Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Apr 15, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 151:
What describes the concept of data consistently and readily being accessible for legitimate users?
A. integrity
B. availability
C. accessibility
D. confidentiality
-
Question 152:
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
A. NetScout
B. tcpdump
C. SolarWinds
D. netsh
-
Question 153:
What is the principle of defense-in-depth?
A. Agentless and agent-based protection for security are used.
B. Several distinct protective layers are involved.
C. Access control models are involved.
D. Authentication, authorization, and accounting mechanisms are used.
-
Question 154:
Which technology should be used to implement a solution that makes routing decisions based on HTTP header, uniform resource identifier, and SSL session ID attributes?
A. AWS
B. IIS
C. Load balancer
D. Proxy server
-
Question 155:
Which two elements of the incident response process are stated in NIST SP 800-61 r2? (Choose two.)
A. detection and analysis
B. post-incident activity
C. vulnerability scoring
D. vulnerability management
E. risk assessment
-
Question 156:
An engineer is addressing a connectivity issue between two servers where the remote server is unable to establish a successful session. Initial checks show that the remote server is not receiving an SYN-ACK while establishing a session by
sending the first SYN.
What is causing this issue?
A. incorrect TCP handshake
B. incorrect UDP handshake
C. incorrect OSI configuration
D. incorrect snaplen configuration
-
Question 157:
Refer to the exhibit.
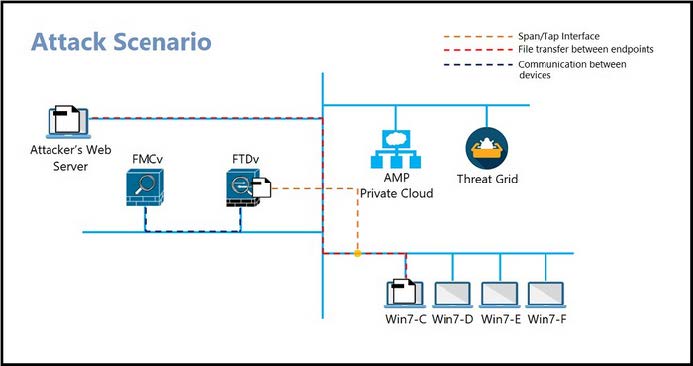
A workstation downloads a malicious docx file from the Internet and a copy is sent to FTDv. The FTDv sends the file hash to FMC and the tile event is recorded What would have occurred with stronger data visibility?
A. The traffic would have been monitored at any segment in the network.
B. Malicious traffic would have been blocked on multiple devices
C. An extra level of security would have been in place
D. Detailed information about the data in real time would have been provided
-
Question 158:
Refer to the exhibit.
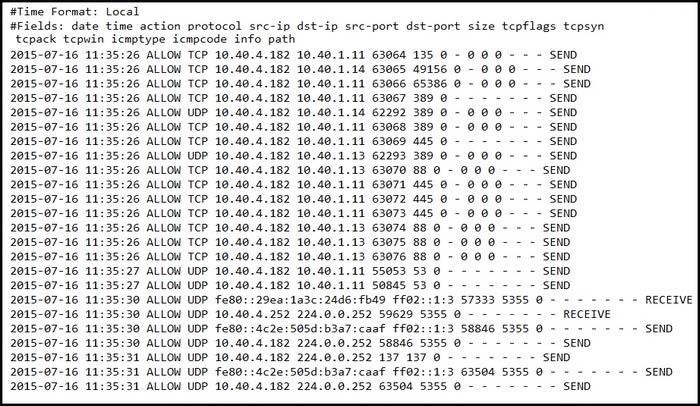
An engineer received an event log file to review. Which technology generated the log?
A. NetFlow
B. proxy
C. firewall
D. IDS/IPS
-
Question 159:
What does cyber attribution identify in an investigation?
A. cause of an attack
B. exploit of an attack
C. vulnerabilities exploited
D. threat actors of an attack
-
Question 160:
What are two denial-of-service (DoS) attacks? (Choose two)
A. port scan
B. SYN flood
C. man-in-the-middle
D. phishing
E. teardrop
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.