Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Apr 15, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 211:
What is a description of a social engineering attack?
A. fake offer for free music download to trick the user into providing sensitive data
B. package deliberately sent to the wrong receiver to advertise a new product
C. mistakenly received valuable order destined for another person and hidden on purpose
D. email offering last-minute deals on various vacations around the world with a due date and a counter
-
Question 212:
Which piece of information is needed for attribution in an investigation?
A. proxy logs showing the source RFC 1918 IP addresses
B. RDP allowed from the Internet
C. known threat actor behavior
D. 802.1x RADIUS authentication pass arid fail logs
-
Question 213:
What does an attacker use to determine which network ports are listening on a potential target device?
A. man-in-the-middle
B. port scanning
C. SQL injection
D. ping sweep
-
Question 214:
What is personally identifiable information that must be safeguarded from unauthorized access?
A. date of birth
B. driver's license number
C. gender
D. zip code
-
Question 215:
Refer to the exhibit.
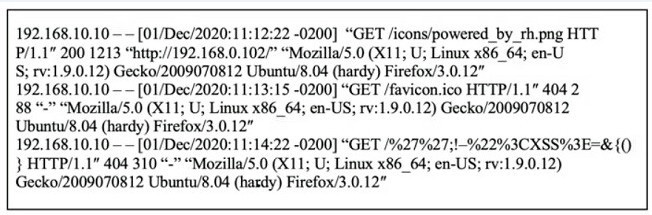
What is occurring within the exhibit?
A. regular GET requests
B. XML External Entities attack
C. insecure deserialization
D. cross-site scripting attack
-
Question 216:
Refer to the exhibit.
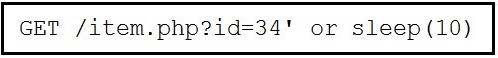
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
A. parameter manipulation
B. heap memory corruption
C. command injection
D. blind SQL injection
-
Question 217:
Which type of verification consists of using tools to compute the message digest of the original and copied data, then comparing the similarity of the digests?
A. evidence collection order
B. data integrity
C. data preservation
D. volatile data collection
-
Question 218:
Which type of access control depends on the job function of the user?
A. discretionary access control
B. nondiscretionary access control
C. role-based access control
D. rule-based access control
-
Question 219:
An analyst is investigating an incident in a SOC environment. Which method is used to identify a session from a group of logs?
A. sequence numbers
B. IP identifier
C. 5-tuple
D. timestamps
-
Question 220:
What is an incident response plan?
A. an organizational approach to events that could lead to asset loss or disruption of operations
B. an organizational approach to security management to ensure a service lifecycle and continuous improvements
C. an organizational approach to disaster recovery and timely restoration of operational services
D. an organizational approach to system backup and data archiving aligned to regulations
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.