Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Mar 21, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 41:
According to CVSS, what is a description of the attack vector score?
A. It depends on how far away the attacker is located and the vulnerable component.
B. The metric score will be larger when a remote attack is more likely.
C. It depends on how many physical and logical manipulations are possible on a vulnerable component.
D. The metric score will be larger when it is easier to physically touch or manipulate the vulnerable component.
-
Question 42:
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
A. context
B. session
C. laptop
D. firewall logs
E. threat actor
-
Question 43:
A SOC analyst detected connections to known CandC and port scanning activity to main HR database servers from one of the HR endpoints, via Cisco StealthWatch. What are the two next steps of the SOC team according to the NIST.SP80061 incident handling process? (Choose two.)
A. Update antivirus signature databases on affected endpoints to block connections to CandC.
B. Isolate affected endpoints and take disk images for analysis.
C. Block connection to this CandC server on the perimeter next-generation firewall.
D. Provide security awareness training to HR managers and employees
E. Detect the attack vector and analyze CandC connections.
-
Question 44:
The SOC team has confirmed a potential indicator of compromise on an isolated endpoint. The team has narrowed the potential malware type to a new trojan family. According to the NIST Computer Security Incident Handling Guide, what is the next step in handling the event?
A. Perform an AV scan on the infected endpoint.
B. Isolate the infected endpoint from the network.
C. Prioritize incident handling based on the impact.
D. Analyze the malware behavior.
-
Question 45:
Which element is included in an incident response plan as stated in NIST.SP800-617
A. security of sensitive information
B. individual approach to incident response
C. consistent threat identification
D. approval of senior management
-
Question 46:
An engineer is working on a ticket for an incident from the incident management team. A week ago, an external web application was targeted by a DDoS attack. Server resources were exhausted and after two hours, it crashed. An engineer was able to identify the attacker and technique used. Three hours after the attack, the server was restored and the engineer recommended implementing mitigation by Blackhole filtering and transferred the incident ticket back to the IR team. According to NIST.SP800-61, at which phase of the incident response did the engineer finish work?
A. post-incident activity
B. preparation
C. detection and analysis
D. containment, eradication, and recovery
-
Question 47:
A user received a malicious email attachment named "DS045-report1122345.exe" and executed it. In which step of the Cyber Kill Chain is this event?
A. reconnaissance
B. delivery
C. weaponization
D. installation
-
Question 48:
Which action matches the weaponization step of the Cyber Kill Chain model?
A. Research data on a specific vulnerability.
B. Test and construct the appropriate malware to launch the attack.
C. Scan a host to find open ports and vulnerabilities.
D. Construct the appropriate malware and deliver it to the victim.
-
Question 49:
A cyberattacker notices a security flaw in a software that a company is using. They decide to tailor a specific worm to exploit this flaw and extract saved passwords from the software. To which category of the Cyber Kill Chain model does this event belong?
A. weaponization
B. reconnaissance
C. delivery
D. exploitation
-
Question 50:
Refer to the exhibit.
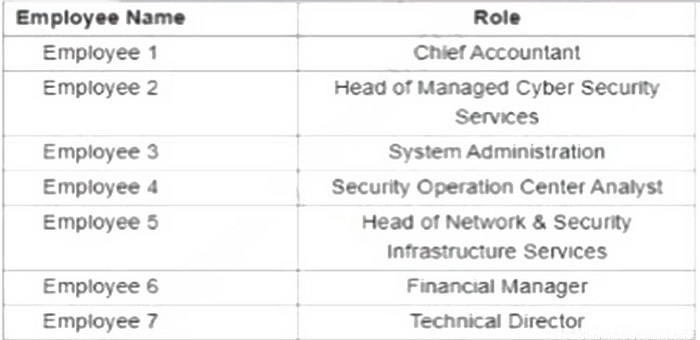
A suspicious IP address is tagged by Threat Intelligence as a brute-force attempt source. After the attacker produces many of failed login entries it successfully compromises the account. Which stakeholder is responsible for the incident response detection step?
A. employee 2
B. employee 3
C. employee 4
D. employee 5
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.