Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Apr 15, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 191:
Refer to the exhibit.
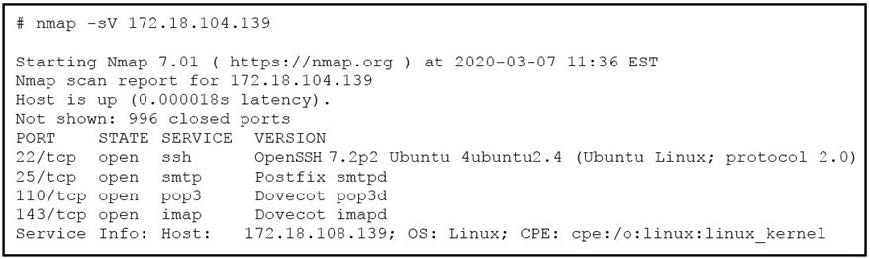
What does the output indicate about the server with the IP address 172.18.104.139?
A. open ports of a web server
B. open port of an FTP server
C. open ports of an email server
D. running processes of the server
-
Question 192:
An engineer received an alert affecting the degraded performance of a critical server. Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
A. Run "ps -d" to decrease the priority state of high load processes to avoid resource exhaustion.
B. Run "ps -u" to find out who executed additional processes that caused a high load on a server.
C. Run "ps -ef" to understand which processes are taking a high amount of resources.
D. Run "ps -m" to capture the existing state of daemons and map required processes to find the gap.
-
Question 193:
Syslog collecting software is installed on the server For the log containment, a disk with FAT type partition is used An engineer determined that log files are being corrupted when the 4 GB tile size is exceeded. Which action resolves the issue?
A. Add space to the existing partition and lower the retention penod.
B. Use FAT32 to exceed the limit of 4 GB.
C. Use the Ext4 partition because it can hold files up to 16 TB.
D. Use NTFS partition for log file containment
-
Question 194:
Refer to the exhibit.
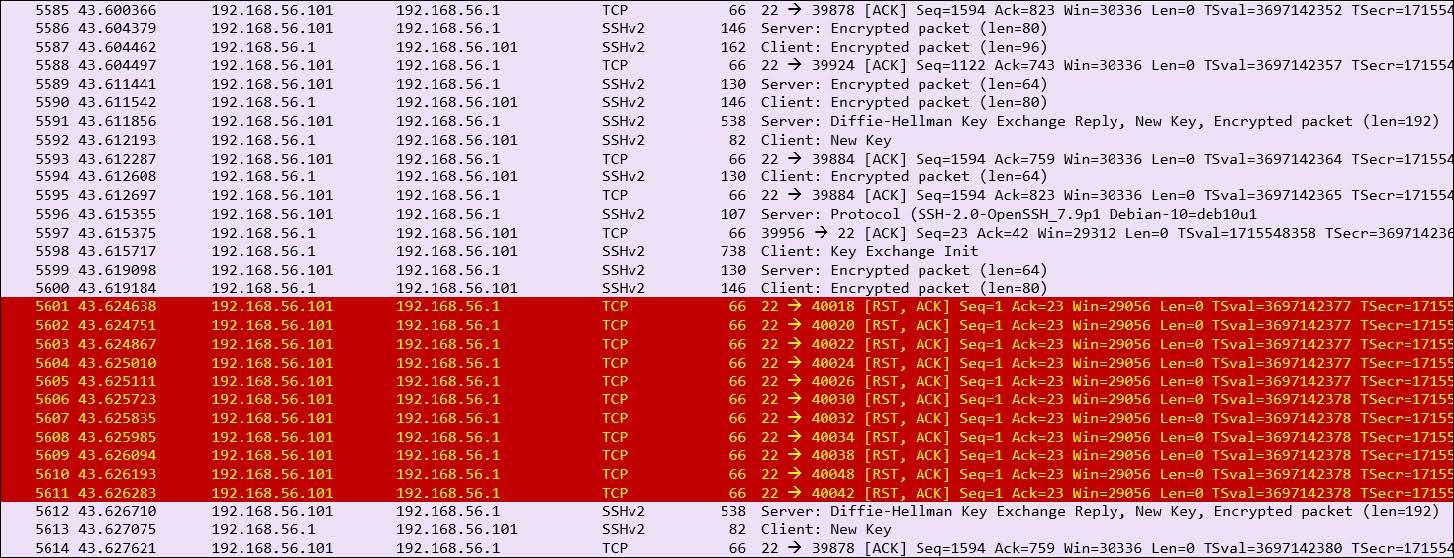
An engineer is analyzing a PCAP file after a recent breach An engineer identified that the attacker used an aggressive ARP scan to scan the hosts and found web and SSH servers. Further analysis showed several SSH Server Banner and Key Exchange Initiations. The engineer cannot see the exact data being transmitted over an encrypted channel and cannot identify how the attacker gained access How did the attacker gain access?
A. by using the buffer overflow in the URL catcher feature for SSH
B. by using an SSH Tectia Server vulnerability to enable host-based authentication
C. by using an SSH vulnerability to silently redirect connections to the local host
D. by using brute force on the SSH service to gain access
-
Question 195:
Refer to the exhibit.
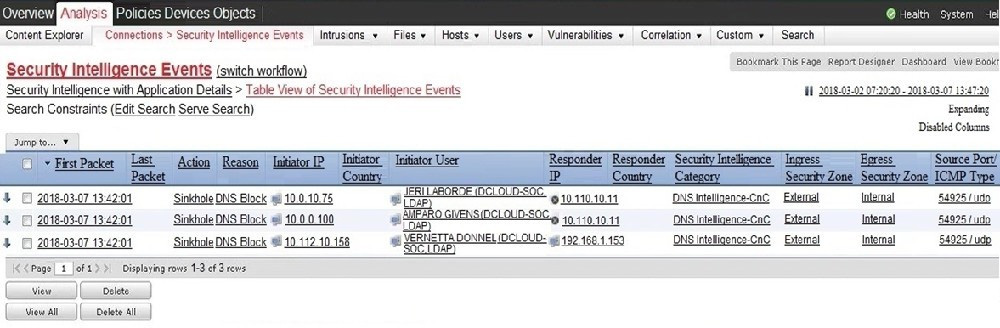
Which two elements in the table are parts of the 5-tuple? (Choose two.)
A. First Packet
B. Initiator User
C. Ingress Security Zone
D. Source Port
E. Initiator IP
-
Question 196:
What is the difference between a threat and an exploit?
A. An exploit is an attack path, and a threat represents a potential vulnerability.
B. An exploit is an attack vector, and a threat is a potential path the attack must go through.
C. A threat is a potential attack on an asset, and an exploit takes advantage of the vulnerability of the asset.
D. A threat is a result of utilizing flow in a system, and an exploit is a result of gaining control over the system.
-
Question 197:
An organization is cooperating with several third-party companies. Data exchange is on an unsecured channel using port 80 Internal employees use the FTP service to upload and download sensitive data An engineer must ensure confidentiality while preserving the integrity of the communication. Which technology must the engineer implement in this scenario'?
A. X 509 certificates
B. RADIUS server
C. CA server
D. web application firewall
-
Question 198:
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group. What is the initial event called in the NIST SP800-61?
A. online assault
B. precursor
C. trigger
D. instigator
-
Question 199:
Refer to the exhibit.
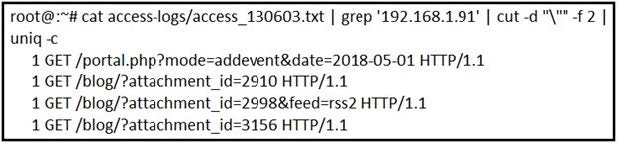
What is depicted in the exhibit?
A. Windows Event logs
B. Apache logs
C. IIS logs
D. UNIX-based syslog
-
Question 200:
Which HTTP header field is used in forensics to identify the type of browser used?
A. referrer
B. host
C. user-agent
D. accept-language
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.