Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:556 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 351:
Which of the flowing is the best reason why organizations need operational security controls?
A. To supplement areas that other controls cannot address
B. To limit physical access to areas that contain sensitive data
C. To assess compliance automatically against a secure baseline
D. To prevent disclosure by potential insider threats
-
Question 352:
Which of the following ICS network protocols has no inherent security functions on TCP port 502?
A. CIP
B. DHCP
C. SSH
D. Modbus
-
Question 353:
Which of the following weaknesses associated with common SCADA systems are the MOST critical for organizations to address architecturally within their networks? (Choose two.)
A. Boot processes that are neither measured nor attested
B. Legacy and unpatchable systems software
C. Unnecessary open ports and protocols
D. No OS kernel mandatory access controls
E. Unauthenticated commands
F. Insecure filesystem permissions
-
Question 354:
A security analyst receives a report indicating a system was compromised due to malware that was downloaded from the internet using TFTP. The analyst is instructed to block TFTP at the corporate firewall. Given the following portion of the current firewall rule set:
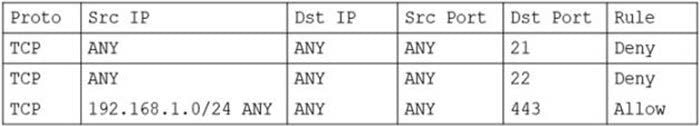
Which of the following rules should be added to accomplish this goal?
A. UDP ANY ANY ANY 20 Deny
B. UDP ANY ANY 69 69 Deny
C. UDP ANY ANY 67 68 Deny
D. UDP ANY ANY ANY 69 Deny
E. UDP ANY ANY ANY 69 Deny
-
Question 355:
A security analyst found the following entry in a server log:

The analyst executed netstat and received the following output:
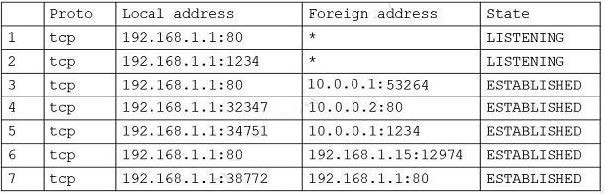
Which of the following lines in the output confirms this was successfully executed by the server?
A. 1
B. 2
C. 3
D. 4
E. 5
F. 6
G. 7
-
Question 356:
A cybersecurity analyst is working with a SIEM tool and reviewing the following table:
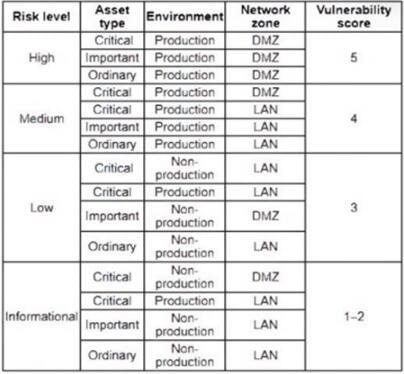
When creating a rule in the company's SIEM, which of the following would be the BEST approach for the analyst to use to assess the risk level of each vulnerability that is discovered by the vulnerability assessment tool?
A. Create a trend with the table and join the trend with the desired rule to be able to extract the risk level of each vulnerability
B. Use Boolean filters in the SIEM rule to take advantage of real-time processing and RAM to store the table dynamically, generate the results faster, and be able to display the table in a dashboard or export it as a report
C. Use a static table stored on the disk of the SIEM system to correlate its data with the data ingested by the vulnerability scanner data collector
D. Use the table as a new index or database for the SIEM to be able to use multisearch and then summarize the results as output
-
Question 357:
A Chief Information Officer wants to implement a BYOD strategy for all company laptops and mobile phones. The Chief Information Security Officer is concerned with ensuring all devices are patched and running some sort of protection against malicious software. Which of the following existing technical controls should a security analyst recommend to BEST meet all the requirements?
A. EDR
B. Port security
C. NAC
D. Segmentation
-
Question 358:
An international company is implementing a marketing campaign for a new product and needs a security analyst to perform a threat-hunting process to identify possible threat actors. Which of the following should be the analyst's primary focus?
A. Hacktivists
B. Organized crime
C. Nation-states
D. Insider threats
-
Question 359:
A security engineer must deploy X 509 certificates to two web servers behind a load balancer. Each web server is configured identically. Which of the following should be done to ensure certificate name mismatch errors do not occur?
A. Create two certificates, each with the same fully qualified domain name, and associate each with the web servers' real IP addresses on the load balancer.
B. Create one certificate on the load balancer and associate the site with the web servers' real IP addresses.
C. Create two certificates, each with the same fully qualified domain name, and associate each with a corresponding web server behind the load balancer.
D. Create one certificate and export it to each web server behind the load balancer.
-
Question 360:
A security analyst is reviewing existing email protection mechanisms to generate a report. The analysis finds the following DNS records:
Record 1
v=spf1 ip4:192:168.0.0/16 include:_spf.marketing.com include: thirdpartyprovider.com ~all
Record 2
"v=DKIM1\ k=rsa\; p=MIGfMA0GCSqh7d8hyh78Gdg87gd98hag86ga98dhay8gd7ashdca7yg79auhudig7df9ah8g76ag98dhay87ga9"
Record 3
_dmarc.comptia.com TXT v=DMARC1\; p=reject\; pct=100; rua=mailto:[email protected]
Which of the following options provides accurate information to be included in the report?
A. Record 3 serves as a reference of the security features configured at Record 1 and 2.
B. Record 1 is used as a blocklist mechanism to filter unauthorized senders.
C. Record 2 is used as a key to encrypt all outbound messages sent.
D. The three records contain private information that should not be disclosed.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.