Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Apr 07, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 311:
A user received a targeted spear-phishing email and identified it as suspicious before opening the content. To which category of the Cyber Kill Chain model does to this type of event belong?
A. weaponization
B. delivery
C. exploitation
D. reconnaissance
-
Question 312:
How does an attack surface differ from an attack vector?
A. An attack vector recognizes the potential outcomes of an attack, and the attack surface is choosing a method of an attack.
B. An attack surface identifies vulnerable parts for an attack, and an attack vector specifies which attacks are feasible to those parts.
C. An attack surface mitigates external vulnerabilities, and an attack vector identifies mitigation techniques and possible workarounds.
D. An attack vector matches components that can be exploited, and an attack surface classifies the potential path for exploitation
-
Question 313:
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
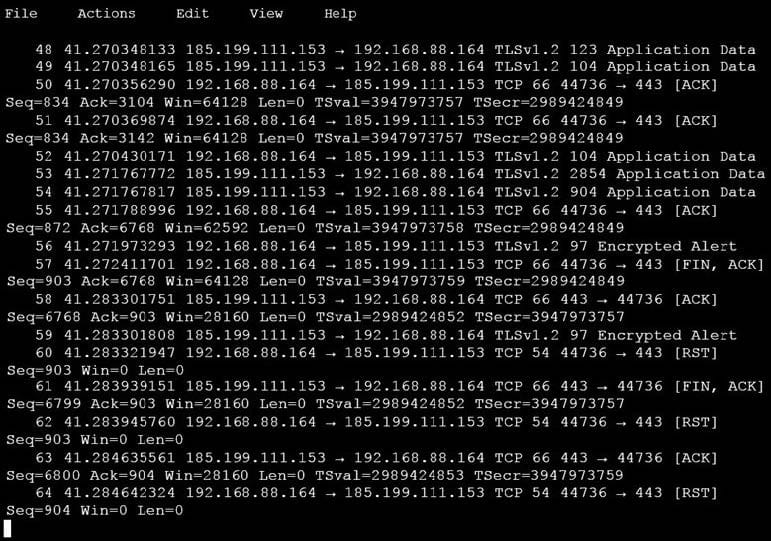
Which obfuscation technique is the attacker using?
A. Base64 encoding
B. TLS encryption
C. SHA-256 hashing
D. ROT13 encryption
-
Question 314:
Which technology on a host is used to isolate a running application from other applications?
A. sandbox
B. application allow list
C. application block list
D. host-based firewall
-
Question 315:
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
A. ransomware communicating after infection
B. users downloading copyrighted content
C. data exfiltration
D. user circumvention of the firewall
-
Question 316:
What is the communication channel established from a compromised machine back to the attacker?
A. man-in-the-middle
B. command and control
C. IDS evasion
D. port scanning
-
Question 317:
What is the role of NAT in data visibility?
A. load balancing
B. hiding IP addresses
C. web filtering
D. encrypting files
-
Question 318:
What is the purpose of command and control for network-aware malware?
A. It controls and shuts down services on the infected host.
B. It helps the malware to profile the host.
C. It contacts a remote server for commands and updates.
D. It takes over the user account for analysis.
-
Question 319:
Which classification of cross-site scripting attack executes the payload without storing it for repeated use?
A. CSRF
B. reflective
C. DOM
D. stored
-
Question 320:
A network engineer noticed in the NetFlow report that internal hosts are sending many DNS requests to external DNS servers. A SOC analyst checked the endpoints and discovered that they are infected and became part of the botnet. Endpoints are sending multiple DNS requests, but with spoofed IP addresses of valid external sources. What kind of attack are infected endpoints involved in?
A. DNS tunneling
B. DNS hijacking
C. DNS amplification
D. DNS flooding
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.