Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:509 Q&AsLast Updated
:Mar 23, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 431:
The analyst reviews the following endpoint log entry: Which of the following has occurred?
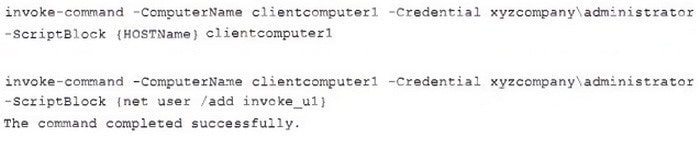
A. Registry change
B. Rename computer
C. New account introduced
D. Privilege escalation
-
Question 432:
A security program was able to achieve a 30% improvement in MTTR by integrating security controls into a SIEM. The analyst no longer had to jump between tools. Which of the following best describes what the security program did?
A. Data enrichment
B. Security control plane
C. Threat feed combination
D. Single pane of glass
-
Question 433:
A technician identifies a vulnerability on a server and applies a software patch. Which of the following should be the next step in the remediation process?
A. Testing
B. Implementation
C. Validation
D. Rollback
-
Question 434:
Which of the following is the first step that should be performed when establishing a disaster recovery plan?
A. Agree on the goals and objectives of the plan
B. Determine the site to be used during a disaster
C. Demonstrate adherence to a standard disaster recovery process
D. Identity applications to be run during a disaster
-
Question 435:
A security alert was triggered when an end user tried to access a website that is not allowed per organizational policy. Since the action is considered a terminable offense, the SOC analyst collects the authentication logs, web logs, and temporary files, reflecting the web searches from the user's workstation, to build the case for the investigation. Which of the following is the best way to ensure that the investigation complies with HR or privacy policies?
A. Create a timeline of events detailinq the date stamps, user account hostname and IP information associated with the activities
B. Ensure that the case details do not reflect any user-identifiable information Password protect the evidence and restrict access to personnel related to the investigation
C. Create a code name for the investigation in the ticketing system so that all personnel with access will not be able to easily identity the case as an HR-related investigation
D. Notify the SOC manager for awareness after confirmation that the activity was intentional
-
Question 436:
Which of the following is the best metric for an organization to focus on given recent investments in SIEM, SOAR, and a ticketing system?
A. Mean time to detect
B. Number of exploits by tactic
C. Alert volume
D. Quantity of intrusion attempts
-
Question 437:
A company is implementing a vulnerability management program and moving from an on-premises environment to a hybrid IaaS cloud environment. Which of the following implications should be considered on the new hybrid environment?
A. The current scanners should be migrated to the cloud
B. Cloud-specific misconfigurations may not be detected by the current scanners
C. Existing vulnerability scanners cannot scan laaS systems
D. Vulnerability scans on cloud environments should be performed from the cloud
-
Question 438:
An incident response team found IoCs in a critical server. The team needs to isolate and collect technical evidence for further investigation. Which of the following pieces of data should be collected first in order to preserve sensitive information before isolating the server?
A. Hard disk
B. Primary boot partition
C. Malicious tiles
D. Routing table
E. Static IP address
-
Question 439:
Which of the following security operations tasks are ideal for automation?
A. Suspicious file analysis: Look for suspicious-looking graphics in a folder. Create subfolders in the original folder based on category of graphics found. Move the suspicious graphics to the appropriate subfolder
B. Firewall IoC block actions: Examine the firewall logs for IoCs from the most recently published zero-day exploit Take mitigating actions in the firewall to block the behavior found in the logs Follow up on any false positives that were caused by the block rules
C. Security application user errors: Search the error logs for signs of users having trouble with the security application Look up the user's phone number Call the user to help with any questions about using the application
D. Email header analysis: Check the email header for a phishing confidence metric greater than or equal to five Add the domain of sender to the block list Move the email to quarantine
-
Question 440:
An organization has experienced a breach of customer transactions. Under the terms of PCI DSS, which of the following groups should the organization report the breach to?
A. PCI Security Standards Council
B. Local law enforcement
C. Federal law enforcement
D. Card issuer
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.