Exam Details
Exam Code
:ECSAv8Exam Name
:EC-Council Certified Security Analyst (ECSA) v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:200 Q&AsLast Updated
:
EC-COUNCIL EC-COUNCIL Certifications ECSAv8 Questions & Answers
-
Question 111:
Phishing is typically carried out by email spoofing or instant messaging and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one.
Phishing is an example of social engineering techniques used to deceive users, and exploits the poor usability of current web security technologies. Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical security measures.
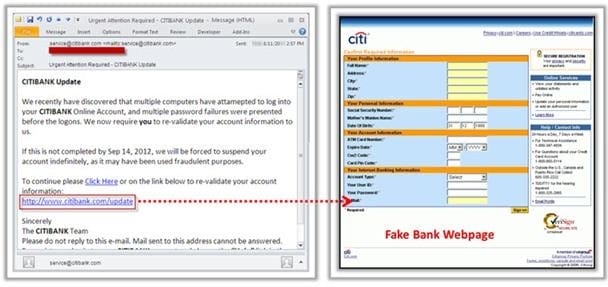
What characteristics do phishing messages often have that may make them identifiable?
A. Invalid email signatures or contact information
B. Suspiciously good grammar and capitalization
C. They trigger warning pop-ups
D. Suspicious attachments
-
Question 112:
Which of the following are the default ports used by NetBIOS service?
A. 135, 136, 139, 445
B. 134, 135, 136, 137
C. 137, 138, 139, 140
D. 133, 134, 139, 142
-
Question 113:
What is the maximum value of a "tinyint" field in most database systems?
A. 222
B. 224 or more
C. 240 or less
D. 225 or more
-
Question 114:
Which of the following policies states that the relevant application owner must authorize requests for additional access to specific business applications in writing to the IT Department/resource?
A. Special-Access Policy
B. User Identification and Password Policy
C. Personal Computer Acceptable Use Policy
D. User-Account Policy
-
Question 115:
Which of the following contents of a pen testing project plan addresses the strengths, weaknesses, opportunities, and threats involved in the project?
A. Project Goal
B. Success Factors
C. Objectives
D. Assumptions
-
Question 116:
In a TCP packet filtering firewall, traffic is filtered based on specified session rules, such as when a session is initiated by a recognized computer.
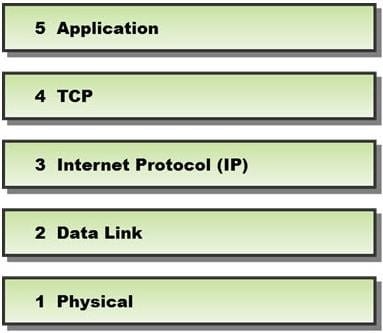
Identify the level up to which the unknown traffic is allowed into the network stack.
A. Level 5 ?Application
B. Level 2 ?Data Link
C. Level 4 ?TCP
D. Level 3 ?Internet Protocol (IP)
-
Question 117:
Which of the following is the objective of Gramm-Leach-Bliley Act?
A. To ease the transfer of financial information between institutions and banks
B. To protect the confidentiality, integrity, and availability of data
C. To set a new or enhanced standards for all U.S. public company boards, management and public accounting firms
D. To certify the accuracy of the reported financial statement
-
Question 118:
A penetration test will show you the vulnerabilities in the target system and the risks associated with it. An educated valuation of the risk will be performed so that the vulnerabilities can be reported as High/ Medium/Low risk issues.
What are the two types of `white-box' penetration testing?
A. Announced testing and blind testing
B. Blind testing and double blind testing
C. Blind testing and unannounced testing
D. Announced testing and unannounced testing
-
Question 119:
Which of the following is not the SQL injection attack character?
A. $
B. PRINT
C. #
D. @@variable
-
Question 120:
Vulnerability assessment is an examination of the ability of a system or application, including the current security procedures and controls, to withstand assault.
What does a vulnerability assessment identify?
A. Disgruntled employees
B. Weaknesses that could be exploited
C. Physical security breaches
D. Organizational structure
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAv8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.