Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Apr 15, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 221:
Refer to the exhibit.

Which technology generates this log?
A. NetFlow
B. IDS
C. web proxy
D. firewall
-
Question 222:
Refer to the exhibit.
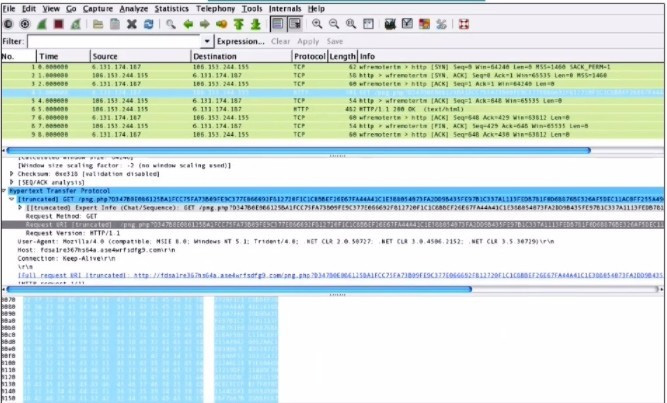
What is shown in this PCAP file?
A. Timestamps are indicated with error.
B. The protocol is TCP.
C. The User-Agent is Mozilla/5.0.
D. The HTTP GET is encoded.
-
Question 223:
Which are two denial-of-service attacks? (Choose two.)
A. TCP connections
B. ping of death
C. man-in-the-middle
D. code-red
E. UDP flooding
-
Question 224:
Which two pieces of information are collected from the IPv4 protocol header? (Choose two.)
A. UDP port to which the traffic is destined
B. TCP port from which the traffic was sourced
C. source IP address of the packet
D. destination IP address of the packet
E. UDP port from which the traffic is sourced
-
Question 225:
Refer to the exhibit.
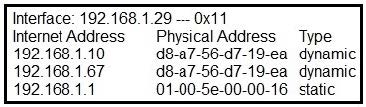
What is occurring in this network?
A. ARP cache poisoning
B. DNS cache poisoning
C. MAC address table overflow
D. MAC flooding attack
-
Question 226:
An engineer must compare NIST vs ISO frameworks The engineer deeded to compare as readable documentation and also to watch a comparison video review. Using Windows 10 OS. the engineer started a browser and searched for a NIST document and then opened a new tab in the same browser and searched for an ISO document for comparison
The engineer tried to watch the video, but there 'was an audio problem with OS so the engineer had to troubleshoot it At first the engineer started CMD and looked fee a driver path then locked for a corresponding registry in the registry editor The engineer enabled "Audiosrv" in task manager and put it on auto start and the problem was solved Which two components of the OS did the engineer touch? (Choose two)
A. permissions
B. PowerShell logs
C. service
D. MBR
E. process and thread
-
Question 227:
What is the difference between deep packet inspection and stateful inspection?
A. Stateful inspection verifies contents at Layer 4. and deep packet inspection verifies connection at Layer 7.
B. Stateful inspection is more secure than deep packet inspection on Layer 7.
C. Deep packet inspection is more secure than stateful inspection on Layer 4.
D. Deep packet inspection allows visibility on Layer 7, and stateful inspection allows visibility on Layer 4.
-
Question 228:
Which type of data consists of connection level, application-specific records generated from network traffic?
A. transaction data
B. location data
C. statistical data
D. alert data
-
Question 229:
Refer to the exhibit.
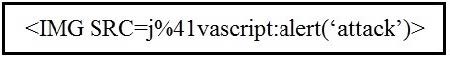
Which kind of attack method is depicted in this string?
A. cross-site scripting
B. man-in-the-middle
C. SQL injection
D. denial of service
-
Question 230:
Which NIST IR category stakeholder is responsible for coordinating incident response among various business units, minimizing damage, and reporting to regulatory agencies?
A. CSIRT
B. PSIRT
C. public affairs
D. management
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.