Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:556 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 331:
A security analyst discovers the following firewall log entries during an incident:
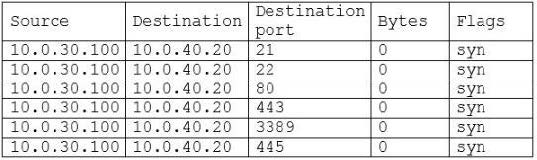
Which of the following is MOST likely occurring?
A. Banner grabbing
B. Port scanning
C. Beaconing
D. Data exfiltration
-
Question 332:
An analyst received an alert regarding an application spawning a suspicious command shell process. Upon further investigation, the analyst observes the following registry change occurring immediately after the suspicious event:
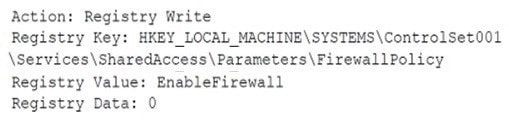
Which of the following was the suspicious event able to accomplish?
A. Impair defenses.
B. Establish persistence.
C. Bypass file access controls.
D. Implement beaconing.
-
Question 333:
An analyst is reviewing the following output:

Vulnerability found: Improper neutralization of script-related HTML tag Which of the following was most likely used to discover this?
A. Reverse engineering using a debugger
B. A static analysis vulnerability scan
C. A passive vulnerability scan
D. A database vulnerability scan
-
Question 334:
During an incident response procedure, a security analyst acquired the needed evidence from the hard drive of a compromised machine. Which of the following actions should the analyst perform NEXT to ensure the data integrity of the evidence?
A. Generate hashes for each file from the hard drive.
B. Create a chain of custody document.
C. Determine a timeline of events using correct time synchronization.
D. Keep the cloned hard drive in a safe place.
-
Question 335:
An organization's Chief Information Security Officer is creating a position that will be responsible for implementing technical controls to protect data, including ensuring backups are properly maintained. Which of the following roles would MOST likely include these responsibilities?
A. Data protection officer
B. Data owner
C. Backup administrator
D. Data custodian
E. Internal auditor
-
Question 336:
A manufacturing company has joined the information sharing and analysis center for its sector. As a benefit, the company will receive structured IoC data contributed by other members. Which of the following best describes the utility of this data?
A. Other members will have visibility into instances of positive IoC identification within the manufacturing company's corporate network.
B. The manufacturing company will have access to relevant malware samples from all other manufacturing sector members.
C. Other members will automatically adjust their security postures to defend the manufacturing company's processes.
D. The manufacturing company can ingest the data and use tools to autogenerate security configurations for all of its infrastructure.
-
Question 337:
A security analyst who works in the SOC receives a new requirement to monitor for indicators of compromise. Which of the following is the first action the analyst should take in this situation?
A. Develop a dashboard to track the indicators of compromise.
B. Develop a query to search for the indicators of compromise.
C. Develop a new signature to alert on the indicators of compromise.
D. Develop a new signature to block the indicators of compromise.
-
Question 338:
A cybersecurity analyst is concerned about attacks that use advanced evasion techniques. Which of the following would best mitigate such attacks?
A. Keeping IPS rules up to date
B. Installing a proxy server
C. Applying network segmentation
D. Updating the antivirus software
-
Question 339:
While reviewing a vulnerability assessment, an analyst notices the following issue is identified in the report:
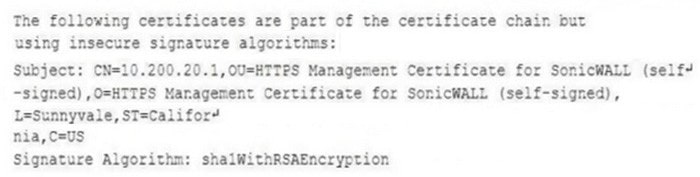
To address this finding, which of the following would be most appropriate for the analyst to recommend to the network engineer?
A. Reconfigure the device to support only connections leveraging TLSv1.2.
B. Obtain a new self-signed certificate and select AES as the hashing algorithm.
C. Replace the existing certificate with a certificate that uses only MDS for signing.
D. Use only signed certificates with cryptographically secure certificate sources.
-
Question 340:
An analyst needs to understand how an attacker compromised a server. Which of the following procedures will best deliver the information that is necessary to reconstruct the steps taken by the attacker?
A. Scan the affected system with an anti-malware tool and check for vulnerabilities with a vulnerability scanner.
B. Extract the server's system timeline, verifying hashes and network connections during a certain time frame.
C. Clone the entire system and deploy it in a network segment built for tests and investigations while monitoring the system during a certain time frame.
D. Clone the server's hard disk and extract all the binary files, comparing hash signatures with malware databases.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.