Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Apr 15, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 271:
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external penmeter data flows contain records, writings, and artwork Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age. The engineer must identify protected data. Which two types of data must be identified'? (Choose two.)
A. SOX
B. PII
C. PHI
D. PCI
E. copyright
-
Question 272:
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
A. social engineering
B. eavesdropping
C. piggybacking
D. tailgating
-
Question 273:
What is indicated by an increase in IPv4 traffic carrying protocol 41 ?
A. additional PPTP traffic due to Windows clients
B. unauthorized peer-to-peer traffic
C. deployment of a GRE network on top of an existing Layer 3 network
D. attempts to tunnel IPv6 traffic through an IPv4 network
-
Question 274:
Refer to the exhibit.

In which Linux log file is this output found?
A. /var/log/authorization.log
B. /var/log/dmesg
C. var/log/var.log
D. /var/log/auth.log
-
Question 275:
When an event is investigated, which type of data provides the investigate capability to determine if data exfiltration has occurred?
A. full packet capture
B. NetFlow data
C. session data
D. firewall logs
-
Question 276:
A developer is working on a project using a Linux tool that enables writing processes to obtain these required results:
If the process is unsuccessful, a negative value is returned. If the process is successful, 0 value is returned to the child process, and the process ID is sent to the parent process.
Which component results from this operation?
A. parent directory name of a file pathname
B. process spawn scheduled
C. macros for managing CPU sets
D. new process created by parent process
-
Question 277:
A company receptionist received a threatening call referencing stealing assets and did not take any action assuming it was a social engineering attempt. Within 48 hours, multiple assets were breached, affecting the confidentiality of sensitive information. What is the threat actor in this incident?
A. company assets that are threatened
B. customer assets that are threatened
C. perpetrators of the attack
D. victims of the attack
-
Question 278:
Refer to the exhibit.

Which type of log is displayed?
A. IDS
B. proxy
C. NetFlow
D. sys
-
Question 279:
What is an attack surface as compared to a vulnerability?
A. any potential danger to an asset
B. the sum of all paths for data into and out of the environment
C. an exploitable weakness in a system or its design
D. the individuals who perform an attack
-
Question 280:
Refer to the exhibit.
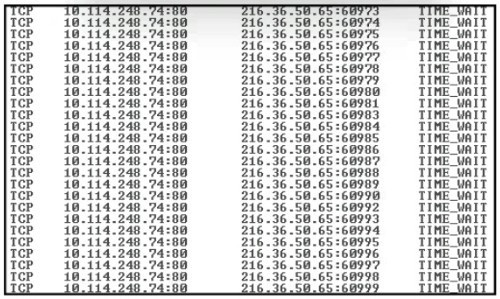
An engineer received a ticket about a slowed-down web application The engineer runs the #netstat -an command. How must the engineer interpret the results?
A. The web application is receiving a common, legitimate traffic
B. The engineer must gather more data.
C. The web application server is under a denial-of-service attack.
D. The server is under a man-in-the-middle attack between the web application and its database
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.