Exam Details
Exam Code
:300-215Exam Name
:Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps (CBRFIR)Certification
:CyberOps ProfessionalVendor
:CiscoTotal Questions
:59 Q&AsLast Updated
:Mar 25, 2025
Cisco CyberOps Professional 300-215 Questions & Answers
-
Question 11:
What are YARA rules based upon?
A. binary patterns
B. HTML code
C. network artifacts
D. IP addresses
-
Question 12:

Refer to the exhibit. According to the Wireshark output, what are two indicators of compromise for detecting an Emotet malware download? (Choose two.)
A. Domain name:iraniansk.com
B. Server: nginx
C. Hash value: 5f31ab113af08=1597090577
D. filename= "Fy.exe"
E. Content-Type: application/octet-stream
-
Question 13:
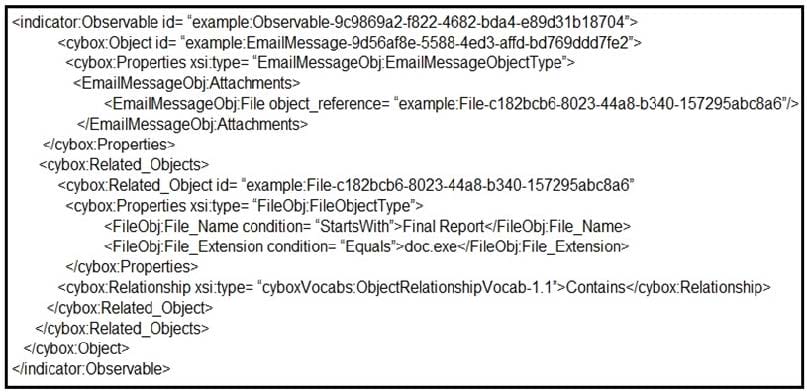
Refer to the exhibit. Which determination should be made by a security analyst?
A. An email was sent with an attachment named "Grades.doc.exe".
B. An email was sent with an attachment named "Grades.doc".
C. An email was sent with an attachment named "Final Report.doc".
D. An email was sent with an attachment named "Final Report.doc.exe".
-
Question 14:
A security team received reports of users receiving emails linked to external or unknown URLs that are non-returnable and non-deliverable. The ISP also reported a 500% increase in the amount of ingress and egress email traffic received. After detecting the problem, the security team moves to the recovery phase in their incident response plan. Which two actions should be taken in the recovery phase of this incident? (Choose two.)
A. verify the breadth of the attack
B. collect logs
C. request packet capture
D. remove vulnerabilities
E. scan hosts with updated signatures
-
Question 15:
Which magic byte indicates that an analyzed file is a pdf file?
A. cGRmZmlsZQ
B. 706466666
C. 255044462d
D. 0a0ah4cg
-
Question 16:
An engineer received a call to assist with an ongoing DDoS attack. The Apache server is being targeted, and availability is compromised. Which step should be taken to identify the origin of the threat?
A. An engineer should check the list of usernames currently logged in by running the command $ who | cut –d’ ‘ -f1| sort | uniq
B. An engineer should check the server's processes by running commands ps -aux and sudo ps -a.
C. An engineer should check the services on the machine by running the command service -status-all.
D. An engineer should check the last hundred entries of a web server with the command sudo tail -100 /var/log/apache2/access.log.
-
Question 17:
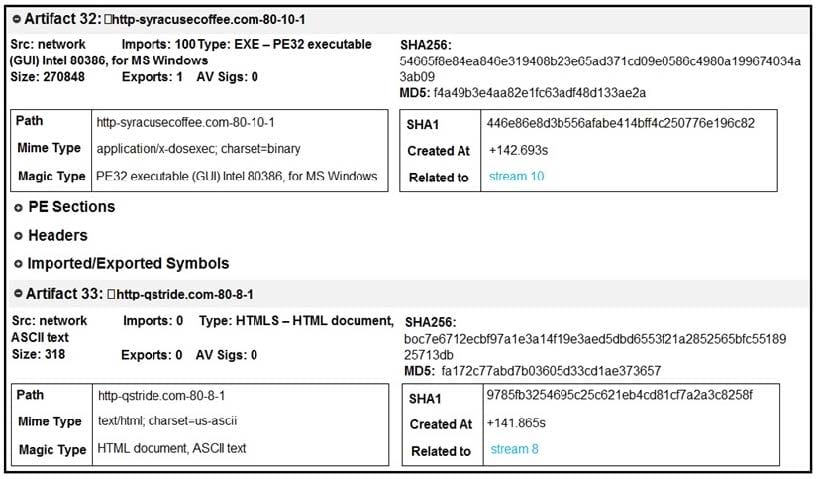
Refer to the exhibit. What do these artifacts indicate?
A. An executable file is requesting an application download.
B. A malicious file is redirecting users to different domains.
C. The MD5 of a file is identified as a virus and is being blocked.
D. A forged DNS request is forwarding users to malicious websites.
-
Question 18:
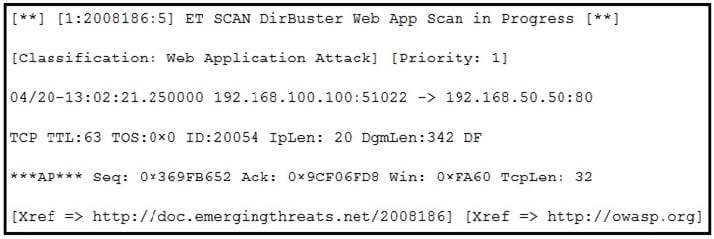
Refer to the exhibit. According to the SNORT alert, what is the attacker performing?
A. brute-force attack against the web application user accounts
B. XSS attack against the target webserver
C. brute-force attack against directories and files on the target webserver
D. SQL injection attack against the target webserver
-
Question 19:

Refer to the exhibit. Which type of code created the snippet?
A. VB Script
B. Python
C. PowerShell
D. Bash Script
-
Question 20:
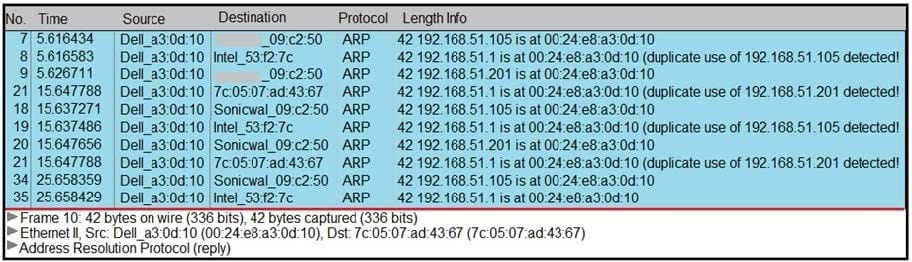
Refer to the exhibit. A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
A. DNS spoofing; encrypt communication protocols
B. SYN flooding, block malicious packets
C. ARP spoofing; configure port security
D. MAC flooding; assign static entries
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-215 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.