Exam Details
Exam Code
:300-215Exam Name
:Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps (CBRFIR)Certification
:CyberOps ProfessionalVendor
:CiscoTotal Questions
:59 Q&AsLast Updated
:Mar 25, 2025
Cisco CyberOps Professional 300-215 Questions & Answers
-
Question 31:
An incident response team is recommending changes after analyzing a recent compromise in which:
a large number of events and logs were involved;
team members were not able to identify the anomalous behavior and escalate it in a timely manner;
several network systems were affected as a result of the latency in detection;
security engineers were able to mitigate the threat and bring systems back to a stable state; and
the issue reoccurred shortly after and systems became unstable again because the correct information was not gathered during the initial identification phase.
Which two recommendations should be made for improving the incident response process? (Choose two.)
A. Formalize reporting requirements and responsibilities to update management and internal stakeholders throughout the incident-handling process effectively.
B. Improve the mitigation phase to ensure causes can be quickly identified, and systems returned to a functioning state.
C. Implement an automated operation to pull systems events/logs and bring them into an organizational context.
D. Allocate additional resources for the containment phase to stabilize systems in a timely manner and reduce an attack's breadth.
E. Modify the incident handling playbook and checklist to ensure alignment and agreement on roles, responsibilities, and steps before an incident occurs.
-
Question 32:
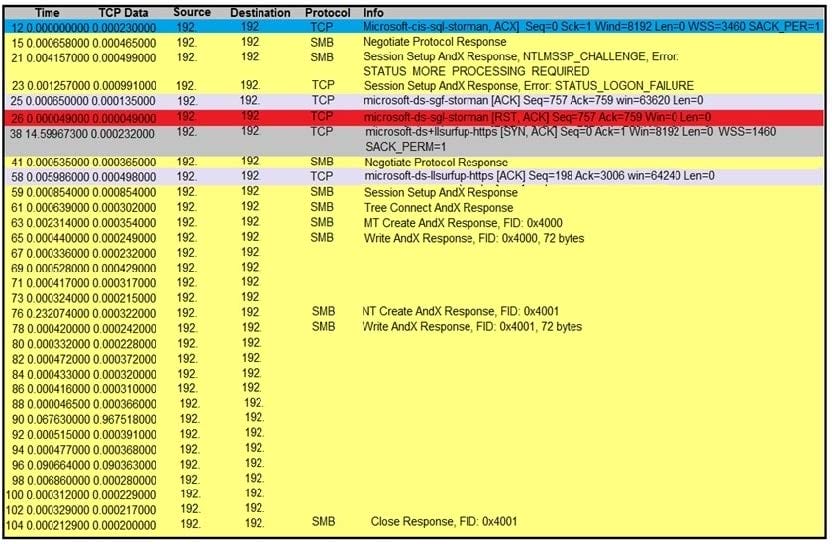
Refer to the exhibit. An engineer is analyzing a TCP stream in a Wireshark after a suspicious email with a URL. What should be determined about the SMB traffic from this stream?
A. It is redirecting to a malicious phishing website,
B. It is exploiting redirect vulnerability C. It is requesting authentication on the user site.
D. It is sharing access to files and printers.
-
Question 33:
What is the goal of an incident response plan?
A. to identify critical systems and resources in an organization
B. to ensure systems are in place to prevent an attack
C. to determine security weaknesses and recommend solutions
D. to contain an attack and prevent it from spreading
-
Question 34:
A security team received an alert of suspicious activity on a user's Internet browser. The user's anti-virus software indicated that the file attempted to create a fake recycle bin folder and connect to an external IP address. Which two actions should be taken by the security analyst with the executable file for further analysis? (Choose two.)
A. Evaluate the process activity in Cisco Umbrella.
B. Analyze the TCP/IP Streams in Cisco Secure Malware Analytics (Threat Grid).
C. Evaluate the behavioral indicators in Cisco Secure Malware Analytics (Threat Grid).
D. Analyze the Magic File type in Cisco Umbrella.
E. Network Exit Localization in Cisco Secure Malware Analytics (Threat Grid).
-
Question 35:
An employee receives an email from a "trusted" person containing a hyperlink that is malvertising. The employee clicks the link and the malware downloads. An information analyst observes an alert at the SIEM and engages the cybersecurity team to conduct an analysis of this incident in accordance with the incident response plan. Which event detail should be included in this root cause analysis?
A. phishing email sent to the victim
B. alarm raised by the SIEM
C. information from the email header
D. alert identified by the cybersecurity team
-
Question 36:

Refer to the exhibit. Which two actions should be taken based on the intelligence information? (Choose two.)
A. Block network access to all .shop domains
B. Add a SIEM rule to alert on connections to identified domains.
C. Use the DNS server to block hole all .shop requests.
D. Block network access to identified domains.
E. Route traffic from identified domains to block hole.
-
Question 37:

Refer to the exhibit. Which two determinations should be made about the attack from the Apache access logs? (Choose two.)
A. The attacker used r57 exploit to elevate their privilege.
B. The attacker uploaded the word press file manager trojan.
C. The attacker performed a brute force attack against word press and used sql injection against the backend database.
D. The attacker used the word press file manager plugin to upoad r57.php.
E. The attacker logged on normally to word press admin page.
-
Question 38:
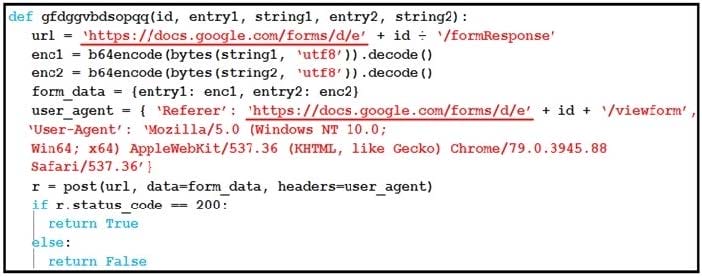
Refer to the exhibit. Which type of code is being used?
A. Shell
B. VBScript
C. BASH
D. Python
-
Question 39:
What is the function of a disassembler?
A. aids performing static malware analysis
B. aids viewing and changing the running state
C. aids transforming symbolic language into machine code
D. aids defining breakpoints in program execution
-
Question 40:
An "unknown error code" is appearing on an ESXi host during authentication. An engineer checks the authentication logs but is unable to identify the issue. Analysis of the vCenter agent logs shows no connectivity errors. What is the next log file the engineer should check to continue troubleshooting this error?
A. /var/log/syslog.log
B. /var/log/vmksummary.log
C. var/log/shell.log
D. var/log/general/log
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-215 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.