Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Mar 30, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 51:
How does certificate authority impact a security system?
A. It authenticates client identity when requesting SSL certificate
B. It validates domain identity of a SSL certificate
C. It authenticates domain identity when requesting SSL certificate
D. It validates client identity when communicating with the se
-
Question 52:
Which action should be taken if the system is overwhelmed with alerts when false positives and false negatives are compared?
A. Modify the settings of the intrusion detection system.
B. Design criteria for reviewing alerts.
C. Redefine signature rules.
D. Adjust the alerts schedule.
-
Question 53:
Refer to the exhibit.
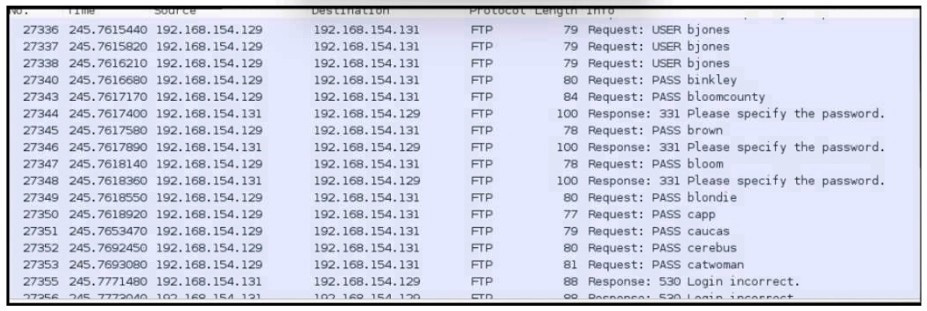
An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server Which display filters should the analyst use to filter the FTP traffic?
A. dstport == FTP
B. tcp.port==21
C. tcpport = FTP
D. dstport = 21
-
Question 54:
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
A. data from a CD copied using Mac-based system
B. data from a CD copied using Linux system
C. data from a DVD copied using Windows system
D. data from a CD copied using Windows
-
Question 55:
Refer to the exhibit.
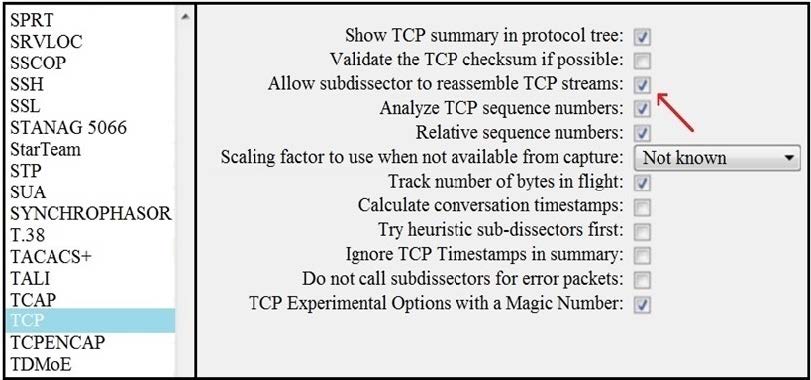
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
A. insert TCP subdissectors
B. extract a file from a packet capture
C. disable TCP streams
D. unfragment TCP
-
Question 56:
Which attack method intercepts traffic on a switched network?
A. denial of service
B. ARP cache poisoning
C. DHCP snooping
D. command and control
-
Question 57:
Refer to the exhibit.
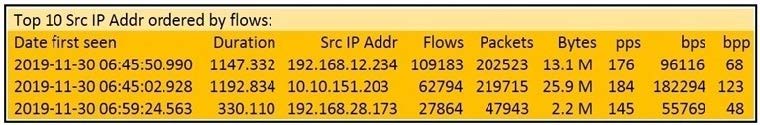
What information is depicted?
A. IIS data
B. NetFlow data
C. network discovery event
D. IPS event data
-
Question 58:
Which information must an organization use to understand the threats currently targeting the organization?
A. threat intelligence
B. risk scores
C. vendor suggestions
D. vulnerability exposure
-
Question 59:
What is a difference between inline traffic interrogation and traffic mirroring?
A. Inline inspection acts on the original traffic data flow
B. Traffic mirroring passes live traffic to a tool for blocking
C. Traffic mirroring inspects live traffic for analysis and mitigation
D. Inline traffic copies packets for analysis and security
-
Question 60:
A company is using several network applications that require high availability and responsiveness, such that milliseconds of latency on network traffic is not acceptable. An engineer needs to analyze the network and identify ways to improve traffic movement to minimize delays. Which information must the engineer obtain for this analysis?
A. total throughput on the interface of the router and NetFlow records
B. output of routing protocol authentication failures and ports used
C. running processes on the applications and their total network usage
D. deep packet captures of each application flow and duration
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.