Exam Details
Exam Code
:ECSAv8Exam Name
:EC-Council Certified Security Analyst (ECSA) v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:200 Q&AsLast Updated
:Mar 22, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAv8 Questions & Answers
-
Question 91:
In Linux, /etc/shadow file stores the real password in encrypted format for user's account with added properties associated with the user's password.
In the example of a /etc/shadow file below, what does the bold letter string indicate? Vivek: $1$fnffc$GteyHdicpGOfffXX40w#5:13064:0:99999:7
A. Number of days the user is warned before the expiration date
B. Minimum number of days required between password changes
C. Maximum number of days the password is valid
D. Last password changed
-
Question 92:
What is a difference between host-based intrusion detection systems (HIDS) and network- based intrusion detection systems (NIDS)?
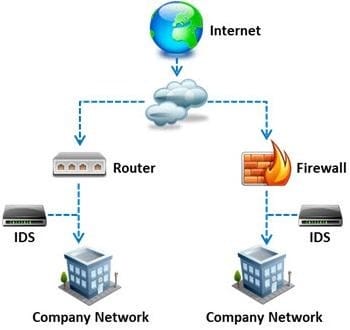
A. NIDS are usually a more expensive solution to implement compared to HIDS.
B. Attempts to install Trojans or backdoors cannot be monitored by a HIDS whereas NIDS can monitor and stop such intrusion events.
C. NIDS are standalone hardware appliances that include network intrusion detection capabilities whereas HIDS consist of software agents installed on individual computers within the system.
D. HIDS requires less administration and training compared to NIDS.
-
Question 93:
Which vulnerability assessment phase describes the scope of the assessment, identifies and ranks the critical assets, and creates proper information protection procedures such as effective planning, scheduling, coordination, and logistics?
A. Threat-Assessment Phase
B. Pre-Assessment Phase
C. Assessment Phase
D. Post-Assessment Phase
-
Question 94:
Which of the following policies helps secure data and protects the privacy of organizational information?
A. Special-Access Policy
B. Document retention Policy
C. Cryptography Policy
D. Personal Security Policy
-
Question 95:
Why is a legal agreement important to have before launching a penetration test?
A. Guarantees your consultant fees
B. Allows you to perform a penetration test without the knowledge and consent of the organization's upper management
C. It establishes the legality of the penetration test by documenting the scope of the project and the consent of the company.
D. It is important to ensure that the target organization has implemented mandatory security policies
-
Question 96:
In which of the following firewalls are the incoming or outgoing packets blocked from accessing services for which there is no proxy?
A. Circuit level firewalls
B. Packet filters firewalls
C. Stateful multilayer inspection firewalls
D. Application level firewalls
-
Question 97:
External penetration testing is a traditional approach to penetration testing and is more focused on the servers, infrastructure and the underlying software comprising the target. It involves a comprehensive analysis of publicly available information about the target, such as Web servers, Mail servers, Firewalls, and Routers.
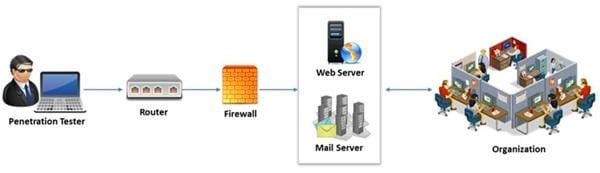
Which of the following types of penetration testing is performed with no prior knowledge of the site?
A. Blue box testing
B. White box testing
C. Grey box testing
D. Black box testing
-
Question 98:
What information can be collected by dumpster diving?
A. Sensitive documents
B. Email messages
C. Customer contact information
D. All the above
-
Question 99:
A WHERE clause in SQL specifies that a SQL Data Manipulation Language (DML) statement should only affect rows that meet specified criteria. The criteria are expressed in the form of predicates. WHERE clauses are not mandatory clauses of SQL DML statements, but can be used to limit the number of rows affected by a SQL DML statement or returned by a query.
A pen tester is trying to gain access to a database by inserting exploited query statements with a WHERE clause. The pen tester wants to retrieve all the entries from the database using the WHERE clause from a particular table (e.g. StudentTable).
What query does he need to write to retrieve the information?
A. EXTRACT* FROM StudentTable WHERE roll_number = 1 order by 1000
B. DUMP * FROM StudentTable WHERE roll_number = 1 AND 1=1-
C. SELECT * FROM StudentTable WHERE roll_number = '' or '1' = '1`
D. RETRIVE * FROM StudentTable WHERE roll_number = 1'#
-
Question 100:
Identify the type of testing that is carried out without giving any information to the employees or administrative head of the organization.
A. Unannounced Testing
B. Double Blind Testing
C. Announced Testing
D. Blind Testing
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAv8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.