Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:509 Q&AsLast Updated
:Mar 23, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 21:
Which of the following evidence collection methods is most likely to be acceptable in court cases?
A. Copying all access files at the time of the incident
B. Creating a file-level archive of all files
C. Providing a full system backup inventory
D. Providing a bit-level image of the hard drive
-
Question 22:
A SOC analyst determined that a significant number of the reported alarms could be closed after removing the duplicates. Which of the following could help the analyst reduce the number of alarms with the least effort?
A. SOAR
B. API
C. XDR
D. REST
-
Question 23:
A penetration tester is conducting a test on an organization's software development website. The penetration tester sends the following request to the web interface:
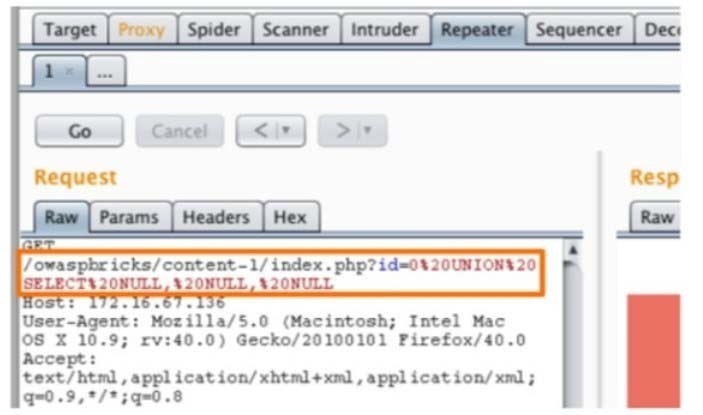
Which of the following exploits is most likely being attempted?
A. SQL injection
B. Local file inclusion
C. Cross-site scripting
D. Directory traversal
-
Question 24:
A vulnerability analyst is writing a report documenting the newest, most critical vulnerabilities identified in the past month. Which of the following public MITRE repositories would be best to review?
A. Cyber Threat Intelligence
B. Common Vulnerabilities and Exposures
C. Cyber Analytics Repository
D. ATTandCK
-
Question 25:
An email hosting provider added a new data center with new public IP addresses. Which of the following most likely needs to be updated to ensure emails from the new data center do not get blocked by spam filters?
A. DKIM
B. SPF
C. SMTP
D. DMARC
-
Question 26:
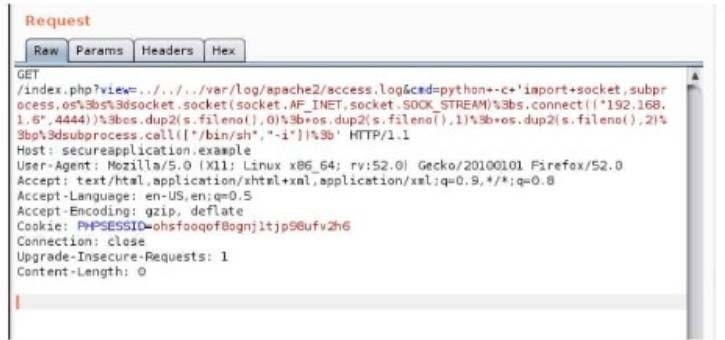
A security analyst is trying to validate the results of a web application scan with Burp Suite.
The security analyst performs the following: Which of the following vulnerabilitles Is the securlty analyst trylng to valldate?
A. SQL injection
B. LFI
C. XSS
D. CSRF
-
Question 27:
Which of the following is the most appropriate action a security analyst to take to effectively identify the most security risks associated with a locally hosted server?
A. Run the operating system update tool to apply patches that are missing.
B. Contract an external penetration tester to attempt a brute-force attack.
C. Download a vendor support agent to validate drivers that are installed.
D. Execute a vulnerability scan against the target host.
-
Question 28:
During a scan of a web server in the perimeter network, a vulnerability was identified that could be exploited over port 3389. The web server is protected by a WAF. Which of the following best represents the change to overall risk associated with this vulnerability?
A. The risk would not change because network firewalls are in use.
B. The risk would decrease because RDP is blocked by the firewall.
C. The risk would decrease because a web application firewall is in place.
D. The risk would increase because the host is external facing.
-
Question 29:
A security analyst has identified a new malware file that has impacted the organization. The malware is polymorphic and has built-in conditional triggers that require a connection to the internet. The CPU has an idle process of at least 70%. Which of the following best describes how the security analyst can effectively review the malware without compromising the organization's network?
A. Utilize an RDP session on an unused workstation to evaluate the malware.
B. Disconnect and utilize an existing infected asset off the network.
C. Create a virtual host for testing on the security analyst workstation.
D. Subscribe to an online service to create a sandbox environment.
-
Question 30:
An analyst reviews a recent government alert on new zero-day threats and finds the following CVE metrics for the most critical of the vulnerabilities:
CVSS: 3.1/AV:N/AC: L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:U/RL:W/RC:R
Which of the following represents the exploit code maturity of this critical vulnerability?
A. E:U
B. S:C
C. RC:R
D. AV:N
E. AC:L
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.