sending a packet from port 1983 to port 1983 of IP address 192.168.7.138 using UDP protocol.
D. 192.168.1.18 is sending a packet from port 1983 to port 1983 of IP address 192.168.7.138 using TCP protocol.
-
Question 20:
Refer to the exhibit.

An engineer received a ticket about a slowdown of a web application. During analysis of traffic, the engineer suspects a possible attack on a web server. How should the engineer interpret the Wireshark traffic capture?
A. 10.128.0.2 sends HTTP / FORBIDDEN / 1.1 and GET requests, and the target responds with HTTP/1.1 200 OK and HTTP/1.1 403. This is an HTTP cache bypass attack.
B. 10.0.0.2 sends GET / HTTP / 1.1 and POST requests, and the target responds with HTTP/1.1 200 OK and HTTP/1.1 403 accordingly. This is an HTTP flood attempt.
C. 10.128.0.2 sends POST / HTTP / 1.1 and GET requests, and the target responds with HTTP/1.1 200 OK and HTTP/1.1 403 accordingly. This is an HTTP Reverse Bandwidth flood.
D. 10.0.0.2 sends HTTP / FORBIDDEN / 1.1 and POST requests, while the target responds with HTTP/1.1 200 GET and HTTP/1.1 403. This is an HTTP GET flood attack.
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.