Exam Details
Exam Code
:ECSAV10Exam Name
:EC-Council Certified Security Analyst (ECSA) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:354 Q&AsLast Updated
:Mar 24, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAV10 Questions & Answers
-
Question 61:
Logs are the record of the system and network activities. Syslog protocol is used for delivering log information across an IP network. Syslog messages can be sent via which one of the following?
A. UDP and TCP
B. TCP and SMTP
C. SMTP
D. UDP and SMTP
-
Question 62:
In the TCP/IP model, the transport layer is responsible for reliability and flow control from source to the destination. TCP provides the mechanism for flow control by allowing the sending and receiving hosts to communicate. A flow control mechanism avoids the problem with a transmitting host overflowing the buffers in the receiving host.
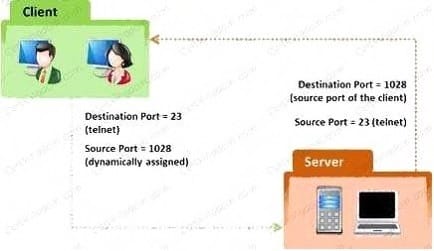
A. Sliding Windows
B. Windowing
C. Positive Acknowledgment with Retransmission (PAR)
D. Synchronization
-
Question 63:
Identify the injection attack represented in the diagram below:
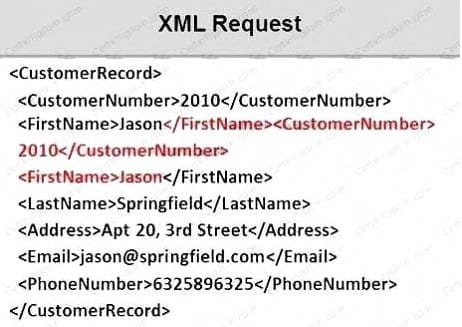
A. XPath Injection Attack
B. XML Request Attack
C. XML Injection Attack
D. Frame Injection Attack
-
Question 64:
War Driving is the act of moving around a specific area, mapping the population of wireless access points
for statistical purposes. These statistics are then used to raise awareness of the security problems
associated with these types of networks.
Which one of the following is a Linux based program that exploits the weak IV (Initialization Vector)
problem documented with static WEP?
A. Airsnort
B. Aircrack
C. WEPCrack
D. Airpwn
-
Question 65:
You are the security analyst working for a private company out of France. Your current assignment is to obtain credit card information from a Swiss bank owned by that company. After initial reconnaissance, you discover that the bank security defenses are very strong and would take too long to penetrate. You decide to get the information by monitoring the traffic between the bank and one of its subsidiaries in London. After monitoring some of the traffic, you see a lot of FTP packets traveling back and forth. You want to sniff the traffic and extract usernames and passwords. What tool could you use to get this information?
A. RaidSniff
B. Snort
C. Ettercap
D. Airsnort
-
Question 66:
What are the 6 core concepts in IT security?
A. Server management, website domains, firewalls, IDS, IPS, and auditing
B. Authentication, authorization, confidentiality, integrity, availability, and non-repudiation
C. Passwords, logins, access controls, restricted domains, configurations, and tunnels
D. Biometrics, cloud security, social engineering, DoS attack, viruses, and Trojans
-
Question 67:
When setting up a wireless network with multiple access points, why is it important to set each access point on a different channel?
A. Avoid cross talk
B. Avoid over-saturation of wireless signals
C. So that the access points will work on different frequencies
D. Multiple access points can be set up on the same channel without any issues
-
Question 68:
A framework is a fundamental structure used to support and resolve complex issues. The framework that delivers an efficient set of technologies in order to develop applications which are more secure in using Internet and Intranet is:
A. Microsoft Internet Security Framework
B. Information System Security Assessment Framework (ISSAF)
C. Bell Labs Network Security Framework
D. The IBM Security Framework
-
Question 69:
Snort, an open source network-based intrusion detection sensor, is the most widely installed NIDS in the world. It can be configured to run in the four modes. Which one of the following modes reads the packets off the network and displays them in a continuous stream on the console (screen)?
A. Packet Sniffer Mode
B. Packet Logger Mode
C. Network Intrusion Detection System Mode
D. Inline Mode
-
Question 70:
Identify the policy that defines the standards for the organizational network connectivity and security standards for computers that are connected in the organizational network.
A. Information-Protection Policy
B. Special-Access Policy
C. Remote-Access Policy
D. Acceptable-Use Policy
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAV10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.