Exam Details
Exam Code
:300-215Exam Name
:Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps (CBRFIR)Certification
:CyberOps ProfessionalVendor
:CiscoTotal Questions
:59 Q&AsLast Updated
:Mar 25, 2025
Cisco CyberOps Professional 300-215 Questions & Answers
-
Question 41:
Over the last year, an organization's HR department has accessed data from its legal department on the last day of each month to create a monthly activity report. An engineer is analyzing suspicious activity alerted by a threat intelligence platform that an authorized user in the HR department has accessed legal data daily for the last week. The engineer pulled the network data from the legal department's shared folders and discovered above average-size data dumps. Which threat actor is implied from these artifacts?
A. privilege escalation
B. internal user errors
C. malicious insider
D. external exfiltration
-
Question 42:
A website administrator has an output of an FTP session that runs nightly to download and unzip files to a local staging server. The download includes thousands of files, and the manual process used to find how many files failed to download is time-consuming. The administrator is working on a PowerShell script that will parse a log file and summarize how many files were successfully downloaded versus ones that failed. Which script will read the contents of the file one line at a time and return a collection of objects?
A. Get-Content-Folder \\Server\FTPFolder\Logfiles\ftpfiles.log | Show-From "ERROR", "SUCCESS"
B. Get-Content –ifmatch \\Server\FTPFolder\Logfiles\ftpfiles.log | Copy-Marked “ERROR”, “SUCCESS”
C. Get-Content –Directory \\Server\FTPFolder\Logfiles\ftpfiles.log | Export-Result “ERROR”, “SUCCESS”
D. Get-Content –Path \\Server\FTPFolder\Logfiles\ftpfiles.log | Select-String “ERROR”, “SUCCESS”
-
Question 43:
What is the steganography anti-forensics technique?
A. hiding a section of a malicious file in unused areas of a file
B. changing the file header of a malicious file to another file type
C. sending malicious files over a public network by encapsulation
D. concealing malicious files in ordinary or unsuspecting places
-
Question 44:
A security team receives reports of multiple files causing suspicious activity on users' workstations. The file attempted to access highly confidential information in a centralized file server. Which two actions should be taken by a security analyst to evaluate the file in a sandbox? (Choose two.)
A. Inspect registry entries
B. Inspect processes.
C. Inspect file hash.
D. Inspect file type.
E. Inspect PE header.
-
Question 45:
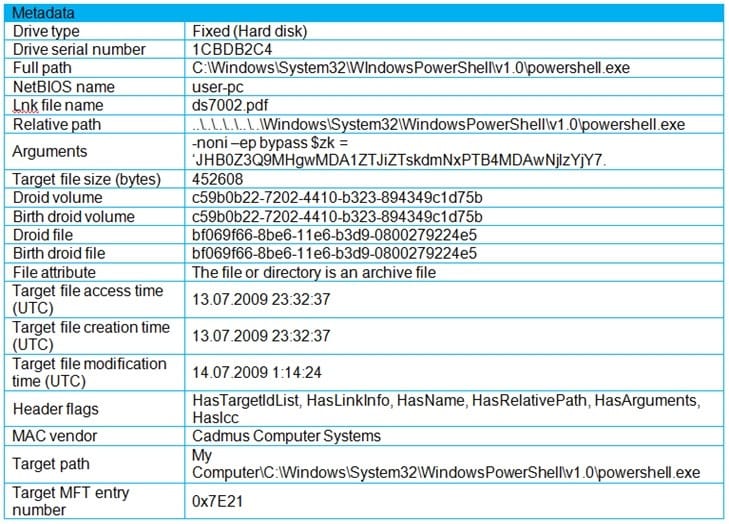
Refer to the exhibit. An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked by email security as suspicious. What is the next step an engineer should take?
A. Delete the suspicious email with the attachment as the file is a shortcut extension and does not represent any threat.
B. Upload the file to a virus checking engine to compare with well-known viruses as the file is a virus disguised as a legitimate extension.
C. Quarantine the file within the endpoint antivirus solution as the file is a ransomware which will encrypt the documents of a victim.
D. Open the file in a sandbox environment for further behavioral analysis as the file contains a malicious script that runs on execution.
-
Question 46:
An investigator is analyzing an attack in which malicious files were loaded on the network and were undetected. Several of the images received during the attack include repetitive patterns. Which anti-forensic technique was used?
A. spoofing
B. obfuscation
C. tunneling
D. steganography
-
Question 47:
A security team detected an above-average amount of inbound tcp/135 connection attempts from unidentified senders. The security team is responding based on their incident response playbook. Which two elements are part of the eradication phase for this incident? (Choose two.)
A. anti-malware software
B. data and workload isolation
C. centralized user management
D. intrusion prevention system
E. enterprise block listing solution
-
Question 48:
Which tool conducts memory analysis?
A. MemDump
B. Sysinternals Autoruns
C. Volatility
D. Memoryze
-
Question 49:
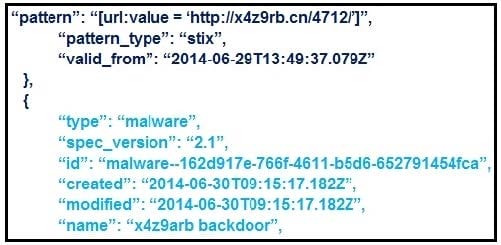
Refer to the exhibit. What is the IOC threat and URL in this STIX JSON snippet?
A. malware; `http://x4z9arb.cn/4712/'
B. malware; x4z9arb backdoor
C. x4z9arb backdoor; http://x4z9arb.cn/4712/
D. malware; malware--162d917e-766f-4611-b5d6-652791454fca
E. stix; `http://x4z9arb.cn/4712/'
-
Question 50:
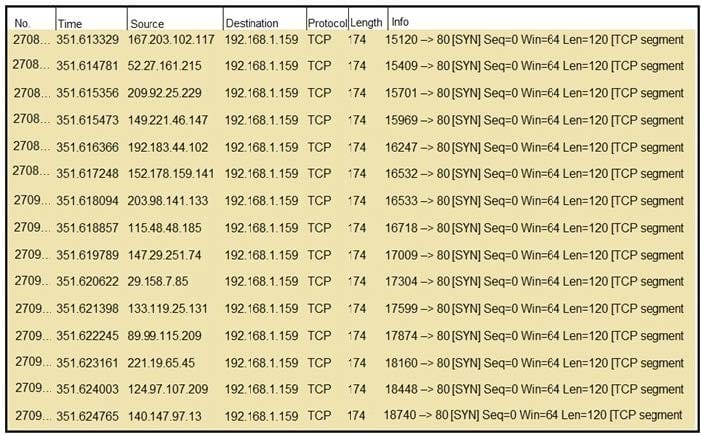
Refer to the exhibit. What should an engineer determine from this Wireshark capture of suspicious network traffic?
A. There are signs of SYN flood attack, and the engineer should increase the backlog and recycle the oldest half-open TCP connections.
B. There are signs of a malformed packet attack, and the engineer should limit the packet size and set a threshold of bytes as a countermeasure.
C. There are signs of a DNS attack, and the engineer should hide the BIND version and restrict zone transfers as a countermeasure.
D. There are signs of ARP spoofing, and the engineer should use Static ARP entries and IP address-to-MAC address mappings as a countermeasure.
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-215 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.