Exam Details
Exam Code
:ECSAv8Exam Name
:EC-Council Certified Security Analyst (ECSA) v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:200 Q&AsLast Updated
:Mar 22, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAv8 Questions & Answers
-
Question 101:
Before performing the penetration testing, there will be a pre-contract discussion with different pen-testers (the team of penetration testers) to gather a quotation to perform pen testing.

Which of the following factors is NOT considered while preparing a price quote to perform pen testing?
A. Total number of employees in the client organization
B. Type of testers involved
C. The budget required
D. Expected time required to finish the project
-
Question 102:
Identify the transition mechanism to deploy IPv6 on the IPv4 network from the following diagram.
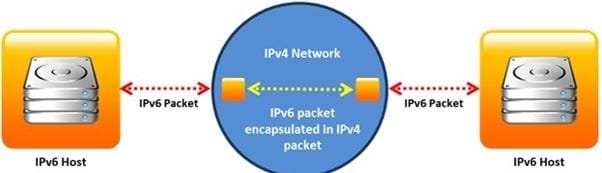
A. Translation
B. Tunneling
C. Dual Stacks
D. Encapsulation
-
Question 103:
John, a penetration tester, was asked for a document that defines the project, specifies goals, objectives, deadlines, the resources required, and the approach of the project. Which of the following includes all of these requirements?
A. Penetration testing project plan
B. Penetration testing software project management plan
C. Penetration testing project scope report
D. Penetration testing schedule plan
-
Question 104:
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.
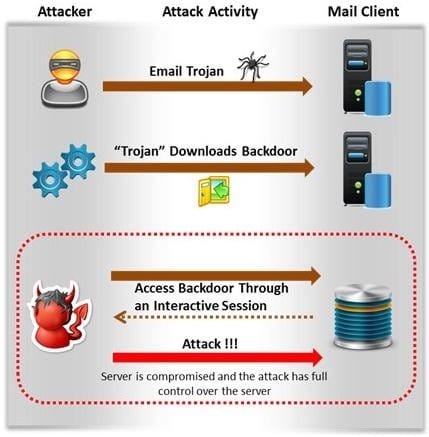
Which of the following techniques do attackers use to create backdoors to covertly gather critical information about a target machine?
A. Internal network mapping to map the internal network of the target machine
B. Port scanning to determine what ports are open or in use on the target machine
C. Sniffing to monitor all the incoming and outgoing network traffic
D. Social engineering and spear phishing attacks to install malicious programs on the target machine
-
Question 105:
Rule of Engagement (ROE) is the formal permission to conduct a pen-test. It provides top- level guidance for conducting the penetration testing. Various factors are considered while preparing the scope of ROE which clearly explain the limits associated with the security test.
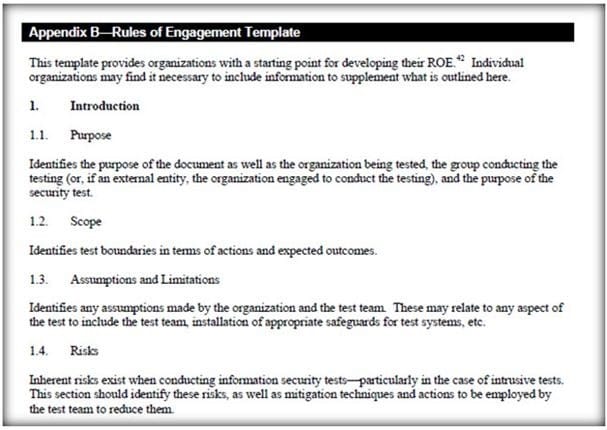
Which of the following factors is NOT considered while preparing the scope of the Rules of Engagment (ROE)?
A. A list of employees in the client organization
B. A list of acceptable testing techniques
C. Specific IP addresses/ranges to be tested
D. Points of contact for the penetration testing team
-
Question 106:
Which of the following protocols cannot be used to filter VoIP traffic?
A. Media Gateway Control Protocol (MGCP)
B. Real-time Transport Control Protocol (RTCP)
C. Session Description Protocol (SDP)
D. Real-Time Publish Subscribe (RTPS)
-
Question 107:
A penetration test consists of three phases: pre-attack phase, attack phase, and post- attack phase.
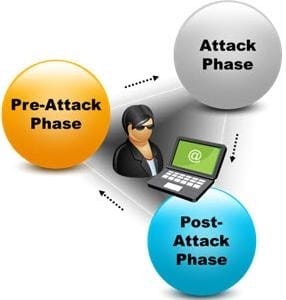
Active reconnaissance which includes activities such as network mapping, web profiling, and perimeter mapping is a part which phase(s)?
A. Post-attack phase
B. Pre-attack phase and attack phase
C. Attack phase
D. Pre-attack phase
-
Question 108:
What are placeholders (or markers) in an HTML document that the web server will dynamically replace with data just before sending the requested documents to a browser?
A. Server Side Includes
B. Sort Server Includes
C. Server Sort Includes
D. Slide Server Includes
-
Question 109:
Which of the following is NOT related to the Internal Security Assessment penetration testing strategy?
A. Testing to provide a more complete view of site security
B. Testing focused on the servers, infrastructure, and the underlying software, including the target
C. Testing including tiers and DMZs within the environment, the corporate network, or partner company connections
D. Testing performed from a number of network access points representing each logical and physical segment
-
Question 110:
Black-box testing is a method of software testing that examines the functionality of an application (e.g. what the software does) without peering into its internal structures or workings. Black-box testing is used to detect issues in SQL statements and to detect SQL injection vulnerabilities.
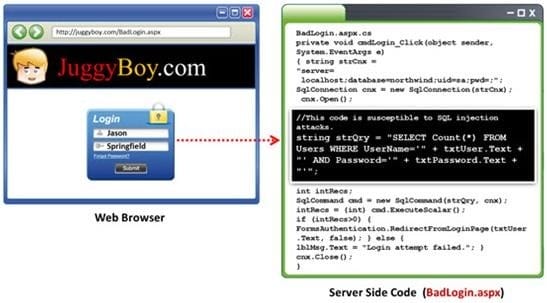
Most commonly, SQL injection vulnerabilities are a result of coding vulnerabilities during the Implementation/Development phase and will likely require code changes.
Pen testers need to perform this testing during the development phase to find and fix the SQL injection vulnerability.
What can a pen tester do to detect input sanitization issues?
A. Send single quotes as the input data to catch instances where the user input is not sanitized
B. Send double quotes as the input data to catch instances where the user input is not sanitized
C. Send long strings of junk data, just as you would send strings to detect buffer overruns
D. Use a right square bracket (the "]" character) as the input data to catch instances where the user input is used as part of a SQL identifier without any input sanitization
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAv8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.