Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 801:
A cybersecurity analyst is working with a SIEM tool and reviewing the following table:
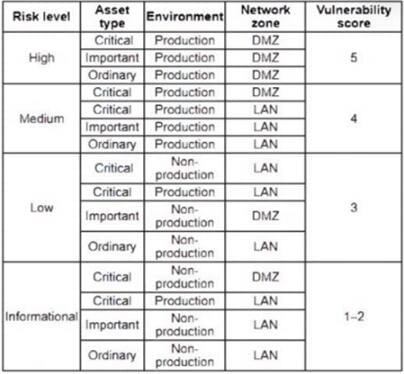
When creating a rule in the company's SIEM, which of the following would be the BEST approach for the analyst to use to assess the risk level of each vulnerability that is discovered by the vulnerability assessment tool?
A. Create a trend with the table and join the trend with the desired rule to be able to extract the risk level of each vulnerability
B. Use Boolean filters in the SIEM rule to take advantage of real-time processing and RAM to store the table dynamically, generate the results faster, and be able to display the table in a dashboard or export it as a report
C. Use a static table stored on the disk of the SIEM system to correlate its data with the data ingested by the vulnerability scanner data collector
D. Use the table as a new index or database for the SIEM to be able to use multisearch and then summarize the results as output
-
Question 802:
An analyst needs to forensically examine a Windows machine that was compromised by a threat actor. Intelligence reports state this specific threat actor is characterized by hiding malicious artifacts, especially with alternate data streams. Based on this intelligence, which of the following BEST explains alternate data streams?
A. A different way data can be streamlined if the user wants to use less memory on a Windows system for forking resources.
B. A way to store data on an external drive attached to a Windows machine that is not readily accessible to users.
C. A Windows attribute that provides for forking resources and is potentially used to hide the presence of secret or malicious files inside the file records of a benign file.
D. A Windows attribute that can be used by attackers to hide malicious files within system memory.
-
Question 803:
A security team is struggling with alert fatigue, and the Chief Information Security Officer has decided to purchase a SOAR platform to alleviate this issue. Which of the following BEST describes how a SOAR platform will help the security team?
A. SOAR will integrate threat intelligence into the alerts, which will help the security team decide which events should be investigated first.
B. A SOAR platform connects the SOC with the asset database, enabling the security team to make informed decisions immediately based on asset criticality.
C. The security team will be able to use the SOAR framework to integrate the SIEM with a TAXII server, which has an automated intelligence feed that will enhance the alert data.
D. Logic can now be created that will allow the SOAR platform to block specific traffic at the firewall according to predefined event triggers and actions.
-
Question 804:
During a company's most recent incident, a vulnerability in custom software was exploited on an externally facing server by an APT. The lessons-learned report noted the following:
The development team used a new software language that was not supported by the security team's automated assessment tools.
During the deployment, the security assessment team was unfamiliar with the new language and struggled to evaluate the software during advanced testing. Therefore, the vulnerability was not detected.
The current IPS did not have effective signatures and policies in place to detect and prevent runtime attacks on the new application.
To allow this new technology to be deployed securely going forward, which of the following will BEST address these findings? (Choose two.)
A. Train the security assessment team to evaluate the new language and verify that best practices for secure coding have been followed
B. Work with the automated assessment-tool vendor to add support for the new language so these vulnerabilities are discovered automatically
C. Contact the human resources department to hire new security team members who are already familiar with the new language
D. Run the software on isolated systems so when they are compromised, the attacker cannot pivot to adjacent systems
E. Instruct only the development team to document the remediation steps for this vulnerability
F. Outsource development and hosting of the applications in the new language to a third-party vendor so the risk is transferred to that provider
-
Question 805:
A digital forensics investigator works from duplicate images to preserve the integrity of the original evidence. Which of the following types of media are MOST volatile and should be preserved? (Choose two.)
A. Memory cache
B. Registry file
C. SSD storage
D. Temporary filesystems
E. Packet decoding
F. Swap volume
-
Question 806:
A security analyst discovers the company's website is vulnerable to cross-site scripting. Which of the following solutions will BEST remedy the vulnerability?
A. Prepared statements
B. Server-side input validation
C. Client-side input encoding
D. Disabled JavaScript filtering
-
Question 807:
A security analyst is reviewing existing email protection mechanisms to generate a report. The analysis finds the following DNS records:
Record 1 v=spf1 ip4:192:168.0.0/16 include:_spf.marketing.com include: thirdpartyprovider.com ~all Record 2
“v=DKIM1\ k=rsa\; p=MIGfMA0GCSqh7d8hyh78Gdg87gd98hag86ga98dhay8gd7ashdca7yg79auhudig7df9ah8g76ag98dhay87ga9”
Record 3 _dmarc.comptia.com TXT v=DMARC1\; p=reject\; pct=100; rua=mailto:[email protected] Which of the following options provides accurate information to be included in the report?
A. Record 3 serves as a reference of the security features configured at Record 1 and 2.
B. Record 1 is used as a blocklist mechanism to filter unauthorized senders.
C. Record 2 is used as a key to encrypt all outbound messages sent.
D. The three records contain private information that should not be disclosed.
-
Question 808:
Which of the following provides an automated approach to checking a system configuration?
A. SCAP
B. CI/CD
C. OVAL
D. Scripting
E. SOAR
-
Question 809:
Which of the following BEST explains the function of a managerial control?
A. To scope the security planning, program development, and maintenance of the security life cycle
B. To guide the development of training, education, security awareness programs, and system maintenance
C. To implement data classification, risk assessments, security control reviews, and contingency planning
D. To ensure tactical design, selection of technology to protect data, logical access reviews, and the implementation of audit trails
-
Question 810:
A security engineer must deploy X 509 certificates to two web servers behind a load balancer. Each web server is configured identically. Which of the following should be done to ensure certificate name mismatch errors do not occur?
A. Create two certificates, each with the same fully qualified domain name, and associate each with the web servers’ real IP addresses on the load balancer.
B. Create one certificate on the load balancer and associate the site with the web servers’ real IP addresses.
C. Create two certificates, each with the same fully qualified domain name, and associate each with a corresponding web server behind the load balancer.
D. Create one certificate and export it to each web server behind the load balancer.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.