Exam Details
Exam Code
:ECSAV10Exam Name
:EC-Council Certified Security Analyst (ECSA) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:354 Q&AsLast Updated
:Mar 24, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAV10 Questions & Answers
-
Question 51:
You are carrying out the last round of testing for your new website before it goes live. The website has
many dynamic pages and connects to a SQL backend that accesses your product inventory in a database.
You come across a web security site that recommends inputting the following code into a search field on
web pages to check for vulnerabilities:
When you type this and click on search, you receive a pop-up window that says:
"This is a test."
What is the result of this test?
A. Your website is vulnerable to web bugs
B. Your website is vulnerable to XSS
C. Your website is not vulnerable
D. Your website is vulnerable to SQL injection
-
Question 52:
Which one of the following is a supporting tool for 802.11 (wireless) packet injections, it spoofs 802.11 packets to verify whether the access point is valid or not?
A. Airsnort
B. Aircrack
C. Airpwn
D. WEPCrack
-
Question 53:
A framework for security analysis is composed of a set of instructions, assumptions, and limitations to
analyze and solve security concerns and develop threat free applications.
Which of the following frameworks helps an organization in the evaluation of the company's information
security with that of the industrial standards?
A. Microsoft Internet Security Framework
B. Information System Security Assessment Framework
C. The IBM Security Framework
D. Nortell's Unified Security Framework
-
Question 54:
Choose the correct option to define the Prefix Length.
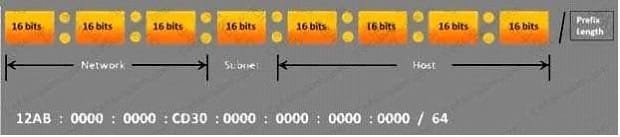
A. Prefix Length = Subnet + Host portions
B. Prefix Length = Network + Host portions
C. Prefix Length = Network + Subnet portions
D. Prefix Length = Network + Subnet + Host portions
-
Question 55:
Frank is working on a vulnerability assessment for a company on the West coast. The company hired Frank to assess its network security through scanning, pen tests, and vulnerability assessments. After discovering numerous known vulnerabilities detected by a temporary IDS he set up, he notices a number of items that show up as unknown but questionable in the logs. He looks up the behavior on the Internet, but cannot find anything related. What organization should Frank submit the log to find out if it is a new vulnerability or not?
A. CVE
B. IANA
C. RIPE
D. APIPA
-
Question 56:
Which of the following statement holds true for TCP Operation?
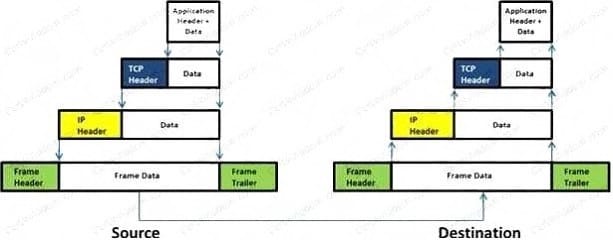
A. Port numbers are used to know which application the receiving host should pass the data to
B. Sequence numbers are used to track the number of packets lost in transmission
C. Flow control shows the trend of a transmitting host overflowing the buffers in the receiving host
D. Data transfer begins even before the connection is established
-
Question 57:
A firewall's decision to forward or reject traffic in network filtering is dependent upon which of the following?
A. Destination address
B. Port numbers
C. Source address
D. Protocol used
-
Question 58:
What is the maximum value of a "tinyint" field in most database systems?
A. 222
B. 224 or more
C. 240 or less
D. 225 or more
-
Question 59:
Firewall is an IP packet filter that enforces the filtering and security policies to the flowing network traffic. Using firewalls in IPv6 is still the best way of protection from low level attacks at the network and transport layers. Which one of the following cannot handle routing protocols properly?
A. "Internet-router-firewall-net architecture"
B. "Internet-firewall-router-net architecture"
C. "Internet-firewall/router(edge device)-net architecture"
D. "Internet-firewall -net architecture"
-
Question 60:
Amazon, an IT based company, conducts a survey on the usage of the Internet. They found that company employees spend most of the time at work surfing the web for their personal use and for inappropriate web site viewing. Management decide to block all such web sites using URL filtering software.
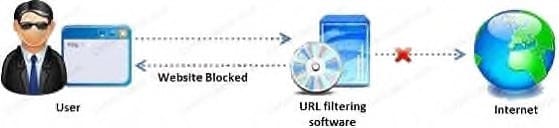
How can employees continue to see the blocked websites?
A. Using session hijacking
B. Using proxy servers
C. Using authentication
D. Using encryption
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAV10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.