Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 811:
An international company is implementing a marketing campaign for a new product and needs a security analyst to perform a threat-hunting process to identify possible threat actors. Which of the following should be the analyst's primary focus?
A. Hacktivists
B. Organized crime
C. Nation-states
D. Insider threats
-
Question 812:
A security analyst discovers a standard user has unauthorized access to the command prompt, PowerShell, and other system utilities. Which of the following is the BEST action for the security analyst to take?
A. Disable the appropriate settings in the administrative template of the Group Policy.
B. Use AppLocker to create a set of whitelist and blacklist rules specific to group membership.
C. Modify the registry keys that correlate with the access settings for the System32 directory.
D. Remove the user's permissions from the various system executables.
-
Question 813:
A security analyst notices the following proxy log entries:
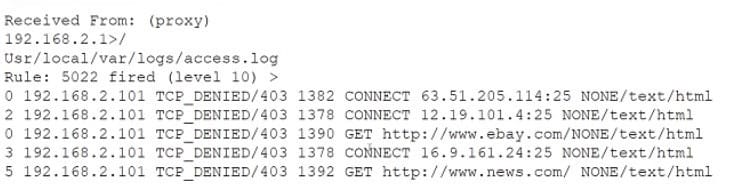
Which of the following is the user attempting to do based on the log entries?
A. Use a DoS attack on external hosts.
B. Exfiltrate data.
C. Scan the network.
D. Relay email.
-
Question 814:
An organization implemented an extensive firewall access-control blocklist to prevent internal network ranges from communicating with a list of IP addresses of known command-and-control domains A security analyst wants to reduce the load on the firewall. Which of the following can the analyst implement to achieve similar protection and reduce the load on the firewall?
A. A DLP system
B. DNS sinkholing
C. IP address allow list
D. An inline IDS
-
Question 815:
A security analyst performs a weekly vulnerability scan on a network that has 240 devices and receives a report with 2.450 pages. Which of the following would most likely decrease the number of false positives?
A. Manual validation
B. Penetration testing
C. A known-environment assessment
D. Credentialed scanning
-
Question 816:
Which of the following software assessment methods world peak times?
A. Security regression testing
B. Stress testing
C. Static analysis testing
D. Dynamic analysis testing
E. User acceptance testing
-
Question 817:
A security analyst is analyzing the following output from the Spider tab of OWASP ZAP after a vulnerability scan was completed:
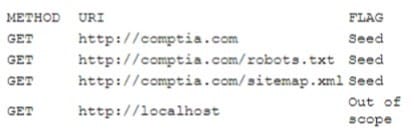
Which of the following options can the analyst conclude based on the provided output?
A. The scanning vendor used robots to make the scanning job faster
B. The scanning job was successfully completed, and no vulnerabilities were detected
C. The scanning job did not successfully complete due to an out of scope error
D. The scanner executed a crawl process to discover pages to be assessed
-
Question 818:
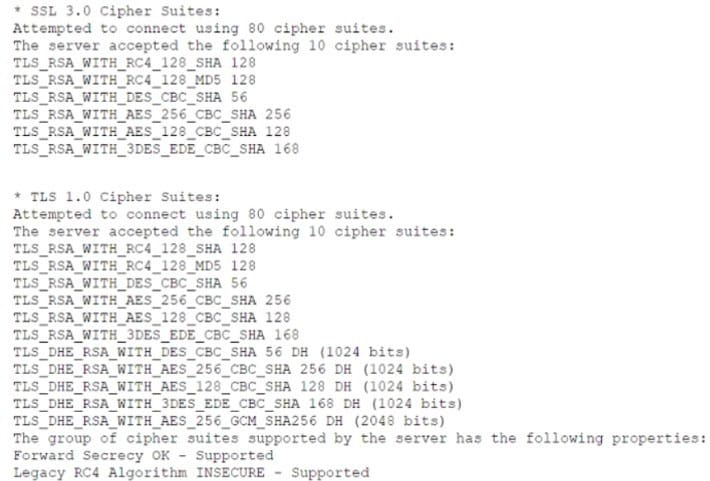
Which of the following lines from this output most likely indicates that attackers could quickly use brute force and determine the negotiated secret session key?
A. TLS_RSA_WITH_DES_CBC_SHA 56
B. TLS_DHE_RSA_WITH_AES_128_CBC_SHA 128 DH (1024 bits)
C. TLS_RSA_WITH_AES_256_CBC_SHA 256
D. TLS_DHE_RSA_WITH_AES_256_GCM_SHA256 DH (2048 bits)
-
Question 819:
Which of the following activities is designed to handle a control failure that leads to a breach?
A. Risk assessment
B. Incident management
C. Root cause analysis
D. Vulnerability management
-
Question 820:
An organization announces that all employees will need to work remotely for an extended period of time. All employees will be provided with a laptop and supported hardware to facilitate this requirement. The organization asks the information security division to reduce the risk during this time. Which of the following is a technical control that will reduce the risk of data loss if a laptop is lost or stolen?
A. Requiring the use of the corporate VPN
B. Requiring the screen to be locked after five minutes of inactivity
C. Requiring the laptop to be locked in a cabinet when not in use
D. Requiring full disk encryption
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.