Exam Details
Exam Code
:ECSAV10Exam Name
:EC-Council Certified Security Analyst (ECSA) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:354 Q&AsLast Updated
:Apr 02, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAV10 Questions & Answers
-
Question 261:
A month ago, Jason, a software developer at a reputed IT firm was surfing through his company's website.
He was visiting random pages of the company's website and came to find confidential information about
the company was posted on one of the web pages. Jason forgot to report the issue. Jason contacted John,
another member of the Security Team, and discussed the issue. John visited the page but found nothing
wrong.
What should John do to see past versions and pages of a website that Jason saw one month back?
A. John should use SmartWhois to recover the old pages of the website
B. John should recover cashed pages of the website from Google search engine cache
C. John should run the Web Data Extractor tool to recover the old data
D. John can go to Archive.org to see past versions of the company website
-
Question 262:
HDC Networks Ltd. is a leading security services company. Matthew works as a penetrating tester with this firm. He was asked to gather information about the target company. Matthew begins with social engineering by following the steps:
I. Secretly observes the target to gain critical information
II. Looks at employee's password or PIN code with the help of binoculars or a low-power telescope
Based on the above description, identify the information gathering technique.
A. Phishing
B. Shoulder surfing
C. Tailgating
D. Dumpster diving
-
Question 263:
Analyze the packet capture from Wireshark below and mark the correct statement.
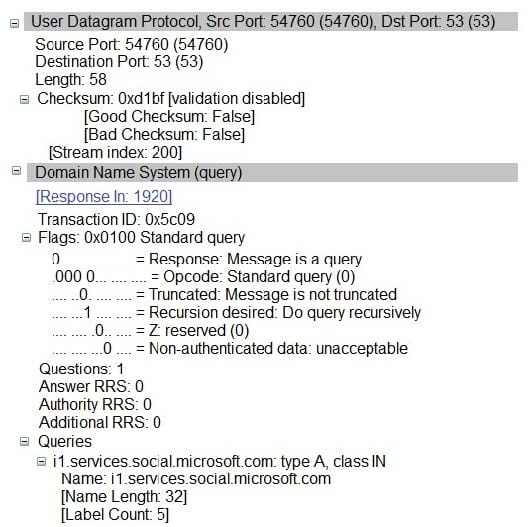
A. It is an invalid DNS query
B. It is a DNS response message
C. It is an answer to the iterative query from Microsoft.com DNS server
D. It is Host (A record) DNS query message
-
Question 264:
Stanley, a pen tester needs to perform various tests to detect SQL injection vulnerabilities. He has to make a list of all input fields whose values could be used in crafting a SQL query. This includes the hidden fields of POST requests and then test them separately, attempting to interfere with the query and cause an error to generate as a result. In which of the following tests is the source code of the application tested in a non-runtime environment to detect the SQL injection vulnerabilities?
A. Dynamic Testing
B. Static Testing
C. Function Testing
D. Source Code Testing
-
Question 265:
During the reconnaissance phase of a penetration test, you discovered that the client has deployed a
firewall that only checks the TCP header information.
Which of the following techniques would you use to bypass the firewall?
A. Bypassing the firewall using tiny fragments
B. Bypassing the firewall by manipulating the IPID sequence number
C. Bypassing the firewall source routing
D. Bypassing the firewall using the IP address in place of an URL
-
Question 266:
Sam is auditing a web application for SQL injection vulnerabilities. During the testing, Sam discovered that
the web application is vulnerable to SQL injection. He starts fuzzing the search field in the web application
with UNION based SQL queries, however, he realized that the underlying WAF is blocking the requests.
To avoid this, Sam is trying the following query:
UNION/**/SELECT/**/'/**/OR/**/1/**/=/**/1
Which of the following evasion techniques is Sam using?
A. Sam is using char encoding to bypass WAF
B. Sam is using obfuscated code to bypass WAF
C. Sam is using inline comments to bypass WAF
D. Sam is manipulating white spaces to bypass WAF
-
Question 267:
David is a penetration tester and he is attempting to extract password hashes from the Oracle database. Which of the following utilities should Dave employ in order to brute-force password hashes from Oracle databases?
A. TNS
B. Orabf
C. Opwg
D. OAT
-
Question 268:
Which of the following tasks is done after submitting the final pen testing report?
A. Kick-off meeting
B. System patching and hardening
C. Exploiting vulnerabilities
D. Mission briefing
-
Question 269:
WallSec Inc. has faced several network security issues in the past and hired Williamson, a professional pentester, to audit its information systems. Before starting his work, Williamson, with the help of his legal advisor, signed an agreement with his client. This agreement states that confidential information of the client should not be revealed outside of the engagement. What is the name of the agreement that Williamson and his client signed?
A. Non-disclosure agreement
B. TPOC agreement
C. Engagement letter
D. Authorization letter
-
Question 270:
Tom is a networking manager in XYZ Inc. He and his team were assigned the task to store and update the confidential files present on a remote server using Network File System (NFS) client-server application protocol. Since the files are confidential, Tom was asked to perform this operation in a secured manner by limiting the access only to his team. As per the instructions provided to him, to use NFS securely, he employed the process of limiting the superuser access privileges only to his team by using authentication based on the team personnel identity. Identify the method employed by Tom for securing access controls in NFS?
A. Root Squashing
B. nosuid
C. noexec
D. Suid
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAV10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.