Exam Details
Exam Code
:300-215Exam Name
:Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps (CBRFIR)Certification
:CyberOps ProfessionalVendor
:CiscoTotal Questions
:59 Q&AsLast Updated
:Mar 25, 2025
Cisco CyberOps Professional 300-215 Questions & Answers
-
Question 21:
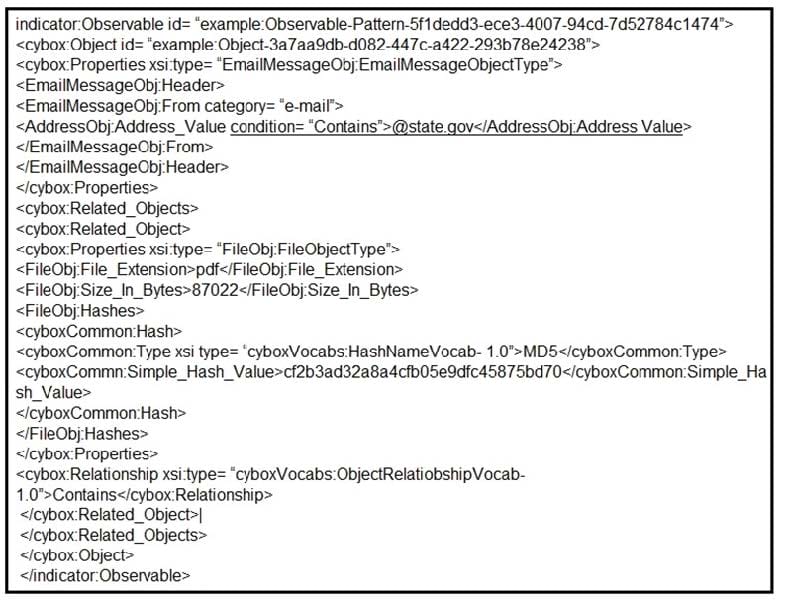
Refer to the exhibit. Which two actions should be taken as a result of this information? (Choose two.)
A. Update the AV to block any file with hash "cf2b3ad32a8a4cfb05e9dfc45875bd70".
B. Block all emails sent from an @state.gov address.
C. Block all emails with pdf attachments.
D. Block emails sent from [email protected] with an attached pdf file with md5 hash "cf2b3ad32a8a4cfb05e9dfc45875bd70".
E. Block all emails with subject containing "cf2b3ad32a8a4cfb05e9dfc45875bd70".
-
Question 22:
Which information is provided bout the object file by the "-h" option in the objdump line command objdump 璪 oasys 璵 vax 環 fu.o?
A. bfdname
B. debugging
C. help
D. headers
-
Question 23:
A threat actor attempts to avoid detection by turning data into a code that shifts numbers to the right four times. Which anti-forensics technique is being used?
A. encryption
B. tunneling
C. obfuscation
D. poisoning
-
Question 24:
Which technique is used to evade detection from security products by executing arbitrary code in the address space of a separate live operation?
A. process injection
B. privilege escalation
C. GPO modification
D. token manipulation
-
Question 25:
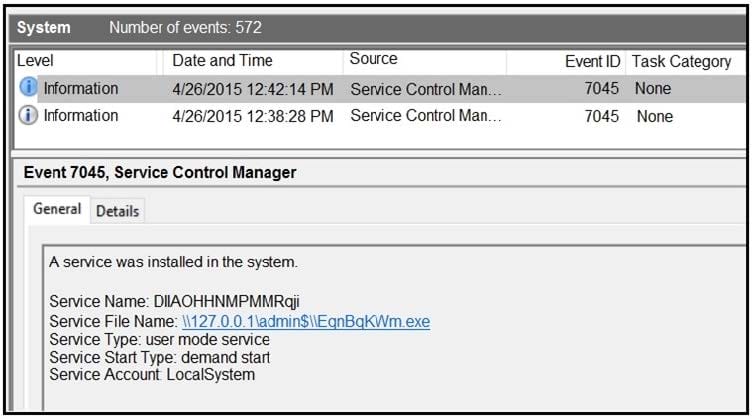
Refer to the exhibit. An HR department submitted a ticket to the IT helpdesk indicating slow performance on an internal share server. The helpdesk engineer checked the server with a real-time monitoring tool and did not notice anything suspicious. After checking the event logs, the engineer noticed an event that occurred 48 hour prior. Which two indicators of compromise should be determined from this information? (Choose two.)
A. unauthorized system modification
B. privilege escalation
C. denial of service attack
D. compromised root access
E. malware outbreak
-
Question 26:
An attacker embedded a macro within a word processing file opened by a user in an organization's legal department. The attacker used this technique to gain access to confidential financial data. Which two recommendations should a security expert make to mitigate this type of attack? (Choose two.)
A. controlled folder access
B. removable device restrictions
C. signed macro requirements
D. firewall rules creation
E. network access control
-
Question 27:
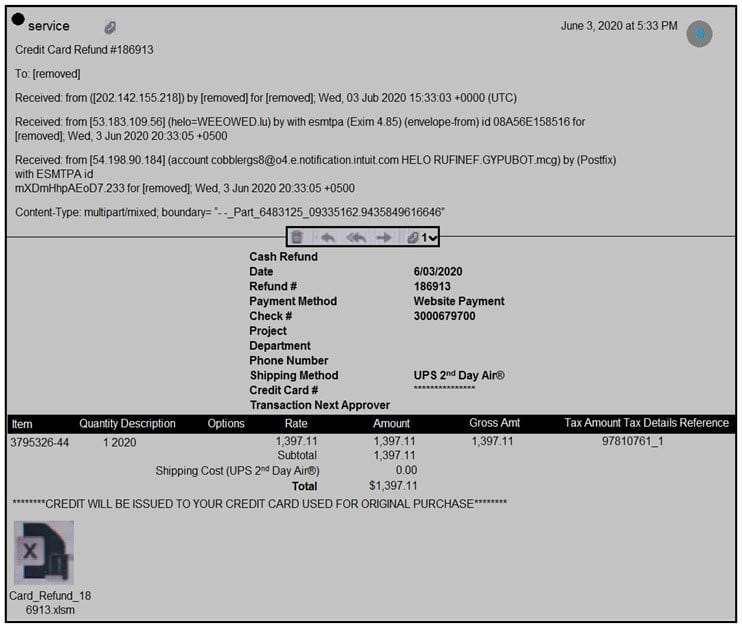
Refer to the exhibit. Which element in this email is an indicator of attack?
A. IP Address: 202.142.155.218
B. content-Type: multipart/mixed
C. attachment: "Card-Refund"
D. subject: "Service Credit Card"
-
Question 28:
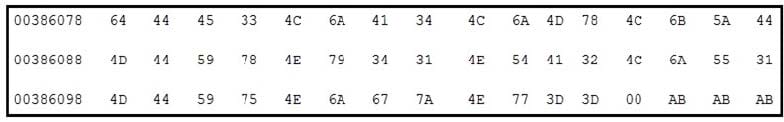
Refer to the exhibit. Which encoding technique is represented by this HEX string?
A. Unicode
B. Binary
C. Base64
D. Charcode
-
Question 29:
A network host is infected with malware by an attacker who uses the host to make calls for files and shuttle traffic to bots. This attack went undetected and resulted in a significant loss. The organization wants to ensure this does not happen in the future and needs a security solution that will generate alerts when command and control communication from an infected device is detected. Which network security solution should be recommended?
A. Cisco Secure Firewall ASA
B. Cisco Secure Firewall Threat Defense (Firepower)
C. Cisco Secure Email Gateway (ESA)
D. Cisco Secure Web Appliance (WSA)
-
Question 30:
What is a use of TCPdump?
A. to analyze IP and other packets
B. to view encrypted data fields
C. to decode user credentials
D. to change IP ports
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-215 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.